PedCont Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | June 6, 2018 |
| OS(es) Affected: | Windows |
The PedCont Ransomware is an encryption ransomware Trojan. The PedCont Ransomware seems to combine elements of the infamous police ransomware, claiming to be part of a law enforcement operation, like traditional encryption ransomware Trojans. Overall, though, the PedCont Ransomware seems to be a low-quality threat with very little to differentiate it from the many encryption ransomware Trojans in use to extort computer users currently. The PedCont Ransomware takes the victim's files hostage and then demands a ransom payment to supposedly restore the victim's files. However, in most cases, the criminals will not help the victims restore their files so that paying these fees or communicating with the criminals is of no use.
Table of Contents
The Lies Contained in the PedCont Ransomware’s Fake Warning
The PedCont Ransomware displays a large fake warning on the victim's computer claiming that the victim is being prosecuted for browsing forbidden online content on the Dark Web. The PedCont Ransomware then turns the victim's screen black and fails to respond. This may be part of a measure used by the PedCont Ransomware when being observed on virtual machines, however, so that it may not be an aspect of the PedCont Ransomware attack present on attacks on the wider public. The PedCont Ransomware encrypts the victim's files in the same way as most encryption ransomware Trojans active today. The following are the file kinds that threats like the PedCont Ransomware will target usually:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
The full text of the PedCont Ransomware ransom note, which demands the payment and threatens the victim by making up a phony story about the victim's files being 'stored on an external server' reads:
'!!! Attention !!! – Please read this immediately:
Dear potential criminal,
- Due to you actively seeking out [illegal digital content] or similarly illegal content on the Deep Web, you have been infected with our ransomware called PedCont.
- WHAT HAS ALREADY HAPPENED:
All of your sensitive data, location and files – pictures, videos, documents, etc. – have been auto-collected and saved to an external server and will be stored & protected for the next 72 hours (counting from the first time you see this message). If we do not receive any cooperation from your part once the time is up, international authorities WILL be contacted and sent detailed information about everything that we have scraped from your computer.
While it is no longer necessary for this program to stay on your computer, should you wish to prevent legal prosecution and safely get rid of our records, do NOT manually remove it, but instead follow the steps listed below.
-WHAT WE REQUIRE OF YOU'
The PedCont Ransomware's ransom note continues by displaying instructions about how to purchase and transfer cryptocurrency.
Dealing with a PedCont Ransomware Infection
Dealing with The PedCont Ransomware attack involves taking steps to restore your files after removing the PedCont Ransomware threat itself. Removing the PedCont Ransomware is relatively simple, and can be done with a reliable security program. However, when the PedCont Ransomware is done with the encryption of the files, they only can be restored by replacing them with file backups, which should be stored on the cloud or an external memory device.
SpyHunter Detects & Remove PedCont Ransomware
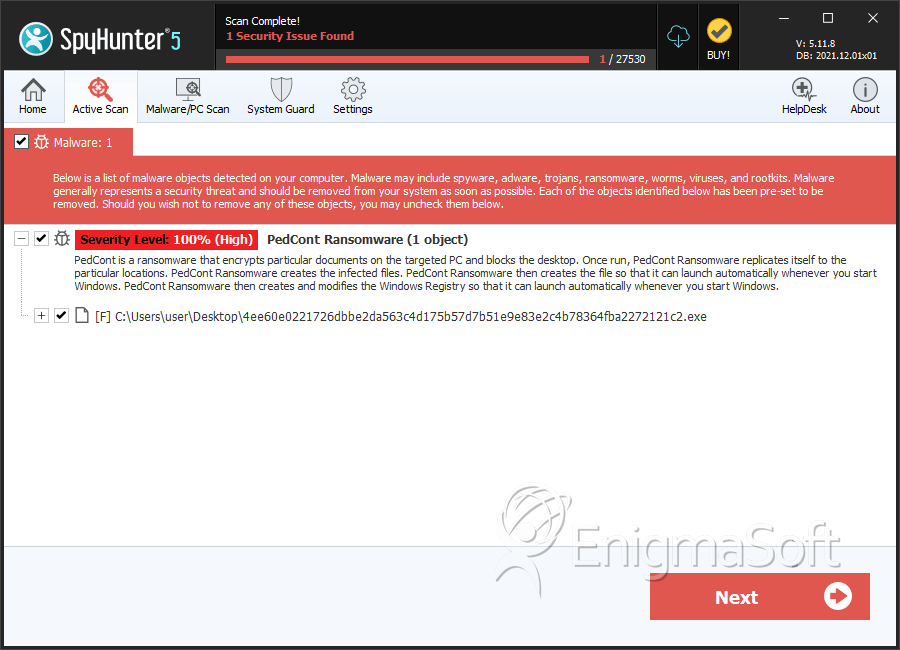
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 4ee60e0221726dbbe2da563c4d175b57d7b51e9e83e2c4b78364fba2272121c2.exe | 60ef1e90b98658a70ed1a9349b0e83b6 | 1 |

