Qbot Spreads Through Windows Defender Phishing Emails
 Qbot aka Quakbot started out as a banking trojan but nowadays it also installs other malware threats and cybercriminals use it to gain access to networks. One of Qbot's main infection vectors is as a second stage payload for Emotet and the other is phishing emails. Cybercriminals are always on the lookout for good phishing themes and recently the operators of Qbot have settled on Windows Defender.
Qbot aka Quakbot started out as a banking trojan but nowadays it also installs other malware threats and cybercriminals use it to gain access to networks. One of Qbot's main infection vectors is as a second stage payload for Emotet and the other is phishing emails. Cybercriminals are always on the lookout for good phishing themes and recently the operators of Qbot have settled on Windows Defender.
Windows Defender is the built-in antimalware solution for Windows 10 and there are many users who aren’t focused on security who only rely on it for protection. As such, Windows Defender is a solid choice for phishing bait. The current Qbot campaigns don’t deviate from previous attacks.
The potential victim receives an email that in this case is made to look like it is an alert which comes from Windows Defender. The email contains an attachment that the user is encouraged to open. The attachment is an Excel .xls file that supposedly contains the alert. The way Qbot infects a system through the file are malicious macros. In order for the infection to occur, the potential victim must have macros enabled. To make the user do that, the cybercriminals claim the document is encrypted and the user must click on "Enable Content" and that actually enables macros. If enabled, the macros are executed and will download and install Qbot.
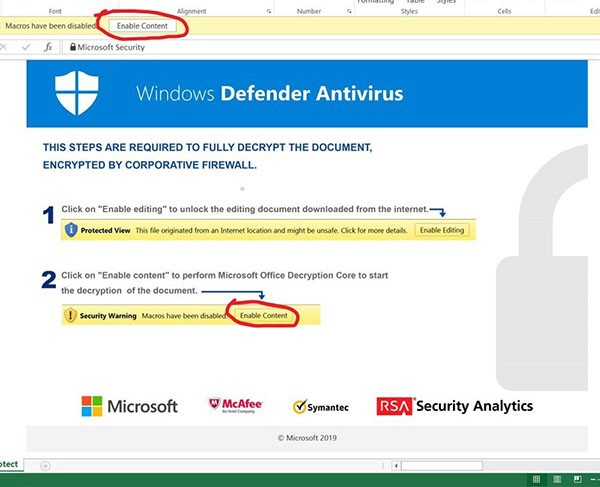
Qbot Phishing Email Example
Once Qbot infects a device it can cause a lot of damage. One of the things Qbot does is locate and steal any banking credentials it can find. Another function of this malware is to distribute other threats. Qbot itself is often the second stage payload in Emotet infections. On top of that if the infected device is on a network, Qbot can give cybercriminals access to that computer and potentially to the whole network. In such cases, the operators will commonly try to deploy some sort of ransomware. Qbot and by extension Emotet are often followed by ProLock ransomware attacks.
Security conscious users are unlikely to fall for a phishing scheme like this, but there are more than enough casual users who will. With Emotet's recent resurgence, the number of Qbot infections is likely to grow even further. While big organizations make for more desirable victims, individual users stand to lose a lot too.