Noblis Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 20 |
| First Seen: | December 17, 2017 |
| Last Seen: | February 18, 2022 |
| OS(es) Affected: | Windows |
The Noblis Ransomware is an encryption ransomware Trojan that was first observed by PC security researchers on December 12, 2017. It seems that the Noblis Ransomware in its current state is incomplete, and it is likely that an updated version of the Noblis Ransomware will be released. Currently, the Noblis Ransomware is loaded on the infected computer's RAM and carries out an encryption ransomware attack, which takes the victim's files hostage. The Noblis Ransomware uses a ransom note written in Spanish, although PC security researchers also have reported a Portuguese variant. This indicates that the Noblis Ransomware is designed to target computer users in certain geographic locations specifically (although this does not preclude the Noblis Ransomware being able to infect computer systems all over the world).
Table of Contents
What is the Purpose of the Noblis Ransomware
The Noblis Ransomware seems to be packed using UPX and the Noblis Ransomware is coded using Python. The Noblis Ransomware will create a text file named 'encrypted_files.txt' on the infected computer during its attack. The Noblis Ransomware appears to have been programmed by someone going by the name '@4v4t4r' and will encrypt the files with the following extensions:
JPG, MP4, DOC, DOCX, PDF, ZIP, MSI, MP3, TAR.GZ, TXT, TSX.
The files affected by the attack will be marked with the file extension '.noblis' added tot he end of the file's name. The Noblis Ransomware displays its ransom note in a CFG file named 'runtime.cfg' that displays a program window with the name 'CRYPTER.'
The Noblis Ransomware’s Ransom Note
The Noblis Ransomware's ransom note delivers a typical ransom note alerting the victim of the attack. The Noblis Ransomware window contains a 24-hour countdown timer and a payment address for the victim pay the ransom using Bitcoins. The Spanish text of the Noblis Ransomware ransom note reads:
'CRYPTER
YOUR FILES HAVE BEEN ENCRYPTED!
Los archivos más importantes de este equipo han sido cifrados con un sistema de grado militar (AES-256)
Sus documentos, videos, imágenes y otros formatos (y por supuesto la FLAG) están fuera de su alcance... Y no podrá descifrarlos sin la llave apropiada... Esta se encuentra almacenada en un servidor remoto.
Las únicas formas de obtenerla, será pagando a la billetera antes que el tiempo se acabe.. También puede vulnerar el servidor remoto¿?...
O encontrar alguna falla en este sistema de cifrado¿?...
--- Recuerde que este reto es únicamente con fines académicos e investigativos... No pierda tiempo... Pues una vez termine la cuenta regresiva, los archivos serán eliminados de forma permanente ---
@4v4t4r
WALLET ADDRESS: nobliswallet99838399283928392323
BITCOIN FEE: 1.0'
Below is the Noblis Ransomware ransom note translated to English:
'The most important files of this machine have been encrypted with a military grade system (AES-256)
Your documents, videos, images and other formats (and of course the FLAG) are beyond your reach ... And you will not be able to decipher them without the proper key ... This is stored on a remote server.
The only way to obtain it, will be to pay before the time runs out.
Can you crack the remote server? ...
Or find some flaw in this encryption system? ...
--- Remember that this challenge is only for academic and investigative purposes ... Do not waste time ... Well once the countdown is finished, the files will be permanently deleted ---
@4v4t4r
WALLET ADDRESS: nobliswallet99838399283928392323
BITCOIN FEE: 1.0'
The Noblis Ransomware's ransom amount is equivalent at the current exchange rate to nearly 17,000 USD. However, computer users are advised not to pay the Noblis Ransomware ransom.
Protecting Your Data from Threats Like the Noblis Ransomware
The best protection against threats like the Noblis Ransomware is to have file backups on unreachable, secure places. Having security copies of your files means that you can recover from a Noblis Ransomware infection by removing the affected files and replacing them with the backup copies. Oncxe again, do not contact the cybercrooks or pay the large ransom fee that is associated with the Noblis Ransomware attack.
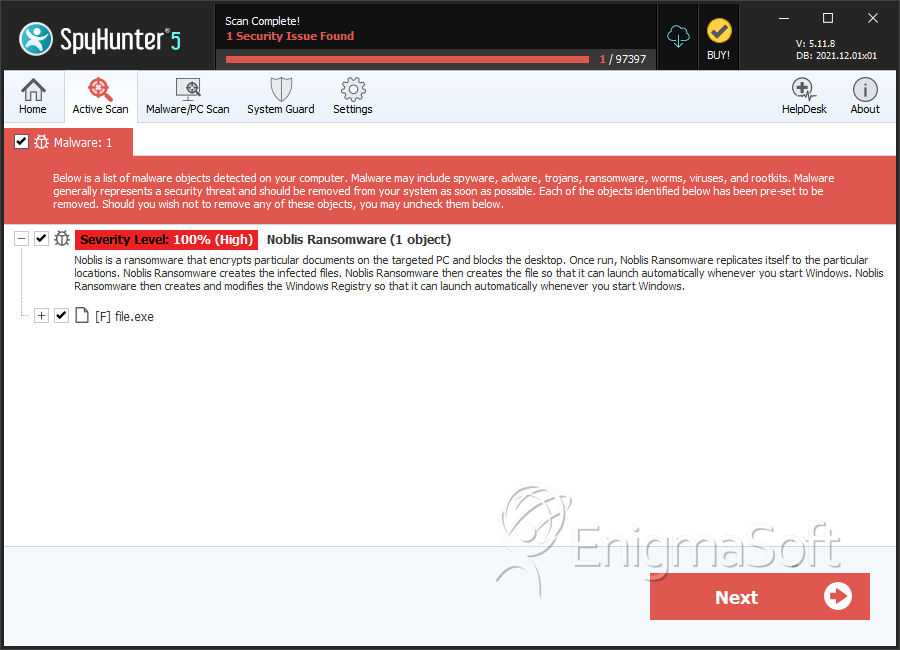
SpyHunter Detects & Remove Noblis Ransomware


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.