Mole02 Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 11 |
| First Seen: | June 15, 2017 |
| Last Seen: | May 12, 2019 |
| OS(es) Affected: | Windows |
The Mole02 Ransomware is a new variant of the MOLE Ransomware, a known ransomware Trojan that has been around for a while. The Mole02 Ransomware is easy to be identified because it will mark the infected files with the file extension '.mole02.' The Mole02 Ransomware carries out a typical ransomware attack, encrypting victims' files and then demanding a ransom to be provided with the decryption key needed to recover the affected files. It is important to take precautions against the Mole02 Ransomware and its variants since this ransomware family represents a real danger to computers and the computer users' data.
Table of Contents
The Mole02 Ransomware Impersonates a Very Convincing Microsoft Online
The Mole02 Ransomware attack is typical of these infections, taking over the victim's computer and the victim's files captive, and then demanding the payment of a ransom. The Mole02 Ransomware carries out an effective attack, like its predecessors, using the RSA-1024 encryption to make the victim's files inaccessible. The Mole02 Ransomware includes complex characteristics that allow the Mole02 Ransomware to avoid detection and tricks computer users into downloading and installing it onto their computers. For example, one distribution technique used by the Mole02 Ransomware variant involves a fake Office plugin, a website designed to imitate the Microsoft Online perfectly, and highly-convincing spam email messages with embedded links.
How the Mole02 Ransomware may Infect a Computer
The Mole02 Ransomware belongs to a large family of ransomware known as CryptoMix, which has numerous variants. These threats carry out typical ransomware attacks, with little to distinguish them from many other ransomware Trojans that are active currently. The Mole02 Ransomware will deliver a ransom note demanding the payment of a large amount of money, after encrypting its victims' data, typically targeting user-generated file types. The ransom note that has been associated with the Mole02 Ransomware may be contained in a text file named '_HELP_INSTRUCTION.TXT,' which includes the following message, displayed on the victim's computer:
'All your important files were encrypted on this computer.
You can verify this by click on see files an try open them.
Encryption was produced using unique public key RSA-1024 generated for this computer.
To decrypted files, you need to obtain private key.
The single copy of the private key, with will allow you to decrypt the files, is locate on a secret server on the internet.
The server will destroy the key within 78 hours after encryption completed.
To retrieve the private key, you need to Contact us by email , send us an email your DECRYPT-ID-Redacted number
and wait for further instructions.
For you to be sure, that we can decrypt your files – you can send us a single encrypted file and we will send you back it in a decrypted form.
Please do not waste your time! You have 72 hours only! After that The Main Server will double your price!
E-MAILS ADRESS:
oceanm@engineer.com
oceanm@india.com'
Dealing with the Mole02 Ransomware and Its Variants
Fortunately, having good backup systems has counteracted the attacks that have occurred involving the Mole02 Ransomware. When talking about ransomware Trojans, the best protection for your data is to have backups of your files. If you have the tradition of backing up your files, then the people responsible for the attack will not have any power or leverage that would allow them to demand a ransom payment from you. Not having a backup copy can cost you thousands of dollars in ransom payments, and establishing a backup system is often an insignificant cost, due to the wide availability of free cloud storage and low-cost memory devices. Apart from having file backups, you should have a security program that you can trust, which can intercept the Mole02 Ransomware attack and prevent it from infecting your computer. Since the Mole02 Ransomware may be delivered via corrupted email attachments, learning to handle spam emails safely is also essential when dealing with threats like the Mole02 Ransomware and other widely spread ransomware Trojans.
SpyHunter Detects & Remove Mole02 Ransomware
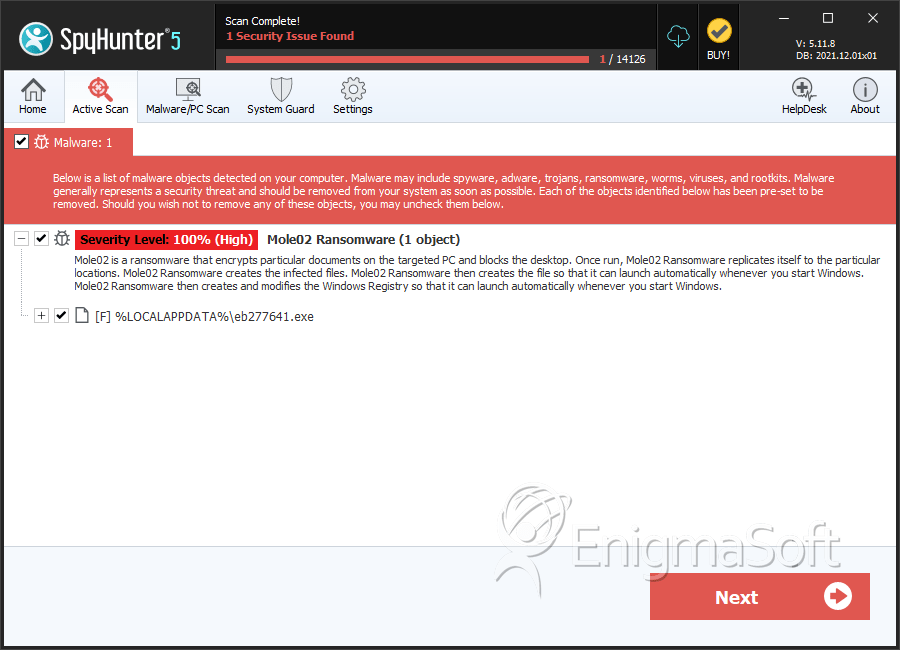
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | eb277641.exe | 0ae91dbea7eff4b045b42920035a7a93 | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.