Rodentia Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 2 |
| First Seen: | April 23, 2013 |
| Last Seen: | July 26, 2019 |
| OS(es) Affected: | Windows |
Rodentia Ransomware Image
There are new ransomware threats popping up daily. Some ransomware authors create highly weaponized, high-end threats that can cause tremendous damage. Others, however, are not that skilled and sometimes end up releasing pretty poorly made ransomware threats. This is the case with the Rodentia Ransomware.
Table of Contents
Infecting Your Computer
Malware researchers have not pinpointed a specific propagation method that is employed in spreading the Rodentia Ransomware. Some believe that the authors of the Rodentia Ransomware may have used some of the classic infection vectors that are most commonly used in propagating ransomware threats – corrupted software downloaded from unsecured websites, emails that contain macro-laced attachments, and bogus application updates. Usually, ransomware threats scan a system, locate the files that they were programmed to target and proceed to encrypt them. However, the Rodentia Ransomware does not do any of this.
The Ransom Note
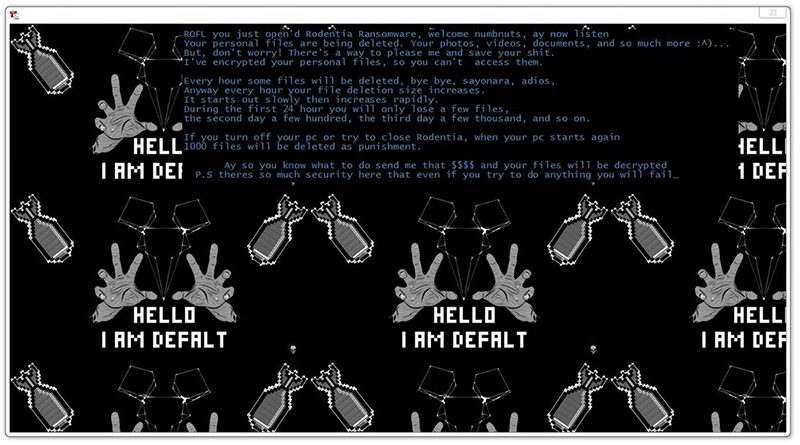
Once the Rodentia Ransomware infiltrates your system, it will present the user with a ransom note in the shape of a new program window, and it reads:
’ROFL you just open'd Rodentia Ransomware, welcome numbnuts, ay now listen Your personal files are being deleted. Your photos, videos, documents, and so much more :A But, don't worry! There's a way to please me and save your shit. I've encrypted your personal files, so you can't access them. Every hour some files will be deleted, bye bye, sayonara, adios, Anyway every hour your file deletion size increases. It starts out slowly then increases rapidly. During the first 24 hour you will only lose a few files, the second day a few hundred, the third day a few thousand, and so on. If you turn off your pc or try to close Rodentia, when your pc starts again 1000 files will be deleted as punishment. Ay so you know what to do send me that MS and your files will be decrypted P.S theres so much security here that even if you try to do anything you will fail_
send at leat $20 worth of Bitcoin
bitcoin address: 3K4XqrepBogMkrFJizfKt4gs8byGhQKXn5’
Empty Threats
Despite the cocky and over-the-top tone of the note, its authors have failed to weaponize this threat completely. Not only does the Rodentia Ransomware fall flat when it comes to encrypting any data, but it also is incapable of deleting any files, despite all the threats and claims in the note. The authors of the Rodentia Ransomware have made sure to use social engineering techniques when tailoring the ransom note. It is made to look scary with the images of bombs and creepily spread hands intentionally. Furthermore, there appears to be a timer, too, which is meant to further pressure the victim. The attackers demand $20 as a ransom fee. Perhaps the price is so low because they realize that this whole campaign is smoke and mirrors and hope that the user will quickly pay up before realizing that none of their files are affected.
Needless to say, you should not pay the ransom fee demanded, but you should certainly look into obtaining a reputable anti-virus software suite because next time you may not be so lucky and be infected by a much more harmful threat.

