PadCrypt Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 14 |
| First Seen: | February 17, 2016 |
| Last Seen: | March 15, 2020 |
| OS(es) Affected: | Windows |
The PadCrypt Ransomware is a ransomware Trojan that has a new 'feature': the PadCrypt Ransomware allows its victims to receive live 'support' via a chat window. Ransomware infections have become gradually more sophisticated over the years. Considering the large amounts of money that are generated from infections like the PadCrypt Ransomware, it is not surprising that con artists are starting to include more advanced features into their threats that allow them to increase the potential revenue from ransom payments. The PadCrypt Ransomware and its various variants not only provide a live support chat window; they also include an uninstaller feature!
Table of Contents
The PadCrypt Ransomware may be a Descendant of the CrytoWall Family
PC security analysts believe that the PadCrypt Ransomware was created by building on the code of an older threat from the well known CryptoWall family of ransomware Trojans. The PadCrypt Ransomware may spread using corrupted PDF email attachments, although it is still unclear exactly what email message tactics have been associated with the PadCrypt Ransomware. Corrupted email messages associated with the PadCrypt Ransomware may include an executable file that has been zipped and disguised to look like a PDF file. Once the compromised 'PDF' file is opened, the PadCrypt Ransomware infects the victim's computer, encrypting files on the infected hard drive, deleting Shadow Volume copies of encrypted files, and blocking any potential system restore or recovery options from functioning. Once the PadCrypt Ransomware has completed its attacks, the victim can only restore the files from a backup stored in an external location, or pay the ransom amount that the PadCrypt Ransomware demands.
The PadCrypt Ransomware Allows Victims to Chat with Its Operators
The PadCrypt Ransomware will demand the ransom by dropping image, text, and HTML files on the directories where the PadCrypt Ransomware has encrypted files. The PadCrypt Ransomware also will display pop-up windows containing the ransom message, which requests the payment of 0.8 Bitcoin (averaging about $350, depending on the current Bitcoin exchange, which can fluctuate substantially). The PadCrypt Ransomware pop-up window has caught the attention of PC security researchers because the PadCrypt Ransomware includes a link that is marked 'Live Chat.' When computer users click on this link, a live support chat window opens, which allows victims to contact the operators of the PadCrypt Ransomware. However, since the PadCrypt Ransomware Command and Control server is not currently operational, this feature does not seem to work.
The PadCrypt Ransomware’s Bizarre Features
Some versions of the PadCrypt Ransomware's predecessor, Cryptowall, also included live support. However, Cryptowall's support was included in the website where its ransom was paid. In the case of the PadCrypt Ransomware, the support works directly from the victim's computer, not requiring the installation of TOR or the victim's Web browser. Another bizarre feature associated with the PadCrypt Ransomware is that it includes an uninstall feature. This uninstaller, a file named Unistl.exe, does not do anything to decrypt the affected data. However, it does uninstall the PadCrypt Ransomware infection. Although it seems counter-intuitive to include an uninstaller to a threat infection, ransomware like the PadCrypt Ransomware encrypts the victim's files and does not need to stay installed. The most probable reason for the PadCrypt Ransomware's uninstaller and live chat feature is that the con artists may have used templates and recycled code to create the PadCrypt Ransomware, which may have generated these features automatically.
Counteracting the PadCrypt Ransomware
Malware researchers advise against paying the PadCrypt Ransomware's ransom amount. There is no guarantee that the con artists will deliver the decryption key, and paying the ransom only serves to facilitate the production of additional ransomware infections. Instead, it is important to establish a culture of backing up all important data regularly. Once the backup of all files becomes a regular thing among computer users, ransomware like the PadCrypt Ransomware will merely be an annoyance and become completely ineffective.
