Ranion 1.07 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 71 |
| First Seen: | February 7, 2017 |
| Last Seen: | October 4, 2020 |
| OS(es) Affected: | Windows |
The Ranion Ransomware is an encryption ransomware Trojan that is part of a RaaS service (Ransomware as a Service). The Ranion Ransomware has been around for some time, at least since February of 2017. A copycat version of the Ranion Ransomware was released in November of 2017, but it does not have a connection to this RaaS. One of the reasons why the Ranion Ransomware caught the attention of PC security researchers originally, is that subscriptions to the Ranion Ransomware were being sold to the cybercrooks for a very low price, despite the fact that the Ranion Ransomware was being advertised as having been created for 'educational purposes only.' Threats like the Ranion Ransomware are designed to make the victims' files unusable by using a strong encryption algorithm to make the victim's files inaccessible and then delivering a ransom note asking for a large ransom payment from the victim. The Ranion Ransomware will infect the computers using most versions of the Windows operating system and is controlled anonymously by the people responsible for the Ranion Ransomware through TOR.
Table of Contents
How the Ranion Ransomware Attack Works
The Ranion Ransomware is designed to encrypt the victim's files with a strong encryption method. The Ranion Ransomware will scan the victim's computer for certain file types and then use the AES 256 encryption method to make the files inaccessible. The Ranion Ransomware will demand a ransom payment from the victim in exchange for the decryption key necessary to restore the affected files after encrypting the victim's files. The Ranion Ransomware will create a file named README on the victim's computer to demand its ransom payment. This file is written in several languages and demands the payment of a ransom through Bitcoins. The Ranion Ransomware will encrypt the following file types in its attack:
.txt, .rtf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .ods, .jpg, .jpeg, .png, .bmp, .csv, .sql, .mdb, .db, .accdb, .sln, .php, .jsp, .asp, .aspx, .html, .htm, .xml, .psd, .cs, .java, .cpp, .cc, .cxx, .zip, .pst, .ost, .pab, .oab, .msg.
The Ranion Ransomware Trojans are capable of evading most anti-virus programs that are used today and, in the future, it will be capable of encrypting additional file types.
The Ranion Ransomware’s Ransom Demands
The people responsible for developing the Ranion Ransomware allow their possible buyers to test the Ranion Ransomware's RaaS before using it. This may be because the people responsible for the Ranion Ransomware attack demand an upfront payment from other the cybercrooks rather than making their money by keeping a percentage of the proceeds from infections involving the Ranion Ransomware. The Ranion Ransomware can be customized to demand various ransom types and display its ransom demand in a variety of ways or languages. It is important to refrain from paying the Ranion Ransomware ransom. The fact that these RaaS tactics exist and that they are lucrative is only possible because computer users continue to pay the ransom amounts and there are enough computers in the wild that remain unsecured to allow these cybercrooks to continue carrying out attacks in an effective way.
Protecting Your Data from Threats Like the Ranion Ransomware
Invariably, the best protection against encryption ransomware Trojans like the Ranion Ransomware is to have file backups. Having backups on the cloud or an external memory device, away from the reach of threats like the Ranion Ransomware, means that computer users can restore their files easily after an attack, instead of having to risk paying the ransom or contacting the cybercrooks. In fact, file backups are such an effective protection that if enough computer users have backup copies of their files, these attacks would no longer be lucrative and would almost certainly disappear. Computer users can protect their data from threats like the Ranion Ransomware and other attacks by keeping a trustable and updated security solution running on their machines.
SpyHunter Detects & Remove Ranion 1.07 Ransomware
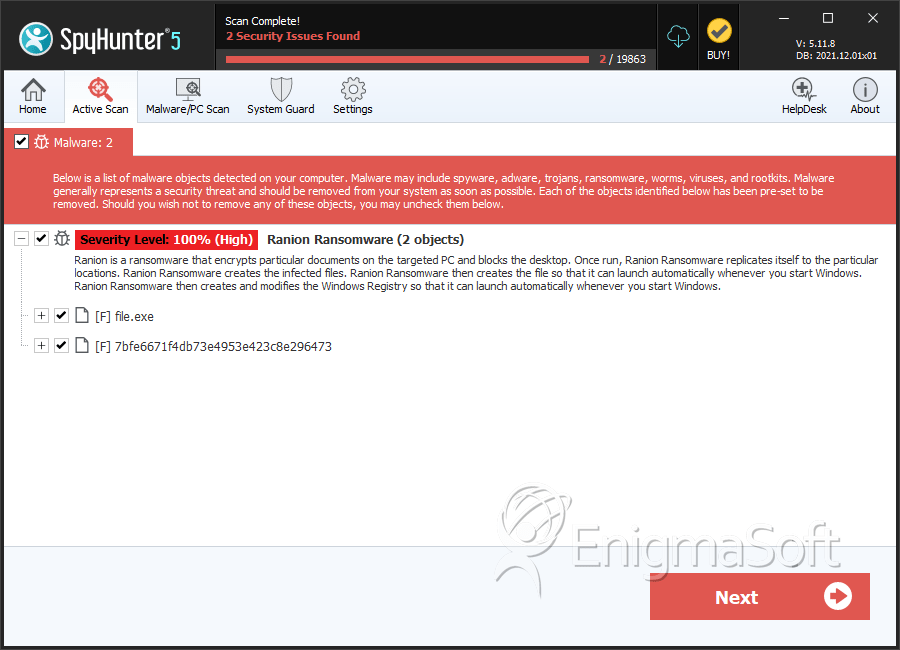
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 447af103027bb7cfa1c09538b38a6007 | 0 |
| 2. | file.exe | 72a1669e4c402bc24795badf7557f889 | 0 |
| 3. | 7bfe6671f4db73e4953e423c8e296473 | 7bfe6671f4db73e4953e423c8e296473 | 0 |

