Ragnar Locker Ransomware
Ragnar Locker Ransomware Image
The Ragnar Locker Ransomware is a new data-encrypting Trojan that appears to target businesses specifically. Ransomware threats' popularity does not seem to be dying off – on the contrary, more and more file-locking Trojans are being deployed.
Table of Contents
Propagation and Encryption
It is likely that the authors of the Ragnar Locker deploy the threat manually on already compromised systems. This comes to show that this is a more complex operation than most ransomware propagation campaigns. Before launching the Ragnar Locker Ransomware, the attackers would make sure to inject a module that is capable of collecting data that is of interest from the infected machines. The authors of the ransomware threat state that unless the victim complies with their demands, all their important data will be leaked online. However, malware researchers are not yet able to confirm whether the creators of the Ragnar Locker Ransomware gather data from the compromised hosts, or they are just using the argument as a social engineering trick. The Ragnar Locker Ransomware will use an encryption algorithm to lock all the targeted data. Upon locking a file, the threat will append a new extension to its name '.ragnar_' Every affected user has a uniquely generated victim ID, which contains numbers and uppercase letters. The Ragnar Locker Ransomware is capable of spotting any processes linked to commonly used remote desktop applications. If any are detected, the Ragnar Locker Ransomware will attempt to shut them down. This makes it more difficult for the victim to get remote help.
This Week In Malware Episode 33 Part 2: Campari Beverage Maker & Capcom Gaming Company Suffer RagnarLocker Ransomware Attacks
The Ransom Note
The Ragnar Locker Ransomware would drop a ransom note named '.RGNR_.txt.' In the note, the attackers state what the demanded ransom fee is. According to reports from victims, the ransom fee is calculated individually. One thing remains unchanged – the fee is sky-high. Cybersecurity analysts state that the authors of the Ragnar Locker Ransomware tend to demand between $200,000 and $600,000. To protect their identity and avoid negative consequences, the attackers demand to be paid via Bitcoin. The creators of the Ragnar Locker Ransomware go a step further in securing their anonymity – they can only be contacted via TOX. This is an instant messaging client that is Tor-based.
It is best to avoid contacting the authors of the Ragnar Locker Ransomware. They would not help you unless you agree to pay the astronomical ransom fee, which is a very bad idea, as there is no guarantee that you will get a decryption key even if you comply. Make sure your system is protected by a genuine anti-malware solution and do not forget to update all your applications regularly.
Update April 14th, 2020 – Ragnar Locker Gang Hits A “Big Fish”
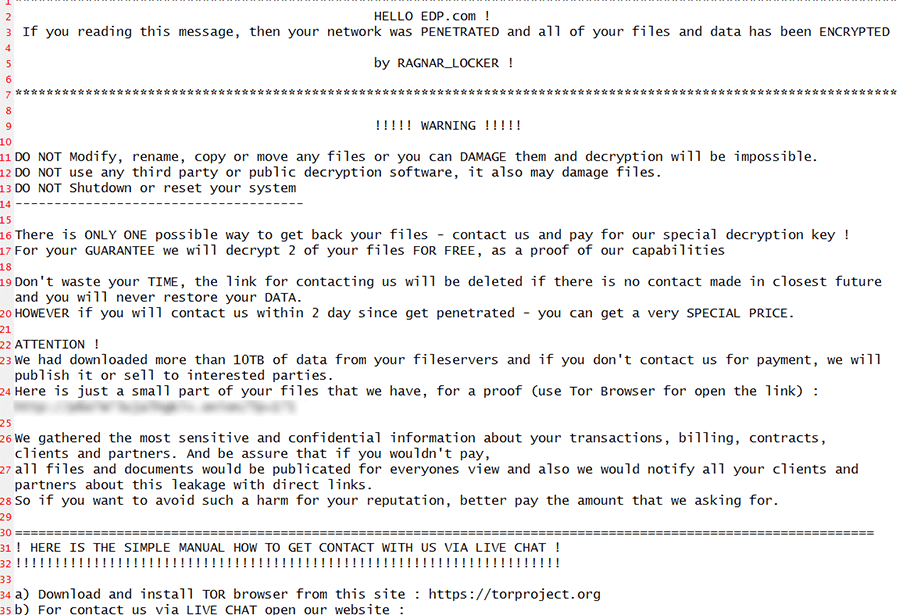
On April 14, 2020, security experts reported that the threat actors behind the Ragnar Locker ransomware had hit Energias de Portugal (EDP), a Portuguese multinational energy giant, and one of the largest European companies in the energy sector.