SpyHunter Detects & Remove PadCrypt Ransomware
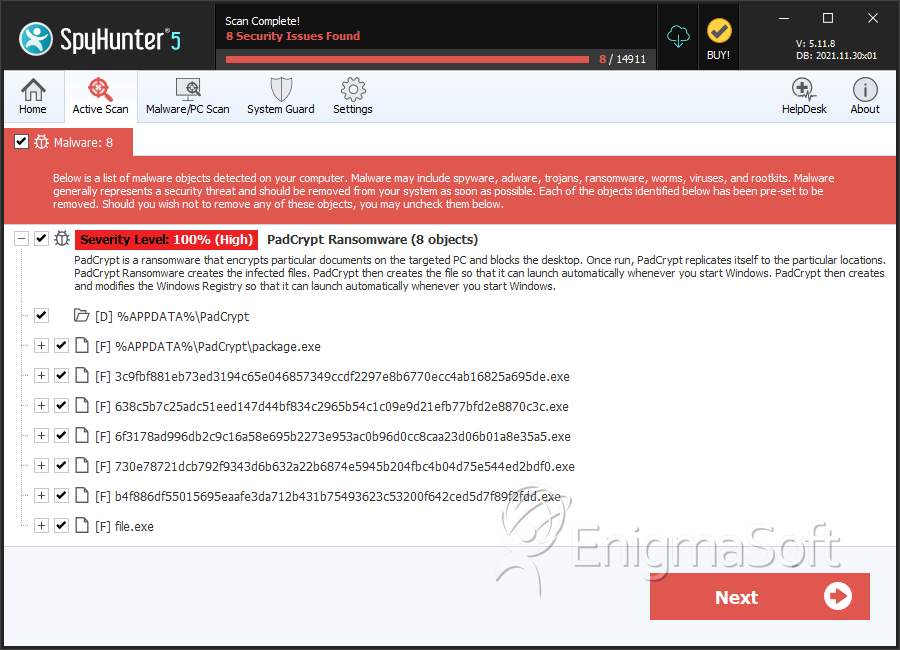
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | package.exe | eeb4d8fab06a892a3862a251864719a7 | 1 |
| 2. | package.exe | 786d201145aa227e816c2c480ca24e23 | 1 |
| 3. | package.exe | a34632d75f4eba0fb0dd90f77db2f90d | 1 |
| 4. | package.exe | 04cb6917c78cbba1824a2bf57a26f019 | 1 |
| 5. | package.exe | 17822a81505e56b8b695b537a42a7583 | 1 |
| 6. | package.exe | 0116f296640ef8e3b43227ac0028518a | 1 |
| 7. | file.exe | 93d2ff0ea17d747ad55c01c9a71529d8 | 1 |
| 8. | 3c9fbf881eb73ed3194c65e046857349ccdf2297e8b6770ecc4ab16825a695de.exe | 7ed0c7cd88bf661ecef8abec2ff310aa | 0 |
| 9. | 638c5b7c25adc51eed147d44bf834c2965b54c1c09e9d21efb77bfd2e8870c3c.exe | 267757370ff7542c4900dc3f6069f7f6 | 0 |
| 10. | 6f3178ad996db2c9c16a58e695b2273e953ac0b96d0cc8caa23d06b01a8e35a5.exe | 681e7ad03c4f41d110d32d175cc14bab | 0 |
| 11. | 730e78721dcb792f9343d6b632a22b6874e5945b204fbc4b04d75e544ed2bdf0.exe | 9dbeff5ac47058fb8fe61c3948cc26ca | 0 |
| 12. | b4f886df55015695eaafe3da712b431b75493623c53200f642ced5d7f89f2fdd.exe | 84aa7c891cd5ae136117317f451819c0 | 0 |
| 13. | file.exe | 841453bdff5905f17c0074a65b263893 | 0 |
| 14. | file.exe | 3e1e3f83032c2237d0df9e45ccb52f3a | 0 |
Directories
PadCrypt Ransomware may create the following directory or directories:
| %APPDATA%\PadCrypt |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.