ORX-Locker
ORX-Locker is a ransomware infection. Although the ORX-Locker attack itself is not different from most other ransomware lockers, ORX-Locker is especially threatening because ORX-Locker is being offered as an easy to use service that nearly anyone can implement. Third parties can take advantage of Ransomware as a Service (RaaS) sites that have sprung up on the Darknet. ORX-Locker is one of these types of infections, which are offered on underground forums and websites. ORX-Locker may allow anyone, regardless of knowledge or resources, to create ransomware attacks in order to infect computers. When victims of ORX-Locker pay the ransom to regain access to their files, the providers of ORX-Locker retain a portion of the ransom amount. This allows the creators of ORX-Locker to spread their threat infection without any additional effort. ORX-Locker is not the first RaaS known to security researchers. The first, uncovered in May of 2015, was named Tox, and was taken down after its creators expressed remorse for the path it had taken. ORX-Locker builds on Tox, with additional obfuscation and evasion methods, and expanding on its infrastructure and communication methods. When Tox was taken down, PC security researchers predicted correctly that new RaaS offerings would appear, containing more sophisticated ransomware infections to their clients.
Table of Contents
What are the Supposed Advantages of ORX-Locker
The first reports of ORX-Locker appeared on August 25, 2015, when a post on an underground forum, posted by a user named 'orxteam' advertised this RaaS. ORX-Locker is distributed on a Darknet website that only requires registration. When visiting this website, users only need to enter an ID number, a ransom price (with a minimum of $75) and click on a button marked 'build EXE.' The ORX-Locker variant is created automatically. Users can check up on the stats for their threats, allowing them to observe how many computers have become infected, collect information about the infected computers, time and dates of the infections, profits generated from each computer, etc. Users can also check on their wallet to withdraw the earnings from each infection. The makers of ORX-Locker even provide support to their users.
The ORX-Locker Attack
When the threat is executed, it connects to various IP addresses, including several University IP addresses. The following are some of the IP addresses that may be linked to ORX-Locker:
130[.]75[.]81[.]251 – Leibniz University of Hanover
130[.]149[.]200[.]12 – Technical University of Berlin
171[.]25[.]193[.]9 – DFRI (Swedish non-profit and non-party organization working for digital rights)
199[.]254[.]238[.]52 – Riseup (Riseup provides online communication tools for people and groups working on social change).
It is presumed that most IP addresses associated with ORX-Locker attacks belong to computers or networks that have been compromised by the makers of ORX-Locker. ORX-Locker uses TOR to transmit its data.
The ORX-Locker attack, like most ransomware lockers, involves locking all of the victim's files, changing their extension in this case to .LOCKED and deleting the original files and shadow copies. Victims of ORX-Locker are faced with a pop-up message and an instruction file on their desktop. The file, an HTML file that opens in the victim's Web browser, will give the victim a payment ID and a link to the onion network website so the victim can pay in order to recover access to the encrypted files.
Dealing with ORX-Locker
Unfortunately, once ORX-Locker has locked the victim's files, it is nearly impossible to recover them without the decryption key. Because of this, the best protection against ORX-Locker is to backup all files (or at least all important files) using an external device or the cloud. This way, in the event of a ransomware attack like ORX-Locker, victims can recover their files from this backup instead of paying ORX-Locker's ransom. PC security analysts advise against paying the ORX-Locker ransom since there is no guarantee that the people responsible for this attack will restore the encrypted files even if the ransom is paid.
SpyHunter Detects & Remove ORX-Locker
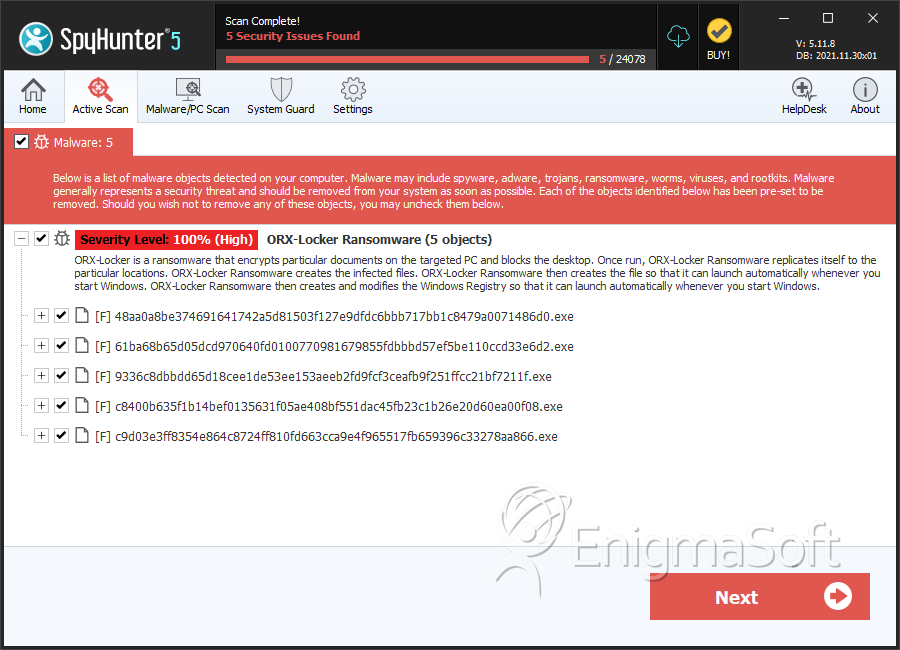
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 48aa0a8be374691641742a5d81503f127e9dfdc6bbb717bb1c8479a0071486d0.exe | d6ed4d4e8b1a95a224ebdd54529b3751 | 0 |
| 2. | 61ba68b65d05dcd970640fd0100770981679855fdbbbd57ef5be110ccd33e6d2.exe | b3b21bca70389666593960dc1d686189 | 0 |
| 3. | 9336c8dbbdd65d18cee1de53ee153aeeb2fd9fcf3ceafb9f251ffcc21bf7211f.exe | 1914724aeea3ca954322053dd883b14a | 0 |
| 4. | c8400b635f1b14bef0135631f05ae408bf551dac45fb23c1b26e20d60ea00f08.exe | 89e1efdc766e9c7d41305566993ba800 | 0 |
| 5. | c9d03e3ff8354e864c8724ff810fd663cca9e4f965517fb659396c33278aa866.exe | 942f6d0aadb9697d300e47eafb5c62dd | 0 |

