SilentSpring Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 8 |
| First Seen: | March 8, 2018 |
| Last Seen: | October 12, 2020 |
| OS(es) Affected: | Windows |
The SilentSpring Ransomware is an encryption ransomware Trojan that PC security researchers observed on March 7, 2018. The SilentSpring Ransomware carries out a typical version of the encryption ransomware tactic, by enciphering the PC user's files and then demanding a ransom payment from the victim in return for the decryption key that should be used to restore the affected files. Computer users must take steps to prevent these attacks since encryption ransomware Trojans are becoming more prevalent increasingly.
Table of Contents
How a Treat Like the SilentSpring Ransomware can Invade a Computer
A threat like the SilentSpring Ransomware may be delivered through the use of corrupted spam email attachments. The most common way of delivering the SilentSpring Ransomware is through the use of damaged DOCX files attached to spam email messages. These DOCX files contain embedded macro scripts that download and install the SilentSpring Ransomware onto the victim's computer. Once the SilentSpring Ransomware is installed on the affected computer, the SilentSpring Ransomware will use the AES encryption to make the victim's files inaccessible. The SilentSpring Ransomware will target the user-generated files, including photos, images, music, videos and various document types. The following are the file types that may be encrypted by the SilentSpring Ransomware during an attack:
.aif, .iff, .m3u, .m4a, .mid, .mp3, .mpa, .wav, .wma, .3g2, .3gp, .asf, .avi, .flv, .m4v, .mov, .mp4, .mpg, .rm, .srt, .swf, .vob, .wmv, .gpx, .kml, .kmz, .asp, .aspx, .cer, .cfm, .csr, .css, .htm, .html, .js, .jsp, .php, .rss, .xhtml, .doc, .docx, .log, .msg, .odt, .pages, .rtf, .tex.
The SilentSpring Ransomware will rename the files encrypted by the attack, adding the file extension '.Sil3nt5pring' to the affected files.
The SilentSpring Ransomware’s Ransom Note
The SilentSpring Ransomware will deliver a ransom note to the computer. The SilentSpring Ransomware is used to target computer users in Russian speaking regions. The SilentSpring Ransomware s attack uses a ransom note written in Russian since most victims of the attack are located in Russia. The following is the text of the SilentSpring Ransomware's ransom note:
'Ашыпъкьа Яvиsowшvяе!!!
Страница, которую вы искали в этом блоге, не существует.
Перейдите на “Введение” или используйте вкладку “Список”.
Do not understand Russian? Well then, click to this picture.'
The translation of the SilentSpring Ransomware ransom note into English reads:
'Attack Ransomware!!!
The page you were looking for in this blog does not exist.
Go to "Introduction" or use the "List" tab.
Do not understand Russian? Well then, click to this picture.'
The SilentSpring Ransomware seems to target small businesses, online websites and individual blogs specifically. It is possible that either the SilentSpring Ransomware is in a testing phase or it is not designed to help victims recover their files since there is no way to contact its perpetrators or demand a ransom payment.
Dealing with a SilentSpring Ransomware Infection
The SilentSpring Ransomware may be associated with a RaaS (Ransomware as a Service) campaign. Because there is a marked increase in attacks involving these infections, it is required that computer users take steps to protect their data. The most effectual protection from these infections is to use a backup system stored on a removable device or the cloud. This allows computer users to recover their files from the backup copy after the SilentSpring Ransomware has compromised their files. Apart from file backups, they should have a security program that is fully up-to-date running all the time. A security program can intercept a SilentSpring Ransomware infection and prevent the ransomware Trojan from being installed in the first place. Since these threats are commonly distributed using spam email messages, learning to recognize these hoaxes is essential in preventing the SilentSpring Ransomware and similar threats distributed in a homologous manner.
SpyHunter Detects & Remove SilentSpring Ransomware
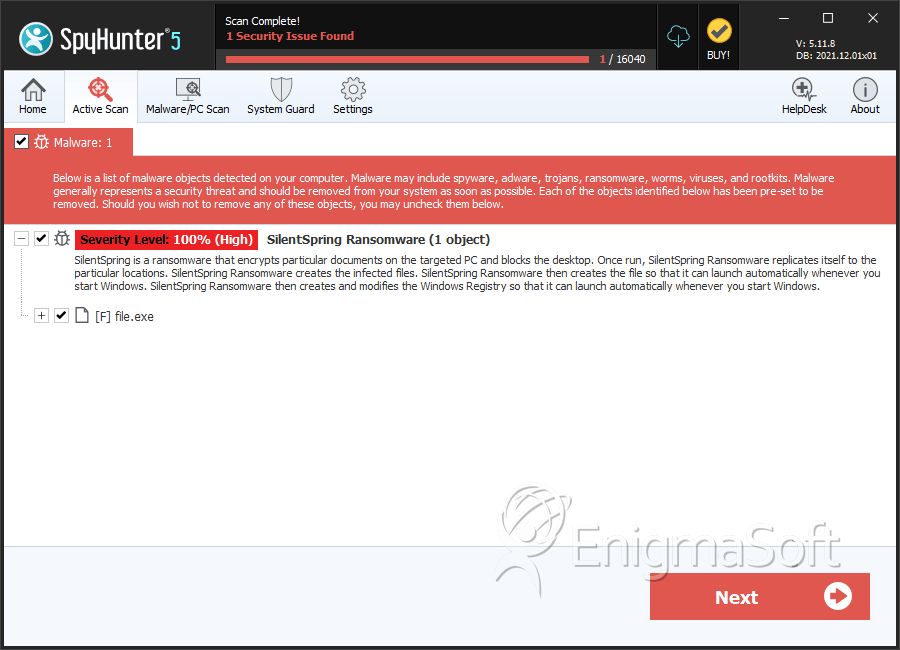
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | aa1101d3c7afdb51d8520ead1e690c9a | 4 |

