Pickles Ransomware
The Pickles Ransomware is an encryption ransomware Trojan that was uncovered almost at the same time as the PyL33T Ransomware. There are numerous similarities between these two threats. They are both programmed using Python, which is not that common when it comes to ransomware Trojans. The main difference between them is that the Pickles Ransomware seems to target individual computer users and home computers, while PyL33T was created to target corporate networks, Web servers, and other high profile targets apparently. Although there is no definite proof that the same team of cyber crooks created both, there is circumstantial evidence to suggest a connection. The Pickles Ransomware has many of the advantages that are provided by using the Python programming language, such as easy updates and the ability to expand with relatively little trouble when compared to other threats programmed using other computer languages.
Table of Contents
The Threat Presented by the Pickles Ransomware
The Pickles Ransomware was first observed online among numerous samples. The Pickles Ransomware receives its name because an initial version of this threat used the password 'pickles' for the decryptor used to recover the files affected on the attack. This meant that recovering from infections involving the first version of the Pickles Ransomware was a simple matter of entering the string 'pickles' into the message that pops out when the victims open a python script file dropped on their computers by the Pickles Ransomware. These early versions of the Pickles Ransomware were first observed on an online scanner, which is a typical way in which the con artists test their threat creations to ensure that they can avoid detection by anti-virus software. Since the initial release of the Pickles Ransomware, a stronger version that uses a more effective encryption technique and a different password will probably be released.
Some Particularities of the Pickles Ransomware
In its attack, the Pickles Ransomware uses a combination of the AES and RSA encryption to encrypt the victim's files. The Pickles Ransomware will target files on the victim's drives, as well as files on external memory devices connected to the infected computer and files located in network directories. The Pickles Ransomware will infect most commonly used versions of Windows. The files that have been encrypted in the Pickles Ransomware attack will have the file extension '.EnCrYpTeD' added to the end of the file name, making it simple to realize which files have been encrypted in the attack. Apart from this, the file's name also will be changed into a randomly generated string. The Pickles Ransomware will drop a text file named 'READ_ME_TO_DECRYPT.txt' on the infected computer's Desktop. This text file contains the Pickles Ransomware's ransom note, which instructs the victim on the attack, as well as the instructions on how to pay. The following are the contents of the Pickles Ransomware ransom note:
'Your files have been locked with AES strong encryption. How to decrypt your files:
1. send one bitcoin to: ABCDEFGHIJKLMNOPQRSTUVWXYZ123456789
2. After sending bitcoin, send email to randonuanonymous@gmail.com containing the following code: 3614e3639c0a98b1006a5Offe5744f054cf4499592feSeflb339601208e80066
3. After receiving bitcoin and required code, you will be given your decrypt password
4. Find to_decrypt.py, double-click, enter the password
Decryption requires Python installed
You have 72 hours to comply, or your decrypt password will be permanently destroyed!
How to buy bitcoin: https://wm.coinbase.
GOOD LUCK!!'
Dealing with a Pickles Ransomware Attack
PC security analysts strongly advise computer users against paying the Pickles Ransomware ransom. In most cases, computer users can unlock their files with the password 'pickles' since an updated version of the Pickles Ransomware is either not in a wide distribution currently, or has been released under a different name. The best protection against threats like the Pickles Ransomware is to have backups of all files, especially since most ransomware Trojans that use a similar attack cannot be dealt with in such a simple way. If computer users can recover their files from a backup copy, then the people responsible for the encryption Trojan attack no longer have leverage that allows them to demand ransom payments from the victims.
SpyHunter Detects & Remove Pickles Ransomware
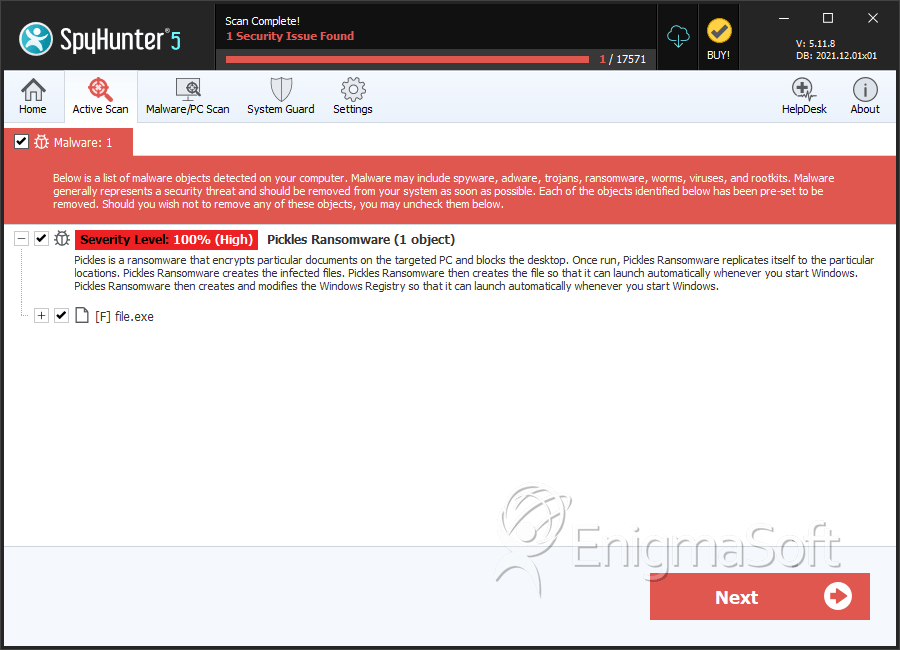
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 8102289c4bb4f0683f56701911252b11 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.