This Week In Malware Episode 37 Part 1: Ragnar Locker Ransomware Gang Using Facebook Ads To Extort Money From Malware Victims
The company has more than 11,500 employees worldwide, operating in 19 countries on four continents, delivering energy to more than 11 million customers. Headquartered in Lisbon, it's the 4th biggest producer of wind energy in the world, with $14.5 billion in revenue for 2019, a thing that the attackers certainly put into consideration when making the ransom demand.
The threat actors posted on their leak site, demanding a whopping 1,580 bitcoin ($11 million at the time of writing) from EDP, as they claim to have stolen more than 10TB of sensitive company information that they threaten to release if the ransom demand is not met within 20 days of the infection.
The Ragnar Locker group uploaded a few files and screenshots to their leak site, as proof of their successful data theft. Among the data, is an edpradmin2.kdb KeePass password manager database, which contains EDP employee accounts, login credentials, notes, and URLs.
Apart from the leak site upload, the attackers also dropped a note on EDPS systems, informing the company that they were able to obtain confidential information on transactions, billing, contracts, partners, and clients.
"And be assure that if you wouldn't pay, all files and documents would be publicated for everyones view and also we would notify all your clients and partners about this leakage with direct links," the note read. "So if you want to avoid such a harm for your reputation, better pay the amount that we asking for."
A company spokesperson for EDP confirmed the attack happened on Easter Monday but was not able to verify the ransom demand. He also noted that: "The power supply service and critical infrastructure, however, have never been compromised and we continue to ensure this operation as normal," and that: "EDP is working with authorities, that were immediately notified of the attack to identify the origin and anatomy of the attack."
Q4 2020 Update: Ragnar Ransomware Attacks Reach Facebook Through Hacked Beverage Company
Discovered in the fourth quarter of 2020 by researchers at securityaffairs.co, Ragnar Locker Ransomware hackers are pushing ads on Facebook through a hack on the Italian beverage vendor Campari Group, which resembles the image below of the Ragnar Locker ransom note. Campari Group did announce that their computer systems were "sidelined by a malware attack."
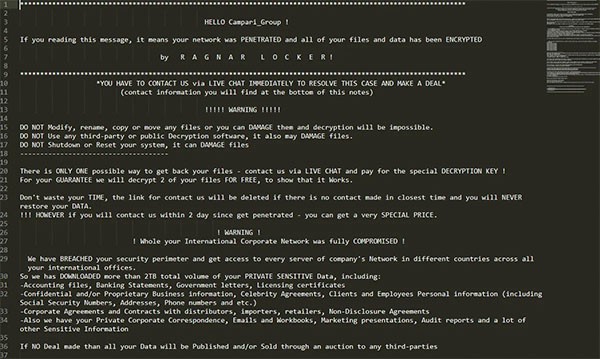
Ragnar Locker Ransomware Facebook ad text from hacker group attacking Campari beverage company - Source: Securityaffairs.co
It looks as if the advertising campaign initiated the week of November 9, 2020 titled "Security breach of Campari Group network." Thousands of Facebook users are suspected to have seen the ad and Facebook is currently investigating the issue. Such an ad making its way to Facebook is more evidence of how ransomware threats are branching out to find other avenues of spreading and extorting money from computer users on various platforms and social media networks. Computer users must beware and vigilant!

