Mal/FakeAV-PY
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 20 % (Normal) |
| Infected Computers: | 1 |
| First Seen: | February 10, 2012 |
| OS(es) Affected: | Windows |
Some security applications stop scareware attacks proactively, detecting various sorts of payloads associated with several categories of scareware, blocking them, and displaying a Mal/FakeAV-PY detection. According to ESG security researchers, if your computer system is detecting a Mal/FakeAV-PY attack, this usually refers to a suspicious behavior which may mean that your computer system has become the target of a scareware attack. There are several types of scareware that are detected as Mal/FakeAV-PY, most of which are usually Trojans that install a fake anti-virus or defragmenter on the victim's computer system. The Mal/FakeAV-PY detection indicates that the victim's computer is the target of a popular online scam that is often the result of having visited an unsafe website, downloaded an infected file or opened an infected file attachment or link in an unsolicited email message. If your security software indicates that you are the victim of a Mal/FakeAV-PY attack, you are probably protected, but should scan your hard drive just to be on the safe side. Most modern malware attacks include various components. While your real-time malware scanner may be able to intercept some attacks, modern malware will attempt to exploit as many known vulnerabilities as possible, injecting batches of malicious files onto the victim's computer system. In fact, it is not uncommon for PC security analysts to remove hundreds of Trojans, viruses and other kinds of malware infections from a single infected drive!
Table of Contents
Understanding Online Scams Detected as Mal/FakeAV-PY
Scareware scams are usually designed to scare inexperienced computer users in order to scam them out of their money. Some examples of scareware include the following:
- Mal/FakeAV-PY may refer to fake anti-virus programs that detect numerous fake infections and then attempt to convince the victim to purchase a useless 'full version' in order to remove these non-existent infections. These kinds of scareware threats are known as rogue anti-virus or rogue anti-malware applications.
- Mal/FakeAV-PY may also refer to the presence of a fake defragmenter which, in a way similar to rogue anti-virus programs, will pretend to be a legitimate computer optimization tool. However, these kinds of programs are actually designed to spam their victims with error messages claiming that their computer has several severe problems that can only be removed by purchasing a 'full version' of the rogue defragmenter.
- Other kinds of scareware associated with Mal/FakeAV-PY are also known as ransomware, programs designed to lock the victim's computer (often claiming to be doing so on behalf of a law enforcement agency), demanding the payment of a ransom in order to return control of the infected computer.
Aliases
5 security vendors flagged this file as malicious.
| Anti-Virus Software | Detection |
|---|---|
| Panda | Suspicious file |
| Sophos | Mal/FakeAV-PY |
| AntiVir | TR/Crypt.ZPACK.Gen |
| K7AntiVirus | Trojan |
| McAfee | Artemis!9E8510765E97 |
SpyHunter Detects & Remove Mal/FakeAV-PY
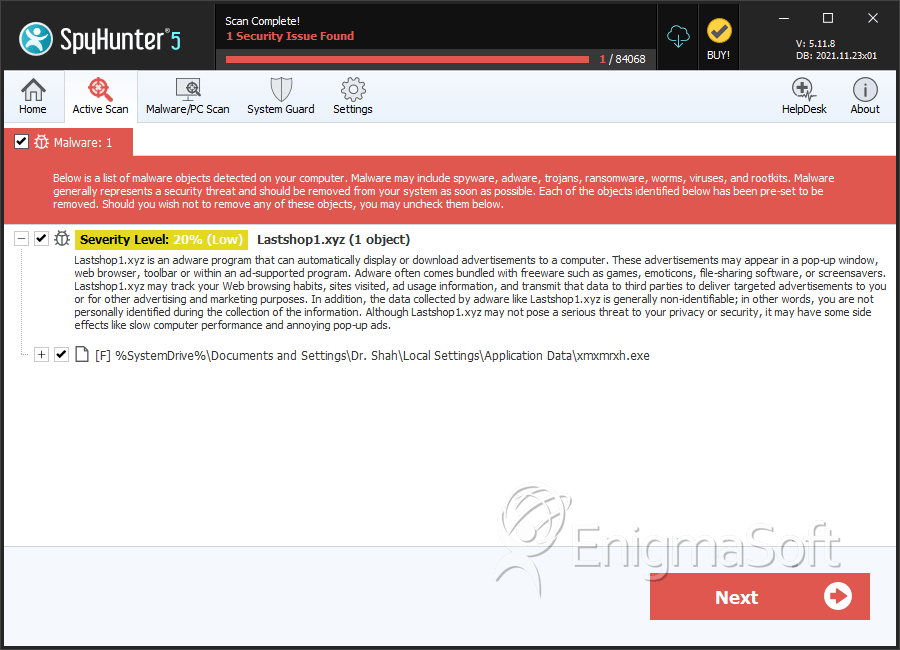
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | xmxmrxh.exe | 9e8510765e974a0042471f4ab1961ec7 | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.