Nymaim Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 13,310 |
| First Seen: | July 10, 2013 |
| Last Seen: | January 20, 2021 |
| OS(es) Affected: | Windows |
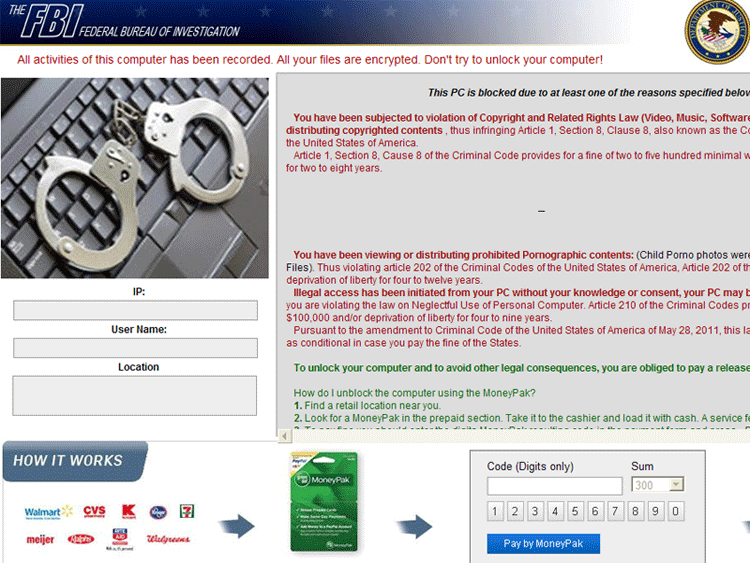
Nymaim Ransomware Image
The Nymaim Ransomware family is a typical example of this kind of scam. While there is little to differentiate the Nymaim Ransomware from other ransomware families, this particular ransomware Trojan has attracted the attention of PC security researchers because the Nymaim Ransomware is part of the payload of Darkleech, a high profile malware campaign that has affected various important targets around the world. If your computer has been infected by the Nymaim Ransomware Trojan, you may not be able to access your operating system or files. To remove the Nymaim Ransomware infection from your computer and regain access to your files and operating system, ESG security researchers advise the use of alternate start-up methods to gain access to your security software. A fully updated anti-malware application should be able to remove a Nymaim Ransomware infection and restore access to the infected computer.
Table of Contents
The Modus Operandi of the Nymaim Ransomware
The Nymaim Ransomware uses a known social engineering scam to trick inexperienced computer users into paying a ransom. The Nymaim Ransomware scam has the following steps:
- Initially, the Nymaim Ransomware infection enters a computer with the help of an exploit kit or through known social engineering tactics. The Nymaim Ransomware is closely related to the Darkleech infection which uses the Black Hole Exploit Kit to install the Nymaim Ransomware Trojan on the victim's computer.
- Once the Nymaim Ransomware Trojan is installed, the Nymaim Ransomware blocks all access to the victim's computer, displaying a full screen message upon start-up. This message indicates that the victim's computer was blocked as part of a police action due to the infected computer's involvement in supposed illegal activities. The Nymaim Ransomware message will threaten the victim with years of jail time and thousands of Euros in fines unless the victim pays a supposed police 'fine' through an online payment service. This message will usually be tailored to the infected computer's geographical location, written in the victim's language and claiming to have been sent by a local police agency.
It is important to note that paying the Nymaim Ransomware Trojan's fine will not remove this threat from your computer or restore your access to your files. In fact, the only way to restore your access to your computer is to remove the Nymaim Ransomware Trojan completely with a reliable anti-malware program.
Nymaim Has Evolved Into a Flexible Malware Dropper
Since its initial appearance, Nymaim has been documented in relationship with other malware threats. In 2016, for example, it was distributed via spam email campaigns and webinjects along with Ursnif banking Trojan. During the following years, Nymaim has evolved into a sophisticated malware downloader that is capable of dropping a range of data stealing, system profiling or file locking tools on target machines. In this current incarnation, Nymaim has already participated in several global campaigns, as well as in attacks targeting particular countries in Europe and North America.
Threat actors typically distribute Nymaim disguised as a regular app or file, for example, often spam emails come with a subject line "Job Application" which is intended to trick users into opening the attached file. Due to its capabilities of a malware dropper, the presence of Nymaim can cause serious issues on a computer. If it installs an encryption-type of a virus, the user's data will be permanently locked and inaccessible. On the other hand, info-stealing threats record bank account data, login credentials, browsing history, keystrokes, and other kinds of sensitive data. Such activities put user privacy at risk and can result in financial losses and even identity theft.
Nymaim can also distribute exploit kits that are able to connect the infected computer to a botnet, which leads to the misuse of system resources, usually stealthy crypto currency mining. It does not need to mention that the Nymaim malware threat should be removed immediately from the infected computer with the help of a reputable anti-malware solution. Subsequently, all affected PC users are advised to change their passwords for all their online accounts.
Nymaim is Being Dropped by a New Variant of Emotet
In February 2019, Nymaim Ransomware emerged again in the form of a malware downloader, this time targeting the hospitality sector. Researchers found out that a new variant of the well-known Emotet Trojan is distributing Nymaim malware, which in turn, once installed on a machine, tends to download the Nozelesn ransomware.
Researchers made that discovery on the basis of the analysis of 580 similar file attachments injected with Emotet and reported in the period between January 9, 2019, and February 7, 2019. Using Root Cause Chain analysis (RCA), suspicious files called "How_Fix_Nozelesn_files.htm" were found on an infected server.
