FakeVimes
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1,759 |
| First Seen: | November 30, 2010 |
| Last Seen: | January 23, 2022 |
| OS(es) Affected: | Windows |
The Rogue:Win32/FakeVimes family of malware is a group of fake security applications that has been prevalent since at least 2009. There are numerous fake security programs belonging to the FakeVimes family, including earlier rogue anti-virus programs like Malware Catcher 2009 and Smart Engine, as well as other Rogue:Win32/FakeVimes clones that include such fake security applications as The presence of malware belonging to the Rogue:Win32/FakeVimes family on your computer is a severe intrusion into your computer's security and can be devastating if not treated immediately with a real, reliable and advanced anti-malware application. Basically, any program in the Rogue:Win32/FakeVimes family of malware claims that they scan your computer system for malware, but actually does nothing but harass the victim with constant fake warnings claiming that the victim's computer is infected. The catch is that FakeVimes programs claim that they will only remove these nonexistent problems if the victim is willing to purchase a registration code for a "full version" of Rogue:Win32/FakeVimes responsible for the attack. Rogue:Win32/FakeVimes has been known to use trademarked logos and product names in order to disguise themselves as legitimate security programs.
Table of Contents
How Rogue:Win32/FakeVimes Attacks your Computer System
FakeVimes programs have been known to carry out browser hijacking and web browser redirects. The presence of an invasive fake security program and constant fake security alerts on your computer are the main symptoms of an infection with a Rogue:Win32/FakeVimes threat. FakeVimes programs are particularly dangerous because they tend not to be limited to spamming their victims with fake error messages. Members of the Rogue:Win32/FakeVimes family of malware have been known to disable known security programs as well as being able to stop file processes corresponding to applications that are often useful when dealing with malware.
FakeVimes programs can also bypass the Windows firewall, connect to a remote server and make dangerous changes to the Windows Registry. Recent members of the Rogue:Win32/FakeVimes family, particularly in 2012, have been known to be bundled with a rootkit component. This means that, while malware researchers have been able to update security software in order to deal with Rogue:Win32/FakeVimes infections, the rootkit component makes the Rogue:Win32/FakeVimes infection undetectable. In these cases, an anti-rootkit application may be necessary before trying to remove the Rogue:Win32/FakeVimes infection itself.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| BitDefender | Trojan.FakeAV.LEO |
