Moloch Ransomware
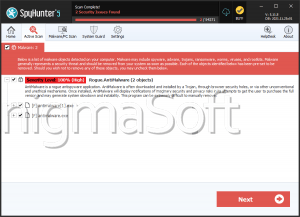
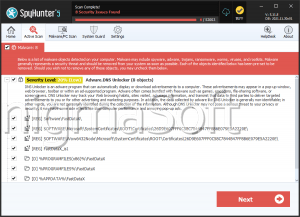
The Moloch Ransomware is a file-locking Trojan that can block documents and similar media of value to the user. According to the Makop Ransomware family's standards, it conducts its attacks, including a text ransom note and a multi-component extension for locked data. Users should keep their work safe on external backups to prevent its extortion attempt from succeeding and protect their systems with professional security solutions capable of deleting the Moloch Ransomware on sight.
The Globe-Spanning Adventures of a Real Demon of a Program
First caught by security analysts in Turkey-specific variants, Makop Ransomware is a file-locker Trojan family that's no stranger to changing countries or languages. While most of its members speak in the English language, like the newest the Moloch Ransomware, that doesn't always imply attacks against nations using English as their official language. For the Moloch Ransomware, malware experts are seeing versions targeting South Korean workplaces with appropriately-themed disguises.
The Moloch Ransomware, which takes the name of a Canaanite deity associated with child sacrifices, is a mostly-conventional update to this family, which boasts a steady supply of members, such as the Fair Ransomware, the Origami Ransomware, the Shootlock Ransomware and the Zbw Ransomware. First, the Windows threat blocks the user's media files with encryption so that they can't open and, then, delivers a text note that sells unlocking aid in exchange for a ransom.
However, the Moloch Ransomware executable's name isn't English but Korean. The phrase translates to 'resume,' which suggests the phishing lure at work in its campaign immediately. The use of fake resumes in e-mails to workplace entities in various industries is one of the more common themes in file-locker Trojans' installation exploits. Naturally, users should pay attention to the extension on the file and its format (which may not be the same thing) and be careful, particularly around unknown 'EXE' or executable program files.
Putting Old World Demons Back to Rest
While its name is ominous extraordinarily, the Moloch Ransomware is no more – or less – threatening to users' media files than any other file-locker Trojan of its family. Since there isn't a freeware solution to its attacks, malware experts continue emphasizing that backups with adequate protection are the only recovery method that doesn't cost money. Rarely, users may recover from Local Restore Points or advanced Shadow Copy utilities, but those options never are dependable against these threats.
Due to the high chances of the Moloch Ransomware's arriving by e-mail, workers should be alert to possibly-fake document attachments, which may include regional, industry, company, or even employee-specific details. However, the Moloch Ransomware also can block files on Windows systems outside of its target region of South Korea. Scanning downloads, enabling visible extensions, and disabling macros are the most relevant protection available to all users.
Paying the ransom is generally not ideal since criminals can upload fake 'unlocked' files threatening to the 'clients' or not provide the recovery service. Good quality anti-malware programs will delete the Moloch Ransomware and identify it without issues, assuming that users have their protection.
The Moloch Ransomware is a far cry from the sacrificial exploits of its namesake but burns up files just as well as any other Makop Ransomware release. A file's name isn't always what it is – a simple but poignant lesson in this Trojan's campaign.