RaRuCrypt Ransomware
The RaRuCrypt Ransomware is an encryption ransomware Trojan. These threats are designed to make the victim's files inaccessible, essentially taking them hostage. The aim of this attack is to force the victim to pay a ransom to receive the decryption key that is crucial to restoring the files encrypted by the RaRuCrypt Ransomware attack. Fortunately, PC security researchers have released the password that is necessary to restore access to the files taken hostage by the RaRuCrypt Ransomware attack.
Table of Contents
Symptoms of a RaRuCrypt Ransomware Attack
PC security researchers first reported the RaRuCrypt Ransomware attacks in the third week of February 2018. The RaRuCrypt Ransomware attacks have been targeting computer users in North America, Russia and Western Europe. Unlike many ransomware Trojans that encrypt the victim's files with a strong encryption algorithm directly, the RaRuCrypt Ransomware will put the victim's files into a password protected archive. These encrypted archive files use strong password protection that is just as difficult to undo as the encryption algorithms used in other, similar attacks. Fortunately, PC security researchers have managed to find the password needed to restore the files made inaccessible by the RaRuCrypt Ransomware attack. However, the people responsible for the RaRuCrypt Ransomware attack could release new versions of the RaRuCrypt Ransomware at any time, where the password would no longer help victims recover from the attack.
How the RaRuCrypt Ransomware Carries out Its Infection Process
The RaRuCrypt Ransomware will scan the victim's computer for certain file types, generally looking for the user-generated files with certain file extensions. The RaRuCrypt Ransomware will take these files and store them in a password protected archive file. The RaRuCrypt Ransomware will then delete the original files, essentially making the victim's files inaccessible. The following are some of the file types that are typically targeted by infections like the RaRuCrypt Ransomware:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
The RaRuCrypt Ransomware delivers its ransom note in ten different files, which are numbered from one to ten. These files, named 'README[1 to 10].txt,' are dropped on the infected computer's desktop. They contain a ransom note written in Russian and English with the following message:
'Ваши файлы были зашифрованы!
Стоимосты расшифровки: 200 RUB
Контакы: vk[.]comid12269280
-------------------------------------------
Attention! Your files were encrypted!
Decryption costs: 200 RUB.
Contacts: vk[.]com/id12269280'
Dealing with a RaRuCrypt Ransomware Infection
The ransom note seems to be associated with a particular social media profile, and the people responsible for the RaRuCrypt Ransomware attack seem to be trying to take credit for the attack, perhaps as a way to compete with other cybercrooks, or as a way to frame specific people. PC security researchers uncovered the password needed to unlock the affected files. The RaRuCrypt Ransomware can be unlocked with the following password:
S?{DCO^C!{L@CR^+<7E}2
To unlock the affected files, computer users can use a program for opening the archive files, such as WinRAR or 7Zip. However, the RaRuCrypt Ransomware's infection itself should be removed quickly. To do this, PC security researchers strongly advise computer users to use a reliable security program that is fully up-to-date to perform a full scan of the infected computer.
SpyHunter Detects & Remove RaRuCrypt Ransomware
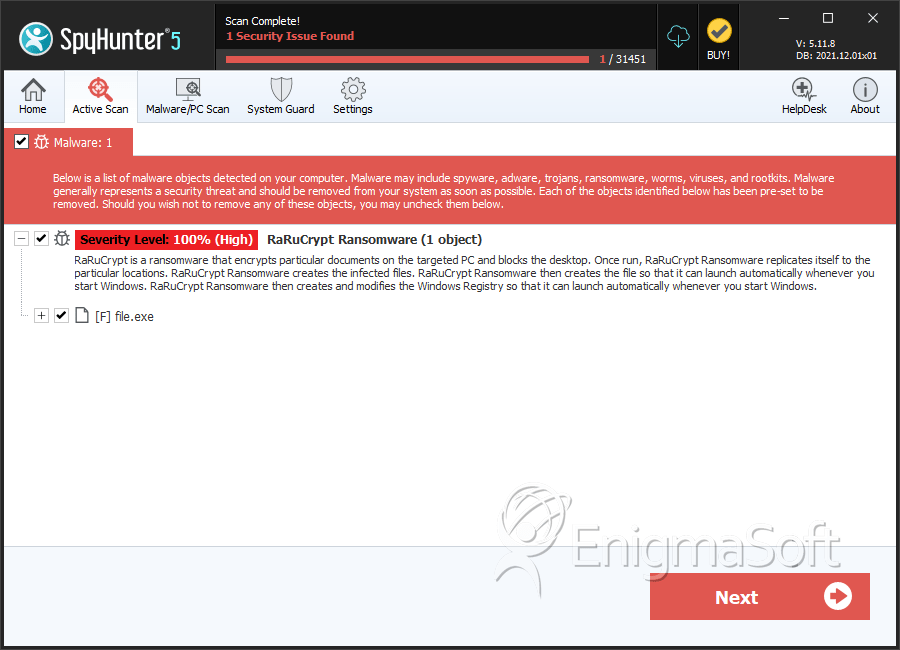
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 576dd75718942a49f1ac141a9e31d927 | 0 |

