Mikoyan Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 5 |
| First Seen: | May 3, 2017 |
| Last Seen: | August 17, 2022 |
| OS(es) Affected: | Windows |
The Mikoyan Ransomware is a ransomware Trojan that was first observed on May 1, 2017. The Mikoyan Ransomware will use an executable file named 'MIKOYAN.exe.' The Mikoyan Ransomware uses an English-language ransom note. However, this does not limit it geographically, and the Mikoyan Ransomware attacks can carry out anywhere in the world. The Mikoyan Ransomware carries out a typical ransomware attack and may be delivered to victims through spam email messages.
Table of Contents
How the Attack of the Mikoyan Ransomware and Other Ransomware Trojans Work
The Mikoyan Ransomware is a typical ransomware Trojan. A ransomware like the Mikoyan Ransomware receives its name because they are designed to force computer users to pay large ransoms. To do this, the Mikoyan Ransomware will encrypt the victim's files using a strong encryption algorithm, taking the files hostage until the victim agrees to pay the ransom. The Mikoyan Ransomware and most other ransomware Trojans may be delivered using corrupted email attachments. Typically, the extortionists will send out spam email messages that will include these attachments or corrupted links leading to attack websites. These messages may utilize social engineering techniques to trick computer users into opening the attachment or clicking on the link. When the victim opens the attachment, which may take the form of a text file, it will execute a corrupted macro, which will allow the Mikoyan Ransomware to be installed. As soon as the Mikoyan Ransomware is installed, it will begin to carry out its attack.
What are the Consequences of a Mikoyan Ransomware Attack
As soon as the Mikoyan Ransomware is installed, it will scan the victim's files, searching for certain files with specific file extensions included in the Mikoyan Ransomware's configuration files. The Mikoyan Ransomware is designed to target the files generated by the user, including media files, images, video, audio, text files, spreadsheets, and files created by software such as Libre Office, Microsoft Office, Adobe Photoshop, etc. The Mikoyan Ransomware uses a combination of the RSA-2048 and AES-256 encryptions to make the victim's files inaccessible. As part of its attack, the Mikoyan Ransomware will try to destroy other forms of alternate recovery, such as the System Restore Points or the Shadow Volume Copies that are created by Windows. After encrypting the victim's files and communicating with its Command and Control servers, the Mikoyan Ransomware will deliver its ransom note. This ransom notification is displayed in a window titled 'MIKOYAN ENCRYPTOR.' The following is the full text of the Mikoyan Ransomware ransom note:
'Warning!
Your downloaded files had been encrypted with a AES-256 enciyption key.
If you want your files back send 1 Btcoins in the adress below.
BITCOIN ADDRESS: 3Cnd77qB88NOiCoChUu4F3exV8CKGH4Ce
Need help? contact me.
EMAIL ADDRESS : mikoyan.ironsight@outlook.com
Good luck before it gets encrypted with RSA-4096
ENTER DECRYPTION KEY
[TEXT BOX] '
How to Deal with a Mikoyan Ransomware Infection
The Mikoyan Ransomware demands the payment of 1 BitCoin (approximately $1500 USD at the average current exchange rate). This pricey ransom, however, does not guarantee that the extortionists will respond or help the victim recover their files. Furthermore, paying the Mikoyan Ransomware ransom finances the creation and development of the Mikoyan Ransomware and similar threats, increasing the chances of future infections. Rather than paying, you should take preventive measures to ensure that your computer is well protected from the Mikoyan Ransomware.
There are several various, protective actions you can take to decrease the probability of infection with the Mikoyan Ransomware and similar threats. The experts strongly recommend the use of a reliable security program that is fully up-to-date. Learn to handle emails safely. Apart from this, PC security researchers advise computer users to have file backups. In fact, having backup copies of all files is the best way to protect yourself from threats like the Mikoyan Ransomware. If computer users have the ability to recover their files from a backup copy located in an external memory mechanism, then the people responsible for the Mikoyan Ransomware attack lose their power over the victim, which allows them to demand the ransom payment.
SpyHunter Detects & Remove Mikoyan Ransomware
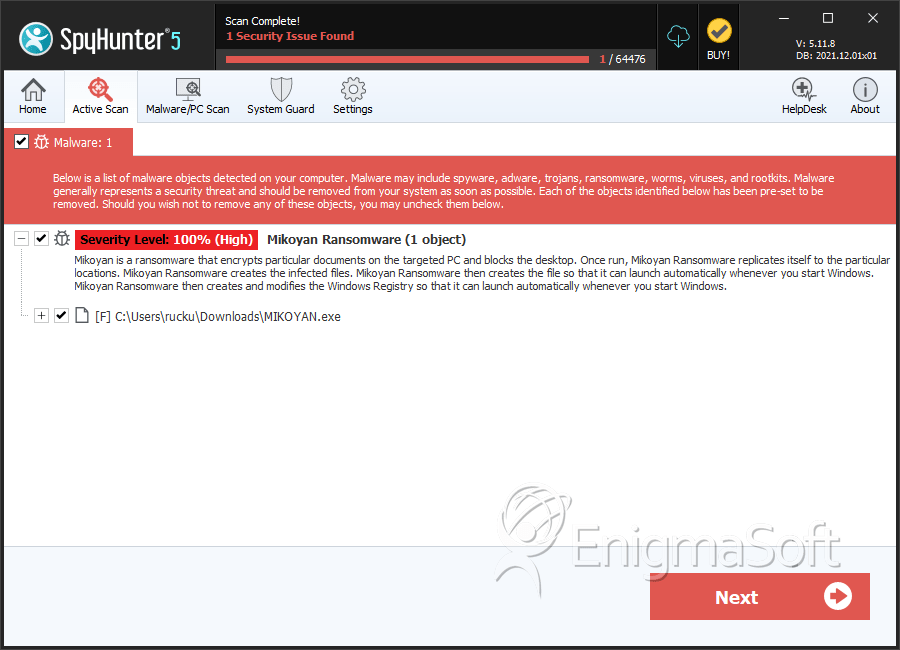
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | MIKOYAN.exe | 4da994544d32b9418bbf227158e1f06f | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.