SUNBURST Malware
 SUNBURST is the name of a recent malware threat bearing classic backdoor features. The infection spreads via a prolonged supply-chain attack campaign. Although security researchers have traced the origins of this threat back to March 2020, they have only recently discovered how the threat really works. SUNBURST exploits a security flaw in the update mechanism of SolarWinds’s Orion IT management software. That vulnerability has allowed the actors in charge — currently referred to as "UNC2452" — to "trojanize" Orion's software updates and spread the SUNBURST backdoor payload. In essence, the Sunburst infection runs parallel with Orion’s next update.
SUNBURST is the name of a recent malware threat bearing classic backdoor features. The infection spreads via a prolonged supply-chain attack campaign. Although security researchers have traced the origins of this threat back to March 2020, they have only recently discovered how the threat really works. SUNBURST exploits a security flaw in the update mechanism of SolarWinds’s Orion IT management software. That vulnerability has allowed the actors in charge — currently referred to as "UNC2452" — to "trojanize" Orion's software updates and spread the SUNBURST backdoor payload. In essence, the Sunburst infection runs parallel with Orion’s next update.
Table of Contents
A Highly Popular Infection Vector
Supply chain attacks are subject to a broad appeal in the cybercriminal world because they allow hackers to reach a vast number of potential victims by breaching a single loophole. The SUNBURST Backdoor makes no exception, either. Moreover, it may go unnoticed if network administrators have set SolarWinds Orion to auto-install updates in the background.
According to researchers’ data, Sunburst infections appear to have struck over 2000 computer systems belonging to at least 100 government and non-government agencies across the globe. At present, SUNBURST seems to be hitting entities located in North America, Asia, Europe, and the Middle East.
A Modified .DLL File
To smuggle SUNBURST into a computer network, the actors modify a file called SolarWinds.Orion.Core.BusinessLayer.dll with a file hash of b91ce2fa41029f6955bff20079468448 — a legitimate DLL digitally signed by SolarWinds that allows the software to exchange HTTP-based communication with third-party servers. Next, they inject the SUNBURST-carrying modified DLL into a Microsoft patch file (.msp) associated with the Orion update. Researchers have spotted the trojanized SolarWinds.Orion.Core.BusinessLayer.dll across multiple SolarWinds updates available on the vendor’s website. Here is how a random compromised update file looks like:
hxxps://downloads.solarwinds[.]com/SolarWinds/CatalogResources/Core/2019.4/2019.4.5220.20574/SolarWinds-Core-v2019.4.5220-Hotfix5.msp
Once the update process has finished, SolarWinds loads the malicious DLL via the SolarWinds.BusinessLayerHost.exe. However, SUNBURST doesn't necessarily start operating right at the outset. Instead, the backdoor may remain dormant for up to 14 days before setting the wheels in motion. To do so, SUNBURST connects to an external command-and-control server via a dedicated subdomain named avsvmcloud[dot]com. A successful C&C connection siphons off tons of data through the SolarWinds API. The unauthorized data traffic goes through the so-called Orion Improvement Program (OIP) protocol, a native Orion protocol. By moving laterally across the network, SUNBURST is capable of executing a wide range of malicious functions on the compromised machine including, but not limited to:
- retrieving sensitive information
- manipulating file and registry systems
- gaining unauthorized network access
- executing arbitrary code
- system rebooting and self-termination
The UNC2452 cybergang executes many commands dubbed "Jobs" to perform the tasks mentioned above. Sunburst’s versatile capabilities bring its exploiters an enormous wealth of data relating to the targeted entity — domain name, hostname, username, OS version, and security identifiers (SIDs), to name but a few. And to top it all, Sunburst also keeps logs of MAC Addresses, DHCP Servers, DNSHostName, IPAddress, IPSubnet, DefaultIPGateway, etc.
The actual SUNBURST infection involves multiple steps, all of which are present in the image below.
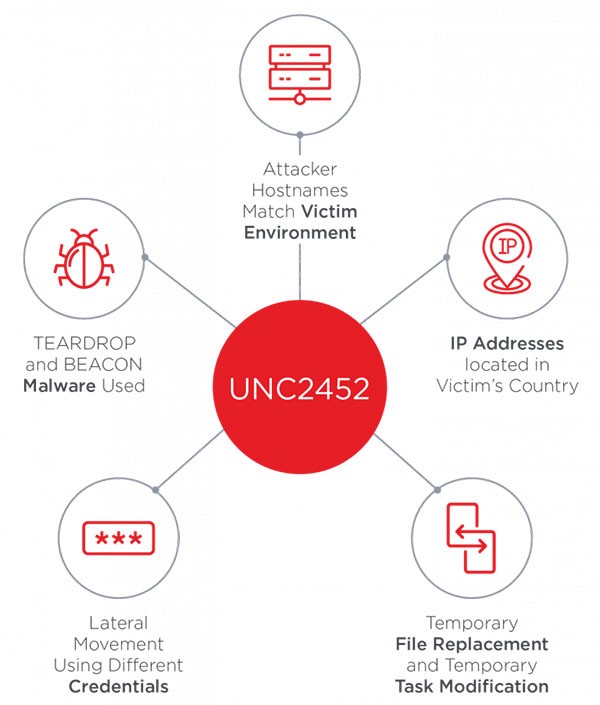
UNC2452 Lateral Movement - Source: Fireeye
In addition to its classic backdoor features, some SUNBURST samples have also injected the Cobalt Strike BEACON malware straight into system memory. The crooks are using Virtual Private Servers to make their IP addresses look as if they came from the victim's country, as well. The login credentials used to obtain unauthorized remote access differ from the ones meant for lateral movement across the infected target. All subsequent malicious actions come to fruition via temporary file replacements — the crooks infect a legitimate file or a system process with malware, use it to trigger the payload, then restore the original file or function.
Overall, whoever stays behind the UNC2452 gang looks prone to remote access execution rather than leaving deep tracks inside the compromised networks.
Sophisticated Evasion Techniques
The UNC2452 actors appear to have gone to great lengths to make the SUNBURST backdoor remarkably resilient to AV detection. On the one hand, the backdoor utilizes numerous obfuscated blocklists to neutralize any running anti-malware solutions. It is also worthy of mention that the crooks even used a Symantec-issued security certificate to hide SUNBURST’s true identity. However, when asked for comment, Symantec clarified that it had sold its certificate authority back in 2018 and underlined that the certificate in question was a legacy one still using the Symantec brand name. And while new certificates may provide an adequate level of protection, old ones may put your online security at risk.
Damage Control
SolarWinds has advised all its users to upgrade their software to Orion Platform release 2020.2.1 HF 1 as this is the version containing the patch for the SUNBURST vulnerability. Infected parties can also follow the vendor's security advisory on neutralizing the backdoor at this location. If you do come across any infection-like symptoms on your SolarWinds Orion software, be sure to either isolate the SolarWinds servers themselves or sever their connection to as many endpoints as possible. Finally, change the login credentials used to access SolarWinds servers and examine the entire network in search of any unusual activity that should otherwise not be taking place.

