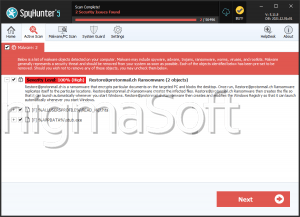
Proton Ransomware
Cybersecurity researchers discovered the Proton Ransomware threat and are warning users about its dangerous capabilities. Upon analysis, it was determined that Proton utilizes encryption to render the files of its victims inaccessible.
The threat also appends the victim's ID, the email address 'kigatsu@tutanota.com,' and the extension '.kigatsu' to the filename of the encrypted files. A ransom note will then be dropped on the breached devices under the form of a ransom note named 'README.txt.' An instance of how the Proton ransomware alters filenames can be seen with the renaming of '1.png' to '1.png.[Kigatsu@tutanota.com][729159DF].kigatsu.'
Victims of the Proton Ransomware will Have Their Data Held Hostage
The ransom note that the victims of the Proton Ransomware receive indicates that their files have been encrypted with a combination of two different algorithms: AES and ECC. The note also states that it is impossible to recover the encrypted files without obtaining decryption services from the threat actors. To demonstrate their capability, the attackers offer a guarantee to decrypt one sample file that is smaller than 1 MB.
The ransom note provides several different contact methods: a Telegram account (@ransom70) and two email addresses ('kigatsu@tutanota.com' and 'kigatsu@mailo.com'). The note urges the victim to act quickly and pay the ransom to receive a decryption tool at a lower price. Additionally, the victim is advised not to delete or try to modify the encrypted files in any way as it may affect decryption.
It is important to note that paying the ransom is not recommended, as it carries a high risk of being scammed. Even after paying the ransom, victims are not guaranteed to receive a decryption tool. It is also extremely important to remove the ransomware from infected systems immediately to prevent further data encryption from occuring.
How not to be One More Victim of Ransomware Attacks?
To prevent a ransomware attack, users need to be aware of the tactics and techniques that attackers use to spread ransomware. This includes being watchful when clicking on links or downloading attachments from unknown sources, as well as being wary of suspicious emails or messages.
Users should also keep their software and operating systems up-to-date with the latest security patches to prevent susceptibilitys that could be exploited by attackers. In addition, it is crucial to have a reliable backup system in place so that data can be restored without paying a ransom if an attack occurs.
Furthermore, users should use strong passwords and multi-factor authentication to secure their accounts and devices. They should also limit access to sensitive information and systems only to those who need it.
Finally, it is important to stay informed about the latest threats and security trends and to educate others about the risks of ransomware. By staying vigilant and taking proactive measures, users can reduce the risk of falling victim to a ransomware attack.
The ransom note of the Proton Ransomware contains the following message:
'~~~ Proton ~~~
>>> What happened?
We encrypted and stolen all of your files.
We use AES and ECC algorithms.
Nobody can recover your files without our decryption service.
>>> How to recover?
We are not a politically motivated group and we want nothing more than money.
If you pay, we will provide you with decryption software and destroy the stolen data.
>>> What guarantees?
You can send us an unimportant file less than 1 MG, We decrypt it as guarantee.
If we do not send you the decryption software or delete stolen data, no one will pay us in future so we will keep our promise.
>>> How to contact us?
Our Telegram ID: @ransom70
Our email address: Kigatsu@tutanota.com
In case of no answer within 24 hours, contact to this email: Kigatsu@mailo.com
Write your personal ID in the subject of the email.
>>>>> Your personal ID: - <<<<<
>>> Warnings!
- Do not go to recovery companies, they are just middlemen who will make money off you and cheat you.
They secretly negotiate with us, buy decryption software and will sell it to you many times more expensive or they will simply scam you.
- Do not hesitate for a long time. The faster you pay, the lower the price.
- Do not delete or modify encrypted files, it will lead to problems with decryption of files'.