Silenced Ransomware
Silenced Ransomware Image
Malware researchers have spotted yet another file-encrypting Trojan recently. Nowadays, it would seem that everyone wants a piece of the pie when it comes to ransomware threats. It appears that they are perceived as an easy way to make some money quickly without too much risk of getting caught or suffering from any consequences.
The Silenced Ransomware was first discovered by the security researcher known on Twitter as 'Jack' or @malwareforme. Much like other threats of this kind, it is made to encrypt data and to rename all affected files to block access for their users. The ransomware adds the '.try' extension to all modified files. Files can be recovered by decryption, something the cybercriminals offer in exchange for the ransom they demand from the victims. The Silenced Ransomware changes the victim's wallpaper, replacing it with an image filled with ransom payment instructions.
Table of Contents
Propagation and Encryption
It is not clear what are the infections vectors employed in the spreading of the Silenced Ransomware. Some researchers venture that the creators of the Silenced Ransomware may have used the most common techniques for propagating threats of this type – spam emails containing macro-laced attachments, fake software updates, and bogus pirated copies of popular applications. As soon as the Silenced Ransomware infects a system, a scan will be performed. The goal of this activity is to determine the locations of the files, which are of interest to the Silenced Ransomware. When this is completed, the Silenced Ransomware will start its encryption process and lock all the targeted files. Then, you will notice that the names of all the files, which have been encrypted, have been changed. The Silenced Ransomware adds a ‘.try’ extension to the affected files. For example, an audio file you had named ‘nbg.mp3’ originally, will be renamed to ‘nbg.mp3.try’ after the encryption process is completed.
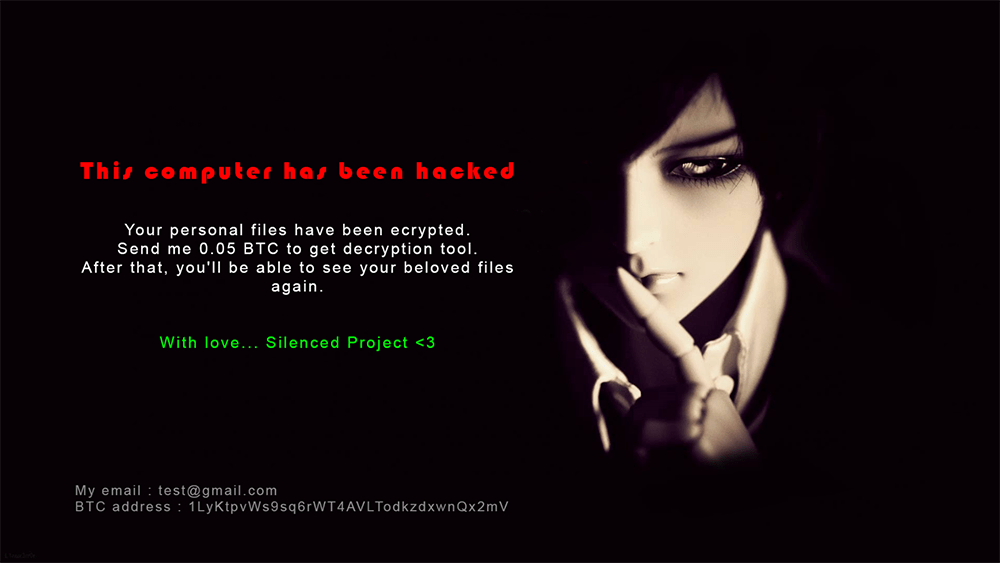
The Ransom Note
In the next step of the attack, the Silenced Ransomware will drop a ransom note. The note consists of a brief message and an image of an eerie ball-jointed doll. It would appear that the Silenced Ransomware is still an unfinished project because its creators have not yet added a real email address as a contact but have instead typed 'test@gmail.com.'
The Silenced Ransomware asks for a payment of 0.05 Bitcoin, paid to a provided Bitcoin wallet address. Victims are also given a method of contacting the people acting behind Silenced by providing them with the email address test@gmail.com. Given the email address, it goes to show the ransomware is likely still in a development stage. Most of the ransomware of this kind will use cryptographic algorithms such as AES, making it difficult to decrypt the data without the proper tools or decryption key.
Certain times the only people with the decryption key are the developers of such threats, meaning they will not send them unless they are paid. The ransom part of the threat is where the victims are given a binary choice – either pay the ransom and trust the developers at their word or not. There is no guarantee that users will receive anything after they send payments, so users are advised to avoid any money transfer. Sticking to regular data backups either on a cloud basis or on physical drives allows avoiding most of the issues.
The test version of the Silenced Ransomware seems to be targeting files specifically located on the desktop, Music, Pictures, and Documents subfolders of %USERPROFILE%\. More directories may be added to the malware, so users should keep that in mind in case they want to check for more encrypted files. The Silenced Ransomware also creates a copy of itself in %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup, and it also creates a Windows Registry entry connected to it. That allows the ransomware to relaunch itself even after a system reboot with no issues.
To avoid becoming a victim of a threat like the Silenced Ransomware, you should make sure to maintain all your applications up to date. Also, having a reputable anti-malware tool installed is crucial for the security of your system.


