PainLocker Ransomware
The PainLocker Ransomware is a ransomware Trojan that was first observed on May 29, 2018. The PainLocker Ransomware is a variant of ransomware Trojans that already existed before and had been released earlier in 2018. Some possible precursors of the PainLocker Ransomware include the Everbe@airmail.cc Ransomware and the Embrace Ransomware. The PainLocker Ransomware, like its predecessors, is commonly delivered to victims through corrupted Microsoft Word documents attached to spam email messages, containing damaged embedded scripts that download and install the PainLocker Ransomware onto the victim's computer. The PainLocker Ransomware and similar threats may be delivered via spam email messages containing file attachments and social engineering techniques to make the victim believe that the file attachment is an invoice, receipt or another legitimate file.
Table of Contents
How the PainLocker Ransomware Trojan will Affect Your Files
The PainLocker Ransomware will run as a randomly named executable file. One version of the PainLocker Ransomware shows up as 'b047a4ab1726fe7414484493c60d5870.exe.@' on the infected computer's Task Manager, for example. Once installed, the PainLocker Ransomware will target a wide variety of the user-generated file types, which may include numerous media file types, documents such as Word documents and spreadsheets, as well as configuration files, archives, and databases. The following are the files that are commonly targeted in attacks like the PainLocker Ransomware:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
The PainLocker Ransomware will add the file extension '.pain' to each file affected by the attack. The PainLocker Ransomware also will drop a ransom note onto the victim's computer. This file takes the form of a text file named '!=How_recovery_files=!.tx,' which is opened with the victim's default text editor. This ransom note contains the text:
'PAIN LOCKER
Hello, dear friend!
All your files have been ENCRYPTED
Do you really want to restore your files?
Write to our email - pain@cock.lu or pain@airmail.cc
And tells us your unique ID - [random characters]'
This is a fairly typical ransom note for these attacks, which alerts the victim of the infection and then demands that the victim contact the criminals for the decryption key. It is recommended that computer users refrain from doing this. The criminals will not respond helpfully, demanding a large ransom in exchange for the decryption key and failing to deliver after the payment is carried out. Even if they do help the victim recover the files, paying these ransoms allows criminals to continue creating and financing these attacks, making the victim vulnerable to additional infections.
Protecting Your Data from Threats Like the PainLocker Ransomware
The best protection against the PainLocker Ransomware is to have file backups stored on the cloud or an offline device. Unfortunately, the PainLocker Ransomware uses a strong encryption method, which makes the affected files unrecoverable. Because of this, having the ability to restore the files affected by the attack from a backup copy is the best measure against threats like the PainLocker Ransomware. Apart from file backups, a proper security program that is fully up-to-date should be used to prevent these attacks and stop threats like the PainLocker Ransomware before they are installed.
SpyHunter Detects & Remove PainLocker Ransomware
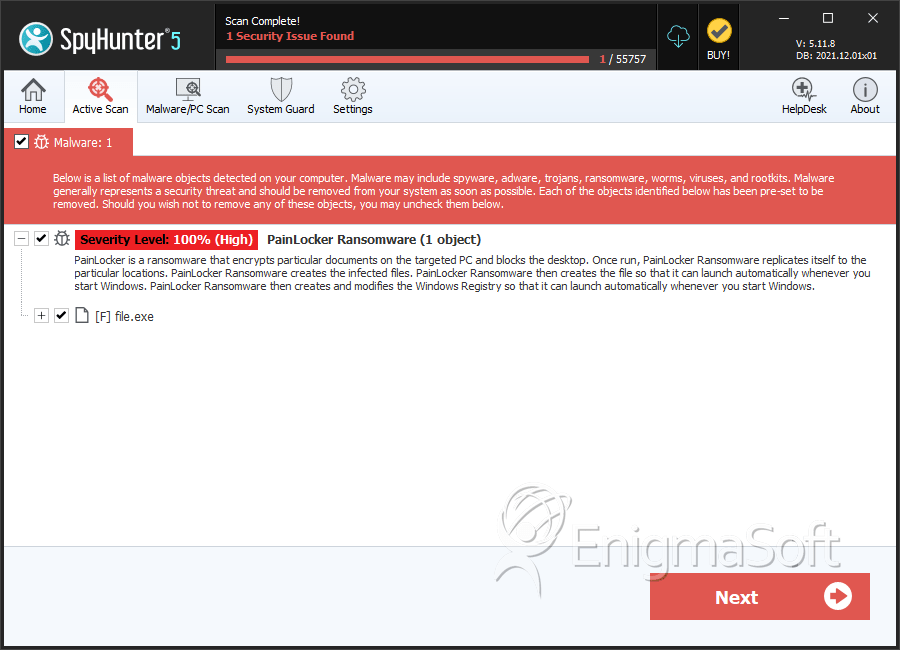
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 01936ee49480e63078dbbd59065ef85f | 0 |
| 2. | file.exe | b047a4ab1726fe7414484493c60d5870 | 0 |

