Mr.Dec Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 80 |
| First Seen: | May 23, 2018 |
| Last Seen: | August 13, 2020 |
| OS(es) Affected: | Windows |
The Mr.Dec Ransomware is an encryption ransomware Trojan first observed in the middle of May 2018. The Mr.Dec Ransomware Trojan is distributed through the use of spam email messages mostly. These messages often will contain an email attachment that delivers the Mr.Dec Ransomware to the victim's computers through the use of embedded macro scripts. The Mr.Dec Ransomware is delivered using an XLS file, a spreadsheet document with damaged enabled scripts, although most of these threats are delivered using Microsoft Word files. The email tactic used to deliver this file claims that the file contains data needed for a shipment. When the victim opens the file, the macros download and install the Mr.Dec Ransomware onto the victim's computer.
Table of Contents
How the Mr.Dec Ransomware will Affect Your Files
The Mr.Dec Ransomware will scan the victim's computer in search for certain file types and encrypt them using a strong encryption method. The Mr.Dec Ransomware will target the user-generated files while avoiding the Windows operating system files and applications. This is done to ensure that the Mr.Dec Ransomware can take victim's files hostage while ensuring that the operating system is still operational so that the victim can pay a ransom amount in exchange for the decryption key. The Mr.Dec Ransomware takes the victim's files hostage with this method. The encryption used, AES 256, is quite strong and once the files are encrypted, they cannot be recovered. The Mr.Dec Ransomware marks files encrypted by the attack by adding the file extension '.[ID]<16 random characters>[ID]' to the names of the files. Some of the file types that are commonly targeted in attacks like the Mr.Dec Ransomware's include:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
The Mr.Dec Ransomware’s Ransom Note
The Mr.Dec Ransomware delivers a ransom note in the form of an HTA file named 'Decoding help.hta' that is dropped onto the victim's computer. This ransom note delivers the following message in a full-screen window:
'You are unlucky! The terrible virus has captured your files! For decoding
please contact by email mr.dee@protonmail.com or mr.dee@tutanota.com
Your
|ID| <16 random characters>|ID|
1. In the subject line, write your ID.
2. Attach 1-2 infected files that do not contain important information (less than 2 mb)
3. Attach the file with the location c:\Windows\DECODE KEY.KEY
are required to generate the decoder and restore the test file.
Hurry up! Time is limited!
Attention!!!
At the end of this time, the private key for generating the decoder will be destroyed. Files will not be restored!'
However, following the instructions in the ransom note or contacting the criminals via the email addresses provided will end up causing more bad than good.
Protecting Your Data from the Mr.Dec Ransomware
The best protection against threats like the Mr.Dec Ransomware is to have file backups stored on an independent memory drive or a cloud storage provider. Having file backups ensures that you can recover your files after an attack without needing to contact the criminals. A dependable security program that is fully up-to-date also can be used to ensure that the Mr.Dec Ransomware is not installed in the first place and intercept these threats.
SpyHunter Detects & Remove Mr.Dec Ransomware
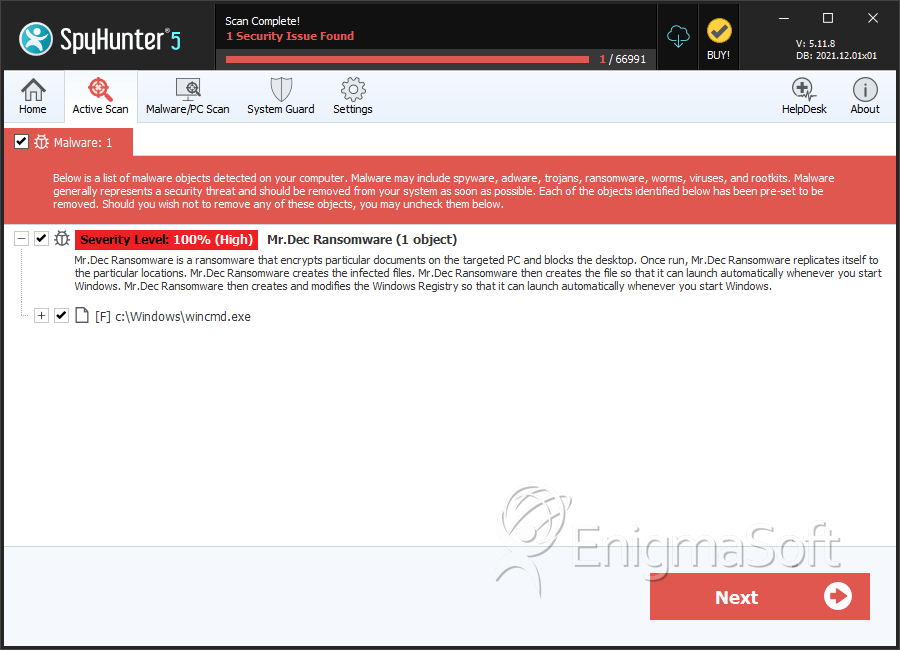
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | wincmd.exe | f86291e994c2e9cb0bb9650d362ee625 | 1 |