The analyzed Emotet samples are distributed through malicious Microsoft Word doc attachments, which once opened, download the PowerShell.exe on the target system, connect to various corrupted IP addresses, and then create another malicious executable file on the system. The link between the Nozelesn ransomware and Nymaim was detected by researchers already in 2018 when it was found that Nymaim uses a fileless execution technique to load the ransomware to the computer's memory.
Although the Nymaim malware has been around for several years now, it has a unique configuration file format and many of its aspects and features are still not completely understood by cyber security researchers. That includes the ownership of the virus and its availability to threat actors. Nymaim is an illustration of a general malware trend that focuses on designing persistent, non-destructive infections that stay unnoticed on a machine for long periods of time with the purpose of collecting information, while at the same time, allowing attackers the flexibility to download additional malware at their choice.
SpyHunter Detects & Remove Nymaim Ransomware
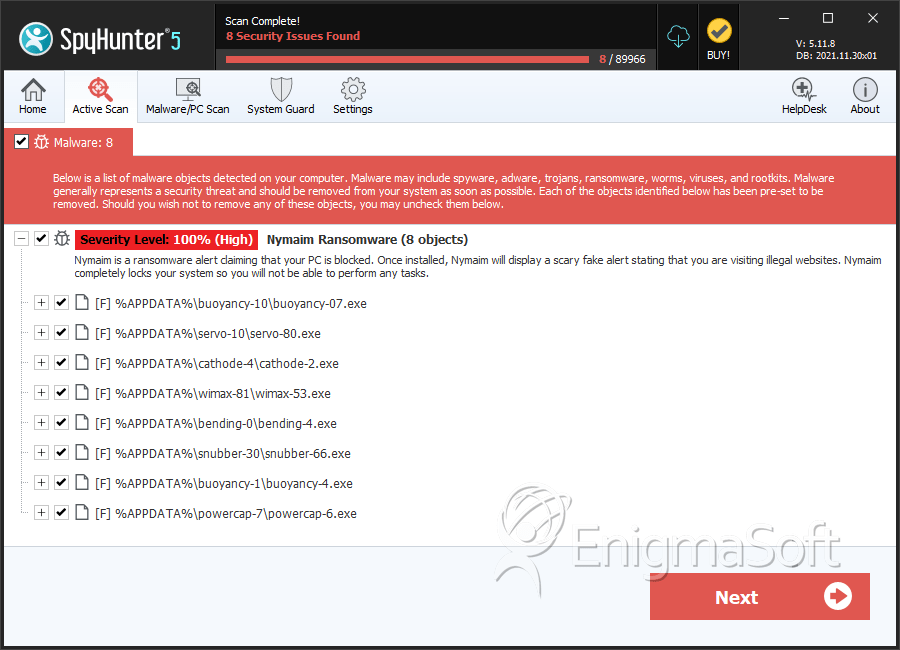
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | buoyancy-07.exe | 70aef4e3f87dd8500e7823d1959a0713 | 76 |
| 2. | servo-80.exe | 57ee304e6e5d6c8e457fa7261b678c86 | 75 |
| 3. | cathode-2.exe | 8cb39720072609f794b3761e1a042ff6 | 66 |
| 4. | wimax-53.exe | 2d53237ef901a75758dcc36d48194cbb | 46 |
| 5. | bending-4.exe | bbfa12669ce2c99136c8374f868ad1a2 | 46 |
| 6. | snubber-66.exe | 13fd1f234fee09cd5c283176de051d3c | 44 |
| 7. | buoyancy-4.exe | 8759644768bc2ff359600b97841b687f | 43 |
| 8. | powercap-6.exe | 53904459f78d8d876df32be4e0390a54 | 28 |
| 9. | alkene-87.exe | 3dec30d4903313cf7938fb8f3e6c2e80 | 28 |
| 10. | gamma-3.exe | 62f97b6201785aff480f2681f196cdce | 11 |
| 11. | ascii-8.exe | 0b8b12b971ccc8a02cc5927a4b0e6d89 | 10 |
| 12. | transfer-09.exe | b8bce5789a340f3230a58972db4642f4 | 9 |
| 13. | robotics-21.exe | f37377e354a887066c34d699252e3f5f | 7 |
| 14. | brownout-7.exe | 511b8484bd3511e8bb9568024302bbf8 | 7 |
| 15. | nyquist-37.exe | ed7b61c2ef72e6aa51249b9e4596c5d7 | 7 |
| 16. | anion-7.exe | f1537003f5eadbdf8378e75640803c08 | 5 |
| 17. | adhesion-20.exe | ceca56fcbe490494b143e68c8230a3e2 | 2 |
| 18. | analogue-64.exe | 23d4c23532d3c120b92fa95a8a381021 | 2 |
| 19. | switcher-20.exe | 7c4852864eab562d42113f7decb78a7e | 2 |
| 20. | receiver-60.exe | 7533db37818a89576b64073a9b3beab2 | 2 |
| 21. | analogue-09.exe | 3a75a3f9325e5a0cf9eb17d952713cb4 | 1 |
| 22. | adhesion-14.exe | 8ee739c01a70923f83975a77dcd34948 | 1 |
| 23. | buoyancy-22.exe | 8213a8d144daf22a60e11fabe0000729 | 1 |
| 24. | molality-08.exe | e5c2c69349456d0f79f7c85e393fa6ae | 1 |
| 25. | buoyancy-21.exe | 7fb91e998ac89c3924eb6f51c5250285 | 1 |
| 26. | debounce-28.exe | fbba9e2bad1eced5dbba660dea9711be | 1 |
| 27. | shutdown-14.exe | 9ee1a90155fa1dbeea72f02760d95e9c | 1 |
| 28. | molecule-94.exe | 09753373ef1391898c60a8b29c728d44 | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.