SaveTheQueen Ransomware
SaveTheQueen Ransomware Image
Some cyber crooks are rather inventive when it comes to ticking unknowing users. Malware researchers have detected cyber crooks that pose as a group of highly-skilled individuals who claim to not only take part in malicious campaigns against high-profile targets alongside infamous APTs (Advanced Persistent Threat) recently but that they also are capable of decrypting any ransomware threat. Of course, this is nonsense, and these shady individuals are exaggerating their capabilities greatly and outright lying about their experience. The hacking group in question is called ‘Malicioussecurityservices.’ Not only are they not nearly as skilled as they present themselves to be, but there also is absolutely no way for them to decrypt any locked files unless they have a matching decryption key. The Malicioussecurityservices hacking group also has posted on their twitter account an announcement about a supposed ransomware threat that they will release, which will be targeting large corporations. They state that the data-locking Trojan will be called ‘SaveTheQueen Ransomware’ and will be a ‘Christmas gift for big companies.’
Propagation and Encryption
Despite all the bluffing from the Malicioussecurityservices group, the SaveTheQueen Ransomware actually works as intended. We cannot confirm what propagation method has been used in the spreading of the SaveTheQueen Ransomware. The Malicioussecurityservices group has likely used spam email campaigns as an infection vector to propagate the SaveTheQueen Ransomware. However, there are countless methods that authors of ransomware threats can use to distribute their creations. Regardless of the distribution method, the result is the same; the SaveTheQueen Ransomware will infiltrate your system and look for any files it can find to encrypt. Ransomware threats usually target a very long list of file types, as this would ensure maximum damage to the compromised host. This ransomware threat applies a ‘.SaveTheQueen’ extension at the end of the files it encrypts. This means that a file that you had called ‘pure-energy.jpeg’ originally will be renamed to ‘pure-energy.jpeg.SaveTheQueen’ after the encryption process has been completed.
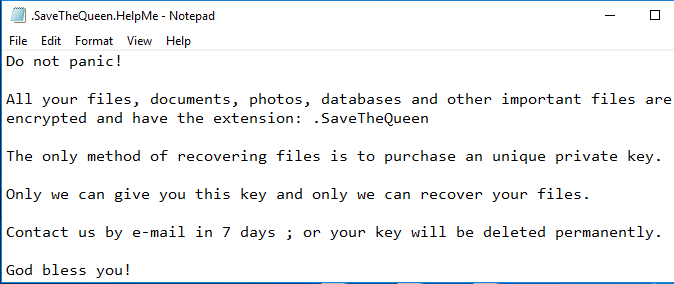
The Ransom Note
The SaveTheQueen Ransomware will drop its ransom message on the user’s desktop. The message can be found in a file called ‘SaveTheQueen.HelpMe.TXT.’ In the note, the attackers do not mention a ransom fee. Do not let this induce you into thinking that they will not demand a payment; the attackers will most certainly ask for a ransom fee, and it is likely to be a hefty sum. Victims are required to contact the attackers via the email - ‘godsaveyou@tuta.io’ and ‘godsaveme@tutamail.com.’
It is never a productive idea to try and cooperate with cybercriminals. They will promise to give you the decryption key you need to unlock your data, but this, more often than not, is a lie. This is why you should consider obtaining a reputable anti-virus solution that will remove the SaveTheQueen Ransomware from your computer safely and will keep your PC secure in the future.