| NOD32 | a variant of Win32/Kryptik.GUW |
| BitDefender | Gen:Variant.Barys.905 |
| eSafe | Win32.TRATRAPS |
| Avast | Win32:Kryptik-HWP [Trj] |
| McAfee | FakeAlert-FBO!B33E80FC0218 |
| CAT-QuickHeal | Trojan.FakeAV.nemj |
| AVG | Generic28.BAFO |
| Kaspersky | Trojan.Win32.FakeAV.msml |
| McAfee | Artemis!6ED6D330CDA2 |
| AVG | FakeAV.AAEP |
| Fortinet | W32/Basine.C |
| Kaspersky | Trojan-Dropper.Win32.Injector.cmiy |
| McAfee | Artemis!92942C6A4924 |
| Panda | Adware/RogueJunkA |
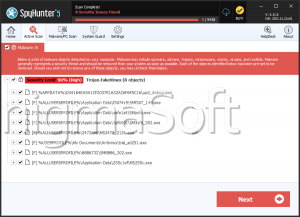
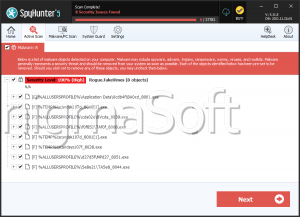
SpyHunter Detects & Remove FakeVimes
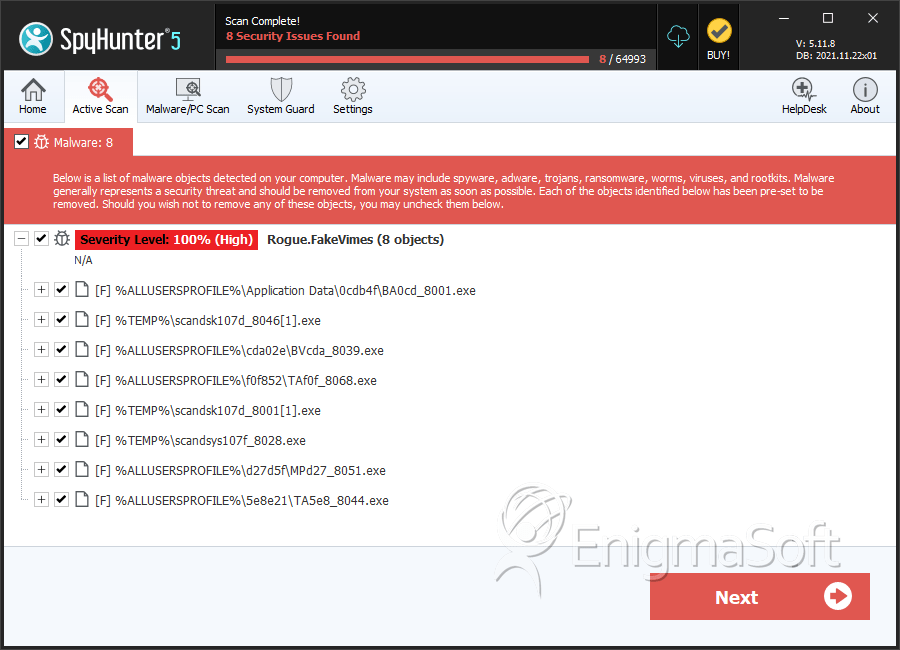
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | BA0cd_8001.exe | ca3aeda1e62cccfdc148c947aeeeebd5 | 71 |
| 2. | scandsk107d_8046[1].exe | bb38279988fcd5dfb313ac7803588daf | 53 |
| 3. | BVcda_8039.exe | 41697fb087b9d3924ad4d465e533cc48 | 52 |
| 4. | TAf0f_8068.exe | 1570e3d543406a1aac419a033bb701f9 | 50 |
| 5. | scandsk107d_8001[1].exe | 96943fd9b02fa996f348d7ce867c012b | 15 |
| 6. | scandsys107f_8028.exe | ea088f10a1b9297f71c4b1f1f5dbaa61 | 13 |
| 7. | MPd27_8051.exe | 92942c6a4924ebf85f58c2591452474e | 13 |
| 8. | TA5e8_8044.exe | 6d6a5c7e9d8522f35a56237a0a6c09ec | 11 |
| 9. | BAaba_8028.exe | fc23a98def665c7ae23136ffdfbe268f | 8 |
| 10. | AVf4b_8050.exe | d30f14b57d841c5ed78449d9d1d8f060 | 4 |
| 11. | APd44_8028.exe | b33e80fc0218e4e268e243422e37a87a | 4 |
| 12. | AS80c_8020.exe | 53e00c57e1c105c837fc64d6813d2663 | 3 |
| 13. | scandsk107d_8028[1].exe | e8ca18008b508982c12c9b04307a7e90 | 3 |
| 14. | AAdb4_8048.exe | ae492045c2e412f3c0732bd20f468e20 | 3 |
| 15. | AVa89_8050.exe | fdad5e201d698b3d66c5bb45b94e3c12 | 2 |
| 16. | AVd8d_8050.exe | 3b3d15d3b26918819ccbafabe13f9502 | 2 |
| 17. | TA81a_8068.exe | ab23544a651bedbeee1d6da6bb8f401b | 2 |
| 18. | scandsk107d_8001[1].exe | 101430a2539d0d5960b4d628fe8ad156 | 2 |
| 19. | MP050_8032.exe | 1b3324938817cd0c4d700d4acb2f02bb | 1 |
| 20. | 0.6567048221346792.exe | 1d3c9c66bfb6e0431764de1a0dc6d058 | 1 |
| 21. | 0.0013807596795621935.exe | b1f6225e4f291f0030d27af3e2f9cc39 | 1 |
| 22. | BA2ff_8001.exe | fc649800fbb20ea1fc4c0bd4fe3921b3 | 1 |
| 23. | BA676_8028.exe | 6ed6d330cda226bb3cf8d9948b95b24c | 1 |
| 24. | BA62b_8001.exe | a70a88be1fc5b481dc9065a349de3764 | 1 |
| 25. | BA621_8097.exe | d7d10ccece823eb9aefd5b401f79e16e | 1 |
| 26. | BA7e9_8028.exe | 08d9a59ffab33559c38c4e3f323dbfb4 | 1 |
| 27. | BA1ab_8028.exe | 7387055fa87c5771d984a196da5e90b4 | 1 |