Mordor Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 1 |
| First Seen: | May 2, 2017 |
| Last Seen: | April 18, 2018 |
| OS(es) Affected: | Windows |
The Mordor Ransomware is a ransomware Trojan that is used to blackmail computer users, keeping their files locked and then demanding the payment of a ransom. The Mordor Ransomware receives its name because it uses certain imagery from The Lord of the Rings in its attack. The Mordor Ransomware's payment portal includes an image of the iconic Eye of Sauron from this book series and movie franchise. Apart from its branding, though, there is little to differentiate the Mordor Ransomware from the numerous other ransomware Trojans that are being used to carry out attacks against computer users currently.
Table of Contents
The Mordor Ransomware – A Fictional Name for a Real Threat
The Mordor Ransomware was first uncovered in the first week of May 2017. The Mordor Ransomware will mark the files it encrypts with the file extension '.mordor.' The Mordor Ransomware attacks have been spotted around the world, and it seems that this ransomware Trojan, like many others, is being delivered through the use of corrupted email attachments contained in spam email messages. These corrupted emails also may include unsafe links, which can be used to install the Mordor Ransomware on the victim's computer.
The Mordor Ransomware carries out its attack with a combination of the AES and RSA encryptions. This is a very common approach seen in the vast majority of emerging ransomware Trojans. Using this combination of encryption methods, the Mordor Ransomware can make the files unrecoverable for those without the decryption key (which the extortionists controlling the Mordor Ransomware hold in their possession). The Mordor Ransomware will infect computers with the Windows operating system and attempt to encrypt the files located on all local drives, as well as on removable memory devices and directories shared on a network. The Mordor Ransomware executable file will be named 'NOTHERSPACE_USE.exe' and will be located in the Temp directory on the infected computer. The Mordor Ransomware has received various other names from PC security providers, including 'SuperCow' and 'Milene.' After carrying out its attack, the Mordor Ransomware will deliver a ransom note. This note, in the form of an HTML file on the infected computer's desktop, is named 'Read_Me.html' and will contain the following text:
'Все файлы зашифрованы!
Есля тебе важны твои документы - перейди по ссылке. Там будет вся необходимая информация чтобы ты вернул свои файлы. Иначе ты на всегда потеряет их;-)
All data - encrypted!
If you need your documents - go to one of the links. There will be all the necessary Information to return your files. A Otherwise, you will always lose them ?
ID: [RANDOM NUMBER]'
What You can do to Counteract the Mordor Ransomware
The Mordor Ransomware will target a wide variety of files, mainly the files that are generated by the user (such as text documents, spreadsheets, media files, video, audio, etc.). The Mordor Ransomware will include its payment instructions in numerous languages, including English, French, Portuguese, Hindi, Turkish, Italian, German, RussiaT and Japanese. This points to the intentions of the extortionists responsible for the Mordor Ransomware infection, which seem to have the aim of taking this attack globally. The Mordor Ransomware demands the payment of a ransom of 1 BitCoin (approximately $1500 USD at the current exchange rate). Computer users are advised against paying the Mordor Ransomware ransom. In many cases, the extortionists will ignore the payment or reinfect the victim's computer after the ransom has been paid, demanding repeated payments from the victim. Furthermore, paying these ransoms support these extortionists' activities, allowing them to develop other ransomware Trojans like the Mordor Ransomware and claim new victims. Instead of paying the ransom, take preventive measures. These may include storing your data on the cloud or an external memory device. If computer users can restore the encrypted files from a backup copy stored elsewhere, then the people responsible for the Mordor Ransomware lose any leverage over the victim.
SpyHunter Detects & Remove Mordor Ransomware
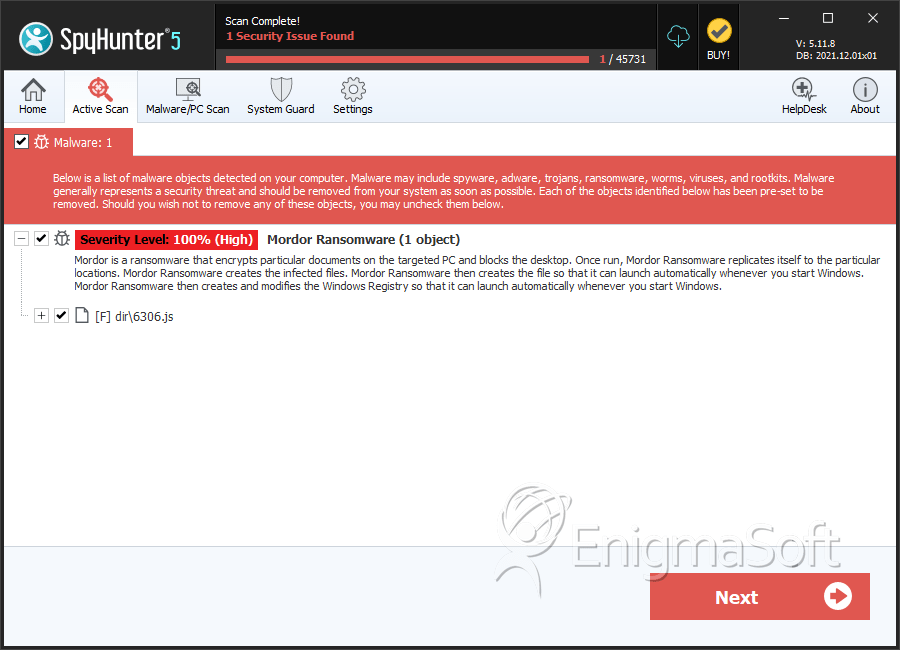
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 6306.js | 90b6b02c2537dff0a4f816176aeb4814 | 0 |

