Robin Hood And Family Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 8 |
| First Seen: | May 3, 2018 |
| Last Seen: | October 24, 2025 |
| OS(es) Affected: | Windows |
The Robin Hood And Family Ransomware is a ransomware Trojan that PC security researchers first reported a ransomware Trojan called Robin Hood And Family Ransomware on April 20, 2018. The Robin Hood And Family Ransomware is delivered to victims in the form of corrupted DOCX files that are affixed to spam email messages. The spam emails messages used to deliver the Robin Hood And Family Ransomware will use social engineering techniques to fool computer users into downloading and opening their unsafe attachments. Once installed, the Robin Hood And Family Ransomware will attempt to extract a ransom payment from its victims by holding their files hostage. The Robin Hood And Family Ransomware receives its name from the signature attached to its ransom note.
Table of Contents
How the Robin Hood And Family Ransomware Attacks a Computer
The Robin Hood And Family Ransomware does not use an encryption algorithm to make the victim's files inaccessible like most ransomware Trojans. Instead, the Robin Hood And Family Ransomware does away with any pretense that it will help victim's recover their files when the ransom is paid and deletes the user-generated files on the infected computer directly. Examples of some files that threats like the Robin Hood And Family Ransomware target in their attacks include:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
The Robin Hood And Family Ransomware delivers a ransom note that claims that it has a backup of the files and can help restore them if the victim pays a ransom that is close to 1000 USD, and should be paid in Bitcoin. It is obvious, however, that the Robin Hood And Family Ransomware does not upload data to an external server or back up the victim's files in any way. The Robin Hood And Family Ransomware delivers its ransom note in the form of a text file named 'YOU ARE HACKED - READ ME.txt,' that is delivered to the victim's computer. The Robin Hood And Family Ransomware ransom note contains the following message:
'So, what the fuck just happened!!!???
You are hacked! In the past few hours, days, weeks or even monts (who knows how long) we have backed up all data from your computer. After that, well, we permanently deleted all your files. And no, you can't restore data from recycle bin.
How to retrieve your data? It's very easy, you have to pay 0.1 BTC (Bitcoin) to the folowing BITCOIN ADDRESS:
1CncuQzDP86vEpS3un8R7BT2yiEgUCpkQg
Note: Be careful with uppercase and lowercase letters in the address.
After payment send the code Pml2N6nHjK to the following email address: robinhoodxxx007@tutanota.com
The code Pml2N6nHjK is a unique ID of your computer.
After we receive 0.1 Bitcoin we will send you via email web address and login parameters where you can download your data.
Don't worry, we are taking care of our reputation.
Best regards,
Robin Hood and family'
Dealing with the Robin Hood And Family Ransomware Infection
Since the people responsible for the Robin Hood And Family Ransomware have no intention of restoring the affected files clearly, PC security researchers strongly advise computer users to refrain from paying the Robin Hood And Family Ransomware ransom. Instead, they should have file backups, which can help the victims of these attacks restore their files.
SpyHunter Detects & Remove Robin Hood And Family Ransomware
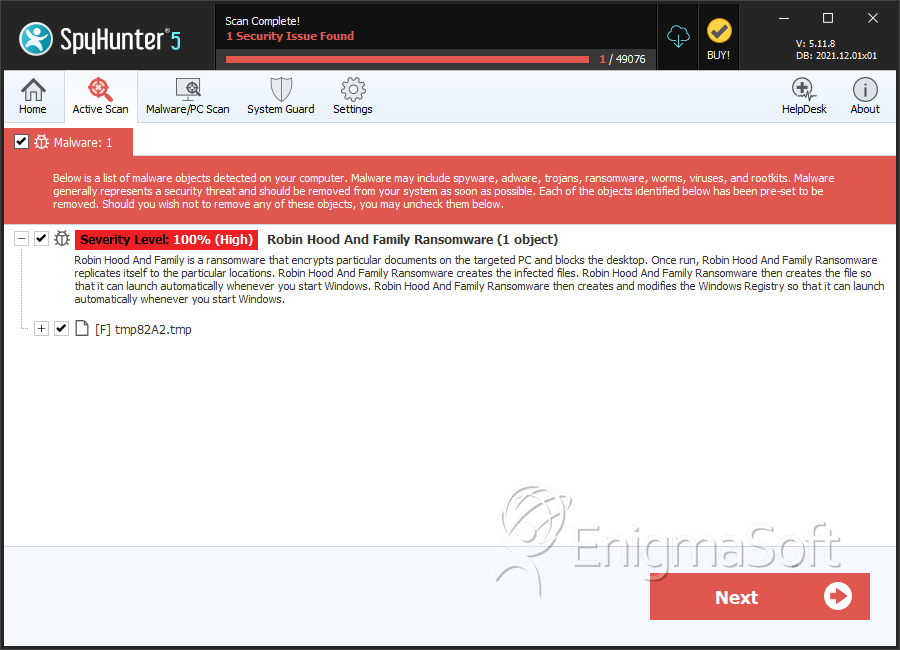
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | tmp82A2.tmp | 4c8116d9e5cfef0a72e9374e4706c4cb | 1 |
