Scarab-Cybergod Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 20 |
| First Seen: | August 22, 2018 |
| Last Seen: | April 1, 2019 |
| OS(es) Affected: | Windows |
The Scarab-Cybergod Ransomware is an encryption ransomware Trojan that is part of the Scarab family of ransomware. The Scarab-Cybergod Ransomware poses a real threat to computer users' data, and preemptive steps should be taken to halt the Scarab-Cybergod Ransomware attacks. The Scarab-Cybergod Ransomware was first observed in August 20, 2018, and is part of a wave of Scarab Ransomware variants released in the late Spring and Summer of 2018, associated with a RaaS (Ransomware as a Service) platform possibly.
Table of Contents
How the Scarab-Cybergod Ransomware Attacks a Computer
The Scarab-Cybergod Ransomware uses the AES encryption to make the victim's files inaccessible. The Scarab-Cybergod Ransomware, to mark the files it encrypts, adds the file extension '.CYBERGOD' to the file's name. The most common way in which criminals deliver threats like the Scarab-Cybergod Ransomware to victims is through the use of corrupted email attachments, often containing embedded macro scripts to download and install the Scarab-Cybergod Ransomware onto the victim's computer. Once the Scarab-Cybergod Ransomware is installed, it scans the victim's computer for the user-generated files, generally looking for a wide variety of file types that may include media files, numerous types of documents, databases and various other file types. The following are examples of the files that threats like the Scarab-Cybergod Ransomware encrypt in these attacks:
.ebd, .jbc, .pst, .ost, .tib, .tbk, .bak, .bac, .abk, .as4, .asd, .ashbak, .backup, .bck, .bdb, .bk1, .bkc, .bkf, .bkp, .boe, .bpa, .bpd, .bup, .cmb, .fbf, .fbw, .fh, .ful, .gho, .ipd, .nb7, .nba, .nbd, .nbf, .nbi, .nbu, .nco, .oeb, .old, .qic, .sn1, .sn2, .sna, .spi, .stg, .uci, .win, .xbk, .iso, .htm, .html, .mht, .p7, .p7c, .pem, .sgn, .sec, .cer, .csr, .djvu, .der, .stl, .crt, .p7b, .pfx, .fb, .fb2, .tif, .tiff, .pdf, .doc, .docx, .docm, .rtf, .xls, .xlsx, .xlsm, .ppt, .pptx, .ppsx, .txt, .cdr, .jpe, .jpg, .jpeg, .png, .bmp, .jiff, .jpf, .ply, .pov, .raw, .cf, .cfn, .tbn, .xcf, .xof, .key, .eml, .tbb, .dwf, .egg, .fc2, .fcz, .fg, .fp3, .pab, .oab, .psd, .psb, .pcx, .dwg, .dws, .dxe, .zip, .zipx, .7z, .rar, .rev, .afp, .bfa, .bpk, .bsk, .enc, .rzk, .rzx, .sef, .shy, .snk, .accdb, .ldf, .accdc, .adp, .dbc, .dbx, .dbf, .dbt, .dxl, .edb, .eql, .mdb, .mxl, .mdf, .sql, .sqlite, .sqlite3, .sqlitedb, .kdb, .kdbx, .1cd, .dt, .erf, .lgp, .md, .epf, .efb, .eis, .efn, .emd, .emr, .end, .eog, .erb, .ebn, .ebb, .prefab, .jif, .wor, .csv, .msg, .msf, .kwm, .pwm, .ai, .eps, .abd, .repx, .oxps, .dot.
The Scarab-Cybergod Ransomware delivers a ransom note in the form of a text file named 'From Jobe Smith.TXT' after encrypting the victim's files and renaming them (encrypting the file names and adding the aforementioned file extension to each affected file's name). This ransom note contains the following message and is dropped on the infected computer's desktop:
'I am The Lawnmower Man!
And i can make you forget everything you got here!
Or you can make offer for me on my mail:
localgreenskeeper@firemail.cc or jobesmith@airmail.cc
To show you my almighty power I can decrypt few files for you
But dont forget to send me your ID!
Have a nice day!
+++++
Your ID
[512 random characters]'
The recommendation from PC security researchers is to refrain from following the instructions contained in the Scarab-Cybergod Ransomware ransom note.
Dealing with Threats Like the Scarab-Cybergod Ransomware
The best protection against threats like the Scarab-Cybergod Ransomware is to have file backups. Having file backups ensures that computer users can restore their data after a Scarab-Cybergod Ransomware infection. Apart from file backups, a reliable anti-malware program should be present to protect their PCs from intruders. Since the Scarab-Cybergod Ransomware is distributed through spam email scams and corrupted email attachments mostly, it is imperative that computer users learn to recognize these tactics and respond to this content type appropriately.
SpyHunter Detects & Remove Scarab-Cybergod Ransomware
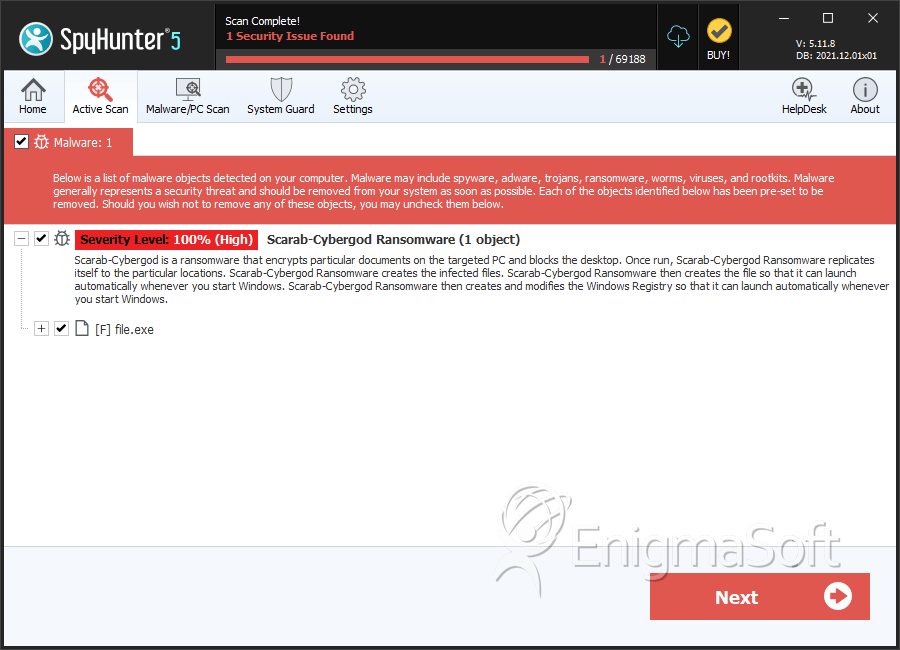
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 0a8cde16e7995a176c668e1f9115307f | 0 |
| 2. | file.exe | 823fa6d6aae4343612d208d6e2fc27a2 | 0 |

