Princess Evolution Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 7 |
| First Seen: | August 22, 2018 |
| Last Seen: | March 6, 2020 |
| OS(es) Affected: | Windows |
The Princess Evolution Ransomware is an encryption ransomware Trojan that is the third release in the Princess Ransomware family of ransomware Trojans. Malware researchers suspect that the Princess Evolution Ransomware and its variants are part of a RaaS (Ransomware as a Service) platform. The first variants in this family of ransomware Trojans were first observed on July 31, 2018. The creators of the Princess Evolution Ransomware offer this RaaS to other criminals, pocketing 40% of the profits from all the attacks.
Table of Contents
How the Princess Evolution Ransomware Attack Works
The Princess Evolution Ransomware and similar threats are being delivered through corrupted advertisements. In many cases, the Princess Evolution Ransomware attacks have been linked to attacks involving the RIG Exploit Kit. Once the Princess Evolution Ransomware is installed, it carries out its attack, which involves encrypting the victim's files by utilizing a strong encryption algorithm (in most cases, the AES and RSA). The Princess Evolution Ransomware targets files with the following file extensions (among others) in its attack:
.ebd, .jbc, .pst, .ost, .tib, .tbk, .bak, .bac, .abk, .as4, .asd, .ashbak, .backup, .bck, .bdb, .bk1, .bkc, .bkf, .bkp, .boe, .bpa, .bpd, .bup, .cmb, .fbf, .fbw, .fh, .ful, .gho, .ipd, .nb7, .nba, .nbd, .nbf, .nbi, .nbu, .nco, .oeb, .old, .qic, .sn1, .sn2, .sna, .spi, .stg, .uci, .win, .xbk, .iso, .htm, .html, .mht, .p7, .p7c, .pem, .sgn, .sec, .cer, .csr, .djvu, .der, .stl, .crt, .p7b, .pfx, .fb, .fb2, .tif, .tiff, .pdf, .doc, .docx, .docm, .rtf, .xls, .xlsx, .xlsm, .ppt, .pptx, .ppsx, .txt, .cdr, .jpe, .jpg, .jpeg, .png, .bmp, .jiff, .jpf, .ply, .pov, .raw, .cf, .cfn, .tbn, .xcf, .xof, .key, .eml, .tbb, .dwf, .egg, .fc2, .fcz, .fg, .fp3, .pab, .oab, .psd, .psb, .pcx, .dwg, .dws, .dxe, .zip, .zipx, .7z, .rar, .rev, .afp, .bfa, .bpk, .bsk, .enc, .rzk, .rzx, .sef, .shy, .snk, .accdb, .ldf, .accdc, .adp, .dbc, .dbx, .dbf, .dbt, .dxl, .edb, .eql, .mdb, .mxl, .mdf, .sql, .sqlite, .sqlite3, .sqlitedb, .kdb, .kdbx, .1cd, .dt, .erf, .lgp, .md, .epf, .efb, .eis, .efn, .emd, .emr, .end, .eog, .erb, .ebn, .ebb, .prefab, .jif, .wor, .csv, .msg, .msf, .kwm, .pwm, .ai, .eps, .abd, .repx, .oxps, .dot.
The Princess Evolution Ransomware will identify the damaged files with a file extension made up of four random characters.
The Princess Evolution Ransomware’s Ransom Note
The Princess Evolution Ransomware delivers a ransom note in the form of a text file named '^_READ_TO_RE5T0RE_[RANDOM STRING].txt' and an HTML file named '^_READ_TO_RE5T0RE_[RANDOM STRING].html' dropped on the infected computer's desktop. The text of the Princess Evolution Ransomware's ransom note reads:
'Your ID: [sixteen random characters]
Your extension: G8xB
Your files are encrypted!
Download and install Tor Browser:
http://www.torproject.org/download/download-easy.html
And follow this link via Tor Browser:
http://royal666k6zyxnai.onion/
Or use this alternative in any exceptional cases:
http://royal666k6zyxnai.tor2web.top/'
When the victims of the Princess Evolution Ransomware attack visit the Princess Evolution Ransomware's payment portal, they are greeted with the following message:
'Your files are encrypted
Log into secure area to proceed with decrypting your personal data.
ENTER ID BELOW
[text box]
[SUBMIT|BUTTON]'
The criminals' instructions on the Princess Evolution Ransomware payment website reads:
'What to do next?
First of all, look at the timers. The upper one indicates remaining time before the price increase. The lower one indicates remaining time until database entry removal. After its expiry, data recovery will be impossible, your login will cease existing. You must act within the given time frames and now is the best moment to start. Then, you must realize that the solution is much more closer than you may think. Briefly, all you have to do is: get Bitcoin address, top up its balance and send the balance to our address. After completing these simple steps you will be able to download the decryptor and recover your files. We will guide you through this whale process to make this even simpler. Follow hereby instructions.
1. Navigate to 'buy Bitcoin' through the top section of this page
2. Choose preferable option and purchase required amount of Bitcoin
3. Send exactly 0.12000 'BTC' to the following Bitcoin address
Make sure the destination address of your transaction exactly matches this one. Each symbol.
4. Wait till the transaction is confirmed
5. Download and run Princess Decryptor'
However, PC security researchers advise not paying this ransom and instead restore the files encrypted by the attack from file backups stored on the cloud or another external device.
SpyHunter Detects & Remove Princess Evolution Ransomware
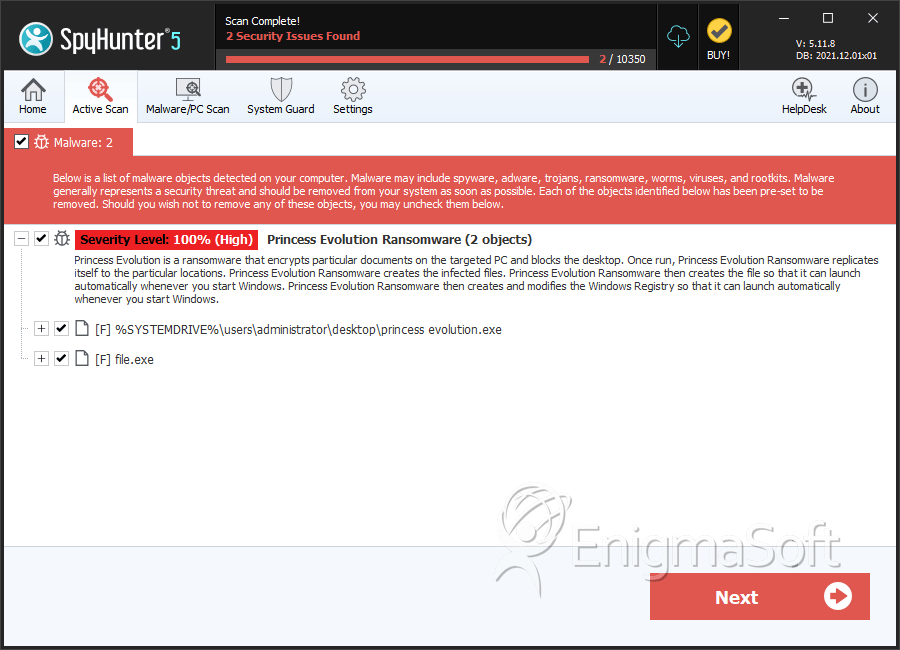
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | princess evolution.exe | b75d9ccdfe580ffcd53f987452be4dac | 3 |
| 2. | file.exe | acaeaf1e1ff0b043a37d2a3e3f9f3fbe | 1 |

