Pay2Key Ransomware
The Pay2Key Ransomware is a new malware strain compiled in late-October that started attacking businesses in early-November, 2020. The crooks in charge acquire early access to the target’s network, only to infect it at a later time. The encryption process may take up to 60 minutes, while the ransom amount varies from 7 to 9 BTC (currently worth between $130,000 and $170,000). So far, Pay2Key has only struck companies based in the State of Israel.
The actors behind the Pay2Key Ransomware most likely exploit security flaws in Remote Desktop (RDP) connections to manually plant the payload within the targeted network. The attacks usually take place after midnight to evade potential detection. Rather than get a grip on the entire network, Pay2Key randomly picks a single network-connected PC, plants the ransomware payload “Cobalt.Client.exe” and a configuration file called Config.ini which outlines a server and a port. Thus, the infected machine now serves as a Pivot/Proxy gateway to the entire network. In other words, the compromised machine acts as an intermediary between the crooks’ C&C server and the breached network. To spread the Pay2Key Ransomware laterally across the network, the malware actors at play must first run the Connect.exe tool by exploiting the PsExec command-line tool. Altogether, the Pay2Key payload lands on C:\Windows\Temp\[organization-name]tmp\Cobalt.Client.exe, where [organization-name] is the name of the targeted business organization. While the configuration .ini file indicates Server and Port, it also reveals that the Pay2Key ransomware does not communicate with an external C&C server — the IP of the Pivot/Proxy machine acts as one instead. A setup of that kind makes it harder for security researchers to locate the C&C server as it is placed on just one of the networked machines. If the affected network is huge, finding patient zero may resemble looking for a needle in a haystack.
At present, no party has taken responsibility for the Pay2Key ransomware attacks in Israel. Judging from the clumsy coding style, however, researchers are prone to think the crooks may not necessarily be English natives.
This Week In Malware Episode 33 Part 3: Pay2Key Ransomware Spreading & Encrypting Networks In Just An Hour
Still A Work In Progress
The hackers who wrote the Pay2Key ransomware code relied heavily on the C++ language, the MSVC++ 2015 compiler, and Object-Oriented Programming (OOP), combined with the Boost library. The main files of the threat are an executable that carries the ransomware called Cobalt.Client.exe and a config file that contains the specific parameters for the 'Server' and 'Port.' The attackers also drop the ConnectPC application used to create the Pivot/Proxy server. After the initial setup, Pay2Key will wait for additional commands to be sent by the attackers. The functionality of the threat is fairly flexible due to the varying commands the hackers can use to specify:
- which file types to encrypt
- the name of the file carrying the ransom note
- the contents of the ransom note itself
- the extension appended to the encrypted files.
In most cases, the extension was '.pay2key' while the name of the ransom file was modified to include the name of the infected organization with the templated being [ORGANIZATION]_MESSAGE.TXT. The ransom note can contain a specially created ASCII-art of the victims' name. Here’s what the ransom note of a typical Pay2Key infection usually says:
PAY2KEY
Hello [organization_name] users!
Congratulations!
Your entire network and all your informations such as computers / employees information / user folders / servers / file-servers / applications/ databases/etc …… in your network has been successfully encrypted!
Some of your important information dumped and ready to leak, in case we can’t make a good deal!
Don’t modify encrypted files or you can damage them and decryption will be impossible!
Don’t try unofficial decryptors to recover your files or you can damage them and decryption will be impossible!
There is only ONE possible way to get back your files! Pay and contact to receive your special decryptor!
You should pay 7 BTC to receive official decryptor and easily recover your files. [classified text] special decryptor is now ready and waiting for your payment, let’s do it!
You can send 4 random files from any computers and receive decrypted data, just as a proof that works!
Your User ID is:
Your Network ID
Note! Offer available till XX/YY/ZZZZ. If you do not pay on time, price will be doubled!
E-mail:
pay2key@tuta.io
pay2key@pm.me
Keybase:
Pay2Key
Here's what the actual note looks like:
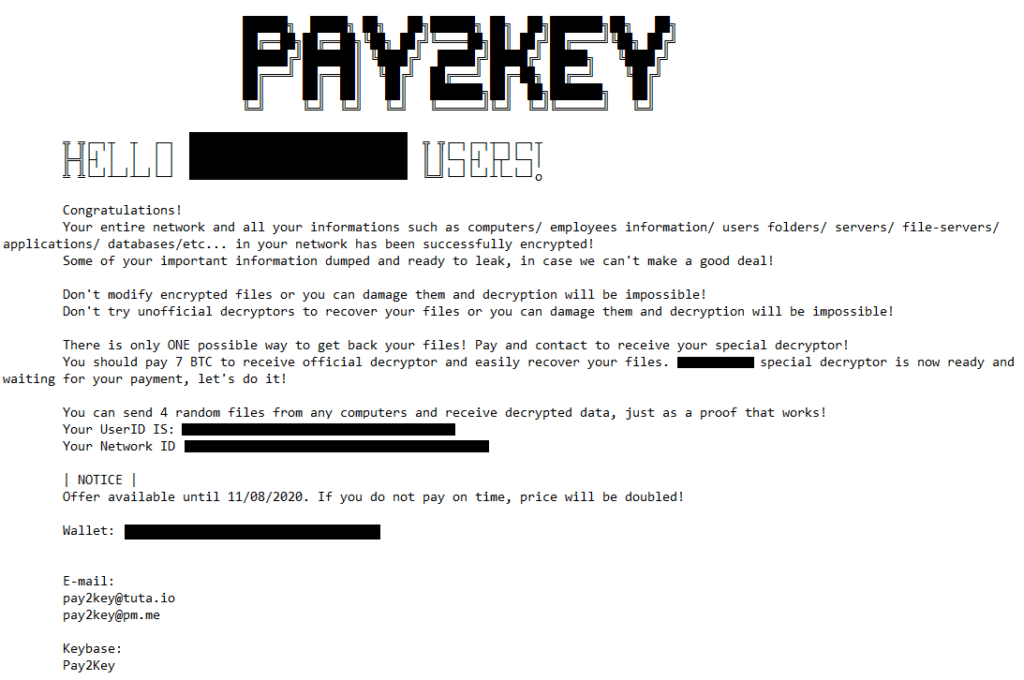
Image title: Pay2Key Ransom note
Source: CheckPoint
Pay2Key uses a combined AES / RSA encryption algorithm. If there is no Internet connection or the C&C servers are down, file encryption will not commence as the threat needs to receive an RSA public key at runtime from the servers.
After analyzing several Pay2Key ransomware strains, it becomes evident that the threat is still being polished as its developers are continually adding more features on the go. Newer versions, for example, arrive with a cleaning mechanism allowing them to cover their tracks completely before system restart.
The hackers behind Pay2Key appear to be focused on Israeli targets for now, but the sophistication of their malware tools and the attack chain of the campaigns shows that they could expand their operations on a global level if they felt the urge to do so.

