PWS:Win32/Zbot.gen!Y
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 311 |
| First Seen: | January 13, 2011 |
| Last Seen: | April 14, 2021 |
| OS(es) Affected: | Windows |
PWS:Win32/Zbot.gen!Y, also known as W32/Zbot.YFP is a dangerous Trojan associated with notorious botnets and the Zeus Trojan. This malware infection spreads through a spam email campaign that has been notorious in the final months of 2011, targeting inexperienced computer users by offering updates for Acrobat Reader and other popular products from Adobe Systems. The email messages carrying PWS:Win32/Zbot.gen!Y use subject lines such as 'Adobe Software Critical Upgrade Notification ID: [Random Number]' and in order to make it appear that the scam emails are coming from Adobe itself, they spoof Adobe's email address. PWS:Win32/Zbot.gen!Y spreads in a compressed file attached to this scam email. The main goal of PWS:Win32/Zbot.gen!Y is to steal its victim's online banking details such as account numbers and passwords. ESG security researchers strongly recommend that you ignore these fake emails from Adobe Systems. A legitimate software company like Adobe Systems will never distribute software updates through these kinds of emails, especially since these malicious emails have been associated with spreading malware and various online scams for a long time. If you are threatened to these kinds of malicious emails, ESG malware analysts strongly recommend that you mark the offending email as spam and not to open the enclosed file under any circumstances. If your computer system becomes infected with PWS:Win32/Zbot.gen!Y, a lengthy and inconvenient removal procedure will be necessary to return your computer to normal conditions.
Table of Contents
An Overview of the PWS:Win32/Zbot.gen!Y Scam Email
The scam email associated with PWS:Win32/Zbot.gen!Y contains an attachment that is named 'AdobeSystems-Software_Critica Update Dec_2011-[Random].zip,' in the form of a compressed file. Within this compressed file, you will find an executable file that contains the PWS:Win32/Zbot.gen!Y infection itself. One of the most common ways of distributing malware online is through the use of compressed files in ZIP format. This is because these kinds of files do not allow computer users to view their contents without opening them. Inside, they will usually contain components designed to run the malware it contains automatically as soon as the compressed file is opened. PWS:Win32/Zbot.gen!Y is only one of a couple of problems associated with Adobe Systems. Due to this company's software's popularity, criminals have found ways of taking advantage in order to target as many victims as possible. Apart from these malicious email scams, Adobe software has also been targeted in 2011 by 0-day exploits that have claimed a large number of victims worldwide.
