Poop Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 13 |
| First Seen: | November 16, 2016 |
| Last Seen: | July 23, 2019 |
| OS(es) Affected: | Windows |
Poop Ransomware Image
The Poop Ransomware is an encryption ransomware Trojan. The Poop Ransomware uses a strong encryption algorithm to make the victim's files inaccessible, essentially taking them hostage. The Poop Ransomware then demands a ransom payment in exchange for restoring the data it has captured.
Table of Contents
How the Poop Ransomware Attacks a Computer
The Poop Ransomware can be delivered in many ways, including corrupted spam email attachments or direct attacks on a device. Once the Poop Ransomware is installed, the Poop Ransomware runs a scan of the victim's computer, searching for the user-generated files. The Poop Ransomware uses the AES encryption to encrypt any file it finds, adding the file extension '.poop' to each file compromised by the attack. The Poop Ransomware targets the files below in this attack:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
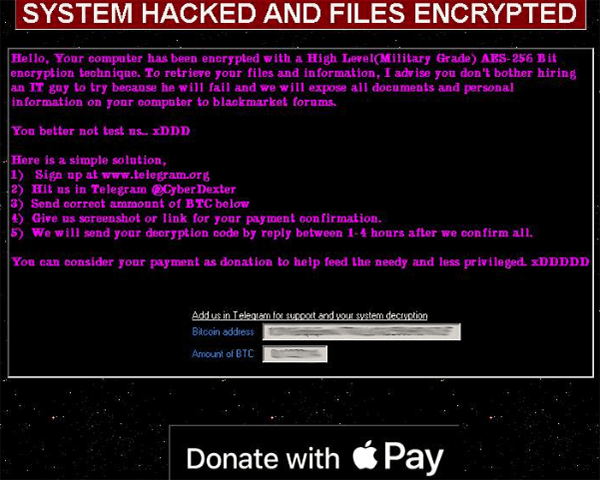
After encrypting the victim's data, the Poop Ransomware displays a pop-up window titled 'SYSTEM HACKED AND FILES ENCRYPTED.' This message alerts the victim of the attack and demands a ransom payment in Bitcoin that amounts to about USD 1,000 at the current exchange rate. The Poop Ransomware ransom note reads:
'Hello, Your computer has been encrypted with a High Level(Military Grade) AES-256 Bit encryption technique. To retrieve your files and information, I advise you don't bother hiring an IT guy to try because he will fail and we will expose all documents and personal information on your computer to blackmarket forums.
You better not test us.. xDDD
Here is a simple solution,
1) Sign up at www.telegram.org
2) Hit us in Telegram @CyberDexter
3) Send correct ammount of BTC below
4) Give us screenshot or link for your payment confirmation.
5) We will send your decryption code by reply between 1-4 hours after we confirm all.
You can consider your payment as donation to help feed the needy and less privileged. xDDDDD
Bitcoin address: 1K3YKBq8qGrnmJ7TKkLbTiGL59UHBYh7LF
Amount of BTC: 0.12277114'
What the Poop ransomware does is change the victim's wallpaper into one with the namesake substance on it, creating and dropping a text file named "READ_IT.txt" as well as opening a popup window.
Poop Ransomware also renames any affected files and appends them with the .poop extension. What is more, the ransomware also runs the Ranso process in the background of infected machines.
Both the popup and the text file state that the Poop Ransomware encrypts files with a 'military grade' encryption algorithm – AES 256. The victims are then warned against attempts to decrypt files through the use of third party tools or the people behind the Poop Ransomware will expose their encrypted files to criminals on dark web forums. The attackers instruct the victims to sign up to Telegram so they can contact Poop's developers through the @CyberDexter account on there. They claim this will allow the victims to purchase a decryption tool at the cost of 0.12277114 Bitcoin sent to the wallet address provided in the communication between both parties. As a proof of the transaction, victims are expected to send a screenshot of the transaction to the attackers.
Protecting Your Data from Threats Like the Poop Ransomware
The best protection against threats like the Poop Ransomware is to have the means to restore any data that becomes compromised by the attack. The threat R Ransomware is known to have an association with Poop Ransomware potentially from its creators being within the same group of cybercrooks and hackers. Computer users that avoid paying the Poop Ransomware ransom or contacting the criminals are taking the right decision because accepting the criminals' conditions only makes computer users more vulnerable to attacks and does not guarantee that the criminals will respond and restore the affected data. Having file backups is the best protection against threats like the Poop Ransomware.
SpyHunter Detects & Remove Poop Ransomware
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 426834e40d3f7f2966fa8a27d64bd091 | 5 |
| 2. | READ_IT.txt |

