Rocra/Red October malware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Ranking: | 2,122 |
| Threat Level: | 20 % (Normal) |
| Infected Computers: | 23,046 |
| First Seen: | January 15, 2013 |
| Last Seen: | September 20, 2023 |
| OS(es) Affected: | Windows |
Rocra/Red October malware Image
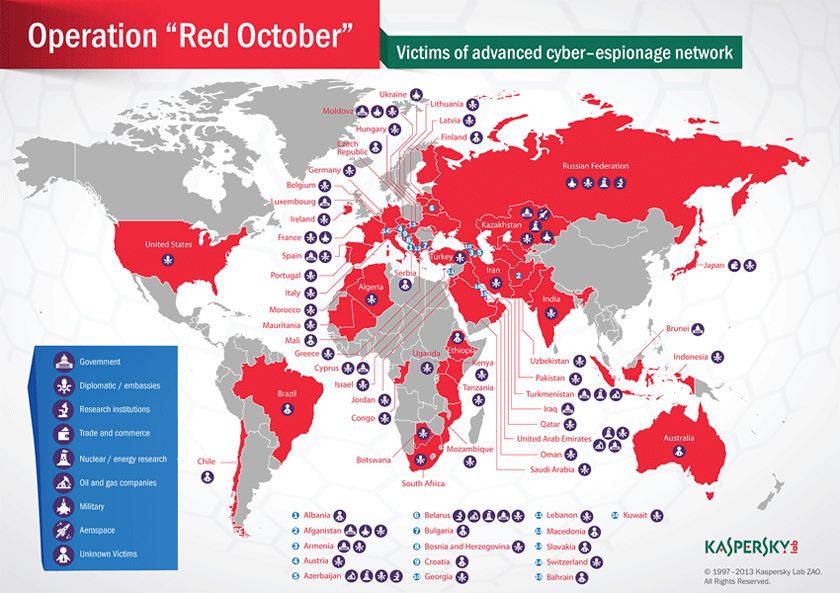
A dangerous malware infection known as Red October has been uncovered in recent months. This malware attack stands out because the Red October seems to be part of a worldwide campaign involving government agencies and important institutions. One of the aspects of the Red October attack that makes the Red October stand out from similar attacks is the length of time that the Red October has taken to uncover this malware campaign, which is comparable with other high profile malware attacks of recent years such as Flame and Stuxnet.
Computer security analysts have identified this malware attack as Red October or Rocra malware. The Red October targets government institutions and political parties in Eastern Europe, Central Asia, and countries that were previously members of the Soviet bloc. Red October is still active and has been constantly stealing data from all kinds of devices, ranging from mobile devices to network machines and individual computer systems. Red October uses numerous command and control servers around the world and, according to PC security researchers, its code is on par in complexity with high profile attacks like the Flame family of malware.
How the Red October is Distributed
Like many malware attacks, Red October begins with a social engineering component. According to malware analysts, Red October is distributed through phishing email messages that are carefully targeted at specific individuals in the kinds of government organizations listed above. The malicious email message contains an email attachment that attempts to exploit at least three different vulnerabilities in the Microsoft Office suite which it uses to install a Trojan on the victim's computer. Finally, this Trojan scans all other computer systems in the targeted machine's network in order to detect other machines vulnerable to these same exploits.
Red October can cause the infected computer to receive orders from a third party. These are typically used to spy on activity taking place on the infected computer. Some examples of typical tasks carried out through the use of Red October include downloading and opening malicious PDF or Microsoft Office documents that exploit vulnerabilities on the infected computer, logging all keystrokes and taking screenshots of the targeted computer's monitor and stealing browser passwords and browsing history. Red October can also steal encrypted files and even retrieve files that have already been deleted. Even worse, Red October can also target various mobile operating systems.
URLs
Rocra/Red October malware may call the following URLs:
| ourhotstories.com |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.