Aliases
15 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Panda | Trj/Spy.AB |
| AVG | PSW.Generic8.BFLK |
| Fortinet | W32/Zbot.AT!tr |
| AhnLab-V3 | Win-Trojan/Zbot.141824.AO |
| eTrust-Vet | Win32/Zbot.EGB |
| Sophos | Troj/PWS-BSF |
| AntiVir | TR/Hijacker.Gen |
| BitDefender | Gen:Variant.Kazy.1779 |
| Kaspersky | Trojan-Spy.Win32.Zbot.biwp |
| ClamAV | Trojan.Spy.Zbot-142 |
| eSafe | Win32.TRHijacker |
| Avast | Win32:Fraudo [Trj] |
| F-Prot | W32/Zbot.BR.gen!Eldorado |
| McAfee | PWS-Zbot.gen.ds |
| CAT-QuickHeal | TrojanSpy.Zbot.capz |
SpyHunter Detects & Remove PWS:Win32/Zbot.gen!Y
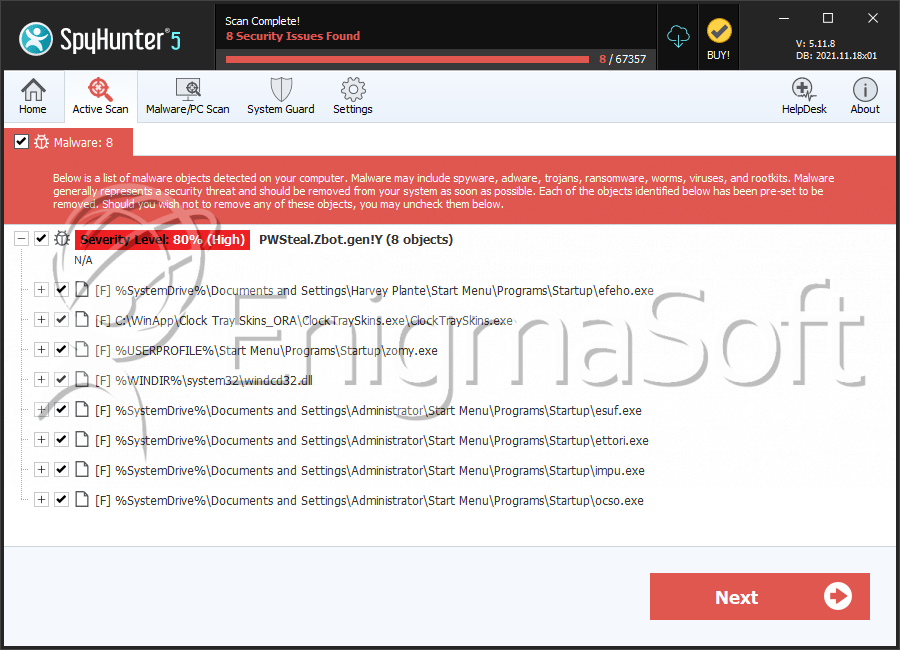
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | efeho.exe | d3d85d43f636a6af45f26b77ece99779 | 39 |
| 2. | ClockTraySkins.exe | a03d4b67795d68e95890764968d7bfdd | 32 |
| 3. | zomy.exe | cf04e0ba922c2b4e9207d5ee1571e66a | 23 |
| 4. | windcd32.dll | 84aa1c3cbdf98d121990c4dd997d6834 | 15 |
| 5. | esuf.exe | 9dfe3d9a9c07c1fbe337ea6364be1b3a | 14 |
| 6. | ettori.exe | 13286600b62779dcc885855cee33cbf9 | 14 |
| 7. | impu.exe | 6024d97573f3de5e4855f11a8b75f88f | 12 |
| 8. | ocso.exe | 322b092be8945a19c2413bcf72f7a585 | 12 |
| 9. | wwwrfd32.exe | ba6fc51b94e3e62c23c21b974cac0bac | 11 |
| 10. | AutoChk.exe | 277c921947fe032066e60bf485347c0d | 8 |
| 11. | ahwoe.exe | 198b6b002075364f1d87e76866994b3c | 3 |
| 12. | avny.exe | 29efc4ff647065f25084df1c6a0c6fc9 | 3 |
| 13. | nyliv.exe | 0c27478195764e6b01459039407210a2 | 3 |
| 14. | pciide2k.sys | 0f6c28d492d8baa532f6f3fa19f63b24 | 3 |
| 15. | netsvcs32.exe | 61be5d4ad0cf138ec4190e8043d56fb2 | 2 |
| 16. | csrrsx.exe | 931da0a3557c536ae94802a46cbb568d | 2 |
| 17. | compatWebaudio.dll | ce2202273d534c307484bdb8edb818b3 | 2 |
| 18. | Asdiph.exe | 06cde1dfb914f0757a0c2d3ebcbf0164 | 2 |
| 19. | movie[1].exe | ea16ffab2f264117e6f89c51b71e620e | 2 |
| 20. | ClickPotatoLiteSA.exe | e7f93f7f99f8c9154b1fb6fee108d234 | 2 |
| 21. | wins.exe | fab2b8b1ca3a351e5925a72c547dbcbf | 2 |
| 22. | paaw.exe | 79e032ccdc5fafff28f85631f13e3689 | 2 |
| 23. | zybu.exe | 76410d9afc8af1477280f92e5139e3d5 | 1 |
| 24. | setup1349310592.exe | 9a036945a46e56c372fcc74af0486649 | 1 |
| 25. | 20578.dll | a57deb949016484cea1c74bd6c21a4c0 | 1 |
| 26. | IDMan.exe | 5972f0615994e9a2b564c21c47599f16 | 1 |
| 27. | vexe.exe | fe07c20d624f9e93b78d51958090f034 | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.