Parisher Ransomware
The Parisher Ransomware is an encryption Trojan that is tailored to encrypt files stored on server machines. The Parisher Ransomware is a variant of the Mobef Ransomware and features the same level of sophistication used to develop threats like KimcilWare and SamSam Ransomware. The Parisher Ransomware is named after one of the emails its victims are welcomed to contact for payment instructions—parisher@protonmail.com. The campaign to distribute the Parisher Ransomware involves spam email, corrupted plug-ins for WordPress, and online store platforms like Shopify, WooCommerce and Magento. There are cases, where the Parisher Ransomware is introduced to systems via compromised RDP (Remote Desktop Connection) connections as well.
Machines powered by the Windows Server 2003, 2008, 2012, and 2016 are vulnerable to attacks by the Parisher Ransomware. Malware investigators report that the Parisher Ransomware is programmed to encrypt data outside of system directories and avoid Windows services. The Parisher Ransomware is known to use industry grade encryption to lock data containers in the following formats:
.PNG, .PSD, .PSPIMAGE, .TGA, .THM, .TIF, .TIFF, .YUV, .AI, .EPS, .PS, .SVG, .INDD, .PCT, .PDF, .XLR, .XLS, .XLSX, .ACCDB, .DB, .DBF, .MDB, .PDB, .SQL, .APK, .APP, .BAT, .CGI, .COM, .EXE, .GADGET, .JAR, .PIF, .WSF, .DEM, .GAM, .NES, .ROM, .SAV, .DWG, .DXF, .GPX, .KML, .KMZ, .ASP, .ASPX, .CER, .CFM, .CSR, .CSS, .HTM, .HTML, .JS, .JSP, .PHP, .RSS, .XHTML, .DOC, .DOCX, .LOG, .MSG, .ODT, .PAGES, .RTF, .TEX, .TXT, .WPD, .WPS, .CSV, .DAT, .GED, .KEY, .KEYCHAIN, .PPS, .PPT, .PPTX, .INI, .PRF, .HQX, .MIM, .UUE, .7Z, .CBR, .DEB, .GZ, .PKG, .RAR, .RPM, .SITX, .TAR.GZ, .ZIP, .ZIPX, .BIN, .CUE, .DMG, .ISO, .MDF, .TOAST, .VCD, .SDF, .TAR, .TAX2014, .TAX2015, .VCF, .XML, .AIF, .IFF, .M3U, .M4A, .MID, .MP3, .MPA, .WAV, .WMA, .3G2, .3GP, .ASF, .AVI, .FLV, .M4V, .MOV, .MP4, .MPG, .RM, .SRT, .SWF, .VOB, .WMV, .3D, .3DM, .3DS, .MAX, .OBJ, R.BMP, .DDS, .GIF, .JPG,.CRX, .PLUGIN, .FNT, .FON, .OTF, .TTF, .CAB, .CPL, .CUR, .DESKTHEMEPACK, .DLL, .DMP, .DRV, .ICNS, .ICO, .LNK, .SYS, .CFG.
Affected users are provided with the ransom note in a TXT file that may feature the title '1NFORMAT1ONFOR.YOU' and 'HELLO.0MG' depending on the strand of the Parisher Ransomware. Evidence suggests that the Parisher Ransomware is programmed to store the public encryption key on the infected system. We have seen the Parisher Ransomware using files like 'ENCRYPT1ON.KEY123' and 'LOKMANN.KEY993,' which may contain 512 bytes long key. Additionally, the Parisher Ransomware will leave a list with the encrypted files on the PC that can be found in the Windows directory packed as [6 digit number].log. As stated above the ransom message may not retain a static name and users may find 'ENCRYPT1ON.KEY123' and 'LOKMANN.KEY993' on their computers. Either way, the note is standardized among variants of the Parisher Ransomware and reads as follow:
'ID:[6 digit number]
PC:[name of the machine]
USER:Administrator
=========
Hello there. I can decrypt your files.
Email me: parisher@protonmail.com
In case you don't get a reply, please email me here*:
parisher@inbox.lv, parisher@mail.bg, parisher@india.com
* check your junk/spam folder first though 🙂
These files have been encrypted (please, keep this .log): C:\Windows\[6 digit number].log'
Server administrators might consider writing to any of the following emails: parisher@mail.bg; parisher@india.com; parisher@protonmail.com and parisher@inbox.lv. However, paying the ransom of 5 Bitcoins (3144 USD) is not advisable because the operators of the Parisher Ransomware are not likely to provide a decryptor. Most server administrators should be able to recover data using backups and services like Google Drive and Microsoft's OneDrive. Users may wish to use a trusted anti-malware solution to clean the systems affected by the Parisher Ransomware.
SpyHunter Detects & Remove Parisher Ransomware
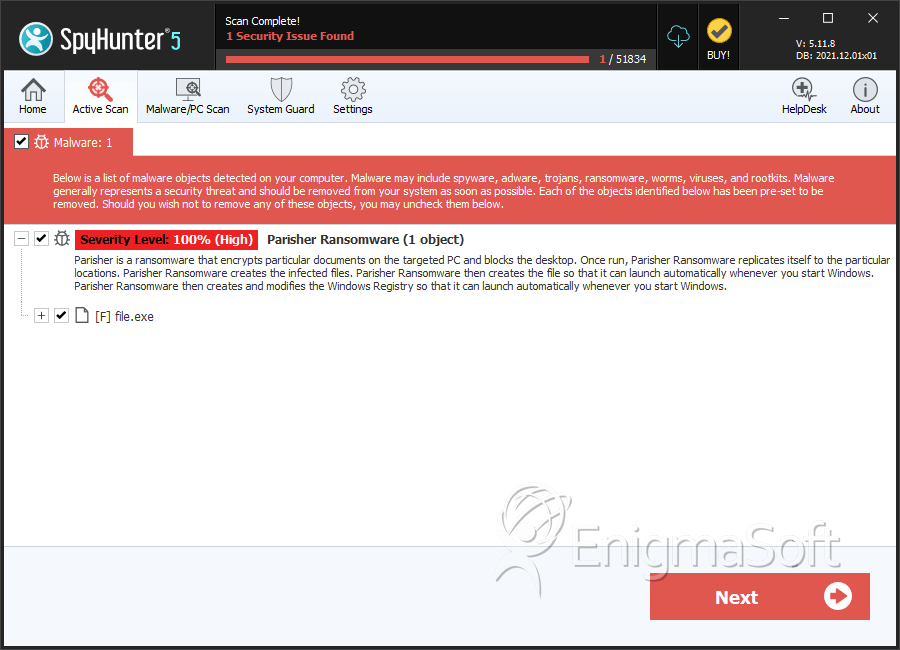
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 7d082fdf8f7a306c9a4fa65d73453f43 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.