QuasarRAT
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 4,232 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 25,421 |
| First Seen: | August 30, 2016 |
| Last Seen: | October 14, 2025 |
| OS(es) Affected: | Windows |
The QuasarRAT is a Trojan that is a heavily modified version of the open-source project carrying the same name "QuasarRAT" by a programmer dubbed 'quasar' who has a page on Github.com/quasar/QuasarRAT. The QuasarRAT software is promoted as a Remote Administration Tool (RAT) for server admins and cyber security managers in the government and private sector. The clean and corrupt versions of QuasarRAT differ in how they are packed, the presence of an obfuscation layer and manner of network communication. The QuasarRAT or Quasar Remote Access Trojan was used in targeted attacks on the government of the United States of America in early 2017 and samples of the malware surfaced in October 2017 with new attacks being recorded. It is not clear who is behind the QuasarRAT threat, but its attack vector appears to remains the same.
- The Trojan Dropper is received by a targeted user as an attachment to a spear phishing email. The majority of the attachments associated with QuasarRAT appear to feature names like 'Scanned Document,' 'Audio Recording,' 'Presentation,' and other names, which can be perceived as titles for office documents. The fake documents may have a double extension and be masquerade as a safe file using icons associated with Microsoft Office. For example, what appears to be a text file may be titled 'Report HG485.docx.exe' and trigger a User Account Control prompt on the screen as opposed to loading in Microsoft Word.
- The Trojan-Dropper is observed to extract a copy of the Downeks threat, which we have seen in the past. The Downeks Trojan-Dropper connects to a hardcoded URL and downloads the main body of the QuasarRAT.
- The QuasarRAT is installed on the system, and the attacker can access all data saved on the computer and connected network data storage. Additionally, the attacker can use QuasarRAT to install third-party software, remove programs, terminate processes and take screenshots.
That is not the full range of operations the remote user can perform. Malware investigators add that the QuasarRAT operators could download files, edit the Registry, open remote desktop connections, collect passwords, load Web pages, issue commands to the keyboard and mouse. Cybersecurity experts discovered that the QuasarRAT threat exhibits vulnerabilities regarding the client-server communication. The vulnerabilities could be exploited and allow the infected PC user to launch a counterattack and install a copy of QuasarRAT on the 'Command and Control' servers used by the first attacker potentially. It is not a good idea to remove the QuasarRAT manually and attempt counterattacks if you are not a computer security expert with experience under your belt. Regular PC users are encouraged to use a reputable anti-malware solution to eliminate the QuasarRAT and block unauthorized connections to the system.
Table of Contents
SpyHunter Detects & Remove QuasarRAT
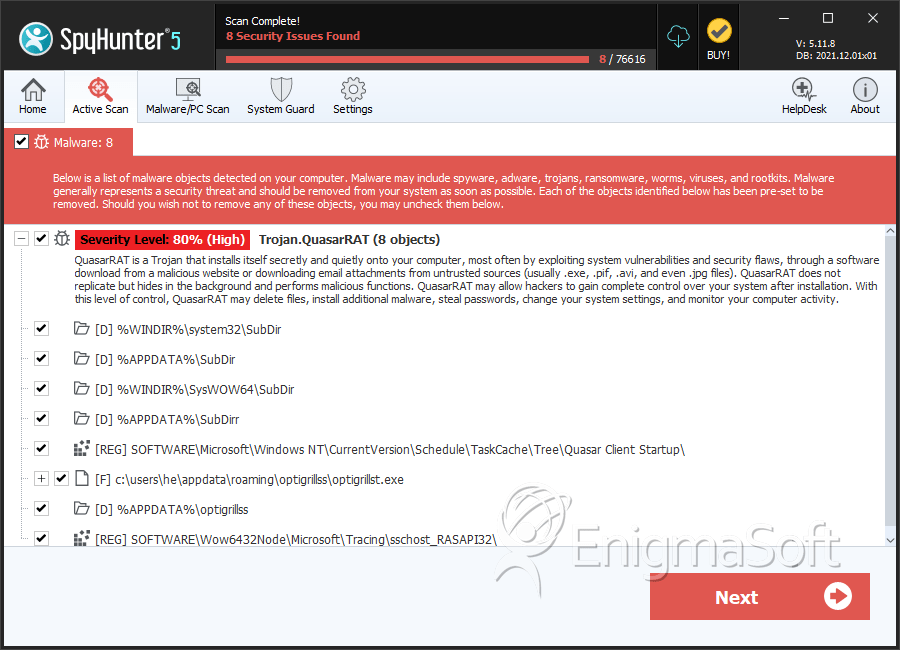
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | optigrillst.exe | 59122b93dabdb8d0736adcf7f57f71df | 30 |
| 2. | file.exe | 46d08a8be16768ee32fcbaa8083ea2f0 | 0 |
Registry Details
Directories
QuasarRAT may create the following directory or directories:
| %APPDATA%\SubDir |
| %APPDATA%\SubDirr |
| %APPDATA%\optigrillss |
| %WINDIR%\SysWOW64\SubDir |
| %WINDIR%\system32\SubDir |
Analysis Report
General information
| Family Name: | Trojan.QuasarRAT |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
8a75af44f5eb8629fb20e900290ad192
SHA1:
2b7813690b94b161c5f0bd2bf7f8e6d3e40c475c
SHA256:
1B6BC2A126CE92F4BB34BA26C4F1E86B84529294411845280E687A66938C3C5A
File Size:
3.27 MB, 3266048 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have security information
- File is .NET application
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is not packed
- IMAGE_FILE_DLL is not set inside PE header (Executable)
Show More
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Assembly Version | 1.4.1.0 |
| File Description | Quasar Client |
| File Version | 1.4.1 |
| Internal Name | Client.exe |
| Legal Copyright | Copyright © MaxXor 2023 |
| Original Filename | Client.exe |
| Product Name | Quasar |
| Product Version | 1.4.1 |
File Traits
- .NET
- Run
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 138 |
|---|---|
| Potentially Malicious Blocks: | 90 |
| Whitelisted Blocks: | 48 |
| Unknown Blocks: | 0 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Syscall Use |
Show More
|
| User Data Access |
|
| Other Suspicious |
|
| Anti Debug |
|
| Encryption Used |
|