Radamant Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | December 21, 2015 |
| OS(es) Affected: | Windows |
The Radamant Ransomware is a ransomware infection that encrypts its victims' files and changes their extension to RDM. The Radamant Ransomware can infect all versions of the Windows operating system. Like other ransomware threats, the Radamant Ransomware will invade the victim's computer and encrypt files found on the affected hard drive. Ransomware infections such as the Radamant Ransomware are among the most feared threats because recovery of the encrypted files is practically impossible without access to the decryption key. The irreversible nature of these infections has resulted in a marked increase in ransomware infections in recent years. If the Radamant Ransomware is installed on your computer, you should restore your files from a backup after removing the Radamant Ransomware with the help of a reliable security application that is fully up-to-date.
Table of Contents
Some Characteristics of the Radamant Ransomware
The Radamant Ransomware is designed to encrypt files and change their extension to RDM. After the Radamant Ransomware encrypts a file, it becomes inaccessible to the computer user. In most cases, the Radamant Ransomware will be distributed using Trojan delivery methods, and the Radamant Ransomware may be linked to another threat infection on the same computer. Because of this, good browsing practices and a reliable security application that is fully up-to-date can do much to prevent a Radamant Ransomware infection.
Dealing with the Radamant Ransomware
Removing the Radamant Ransomware is relatively straightforward. The affected computer can be started up in Safe Mode and then a strong security program can be used to remove the Radamant Ransomware completely. Computer users also may need to remove all files associated with the Radamant Ransomware and uninstall its entries from the Registry Editor and Windows settings. However, since the problems associated with the Radamant Ransomware are so many, it is important to prevent any risk of the return of the Radamant Ransomware due to an improper removal. Because of this, the best bet is for computer users to wipe their hard drive completely before restoring their files from the backup location. The Radamant Ransomware will display numerous misleading messages to convince computer users to pay a ransom to recover the affected files: PC security researchers strongly advise against paying the Radamant Ransomware's ransom.
Do not Pay the Radamant Ransomware If You can Help It
Unfortunately, the encryption used by the Radamant Ransomware is not practically breakable without the decryption key. However, PC security researchers strongly advise against paying the Radamant Ransomware's ransom, and use this option only as a last resort. The best way to stop threats like the Radamant Ransomware from recurring is to ensure that computer users backup their data regularly using a secondary memory device or the Cloud. Once all computer users get into the habit of regularly backing up important data, the Radamant Ransomware, and similar ransomware infections will have no leverage.
The main reason to not pay the Radamant Ransomware's ransom is that you have no guarantee that the people responsible for the Radamant Ransomware will help you decrypt your files. These are, after all, not the most trustworthy people. There is an equivalent chance that they will instead simply demand more money, or you will not hear back from them after you've sent the money. Besides, paying the Radamant Ransomware's ransom allows ransomware creators to continue spreading and creating their threats. Apart from good backup practices, not negotiating with these con artists is also a good prevention tactic to stop these kinds of infections.
Preventing the Radamant Ransomware from Entering Your Computer
There are multiple ways you can reduce the risk of infections such as the Radamant Ransomware:
- Never open unsolicited email attachments or embedded links.
- Use a reliable security application that is fully up-to-date to protect your computer.
- Stay away from websites commonly regarded as unsafe, such as online casinos and pharmacies, pornographic websites, and illegal video streaming or file sharing Web pages.
SpyHunter Detects & Remove Radamant Ransomware
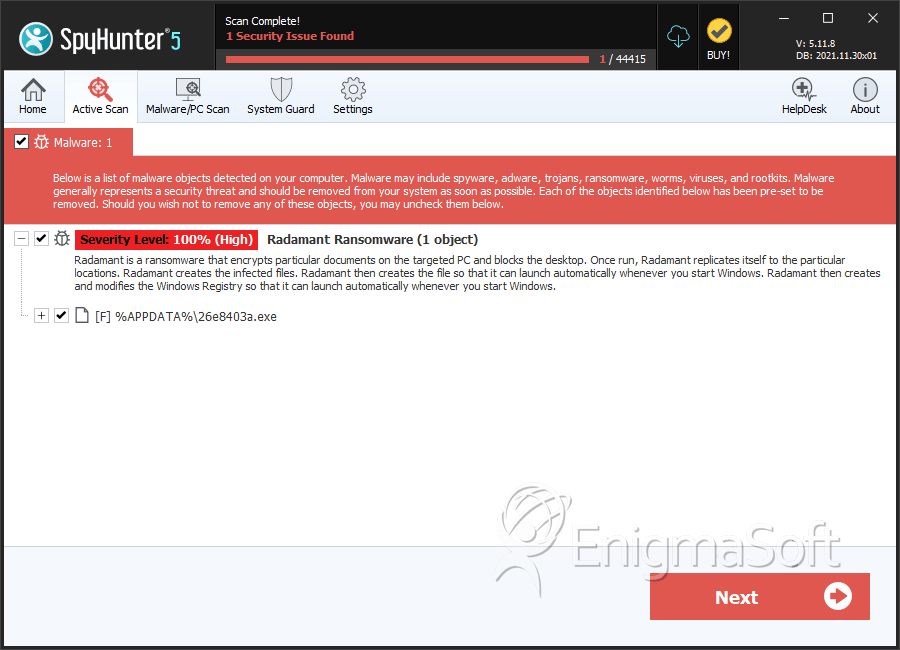
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 26e8403a.exe | 9c8fdcf946812b81c9fda6750c7ad917 | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.