Mal/Badsrc-C
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
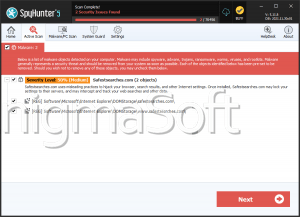
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 7,333 |
| Threat Level: | 80 % (High) |
| Infected Computers: | 2,131 |
| First Seen: | November 7, 2011 |
| Last Seen: | October 31, 2025 |
| OS(es) Affected: | Windows |
Mal/Badsrc-C is a malware threat that can inject itself within the popular blog-building software WordPress. WordPress users infected with Mal/Badsrc-C will find that an index.html file will become infected. Mal/Badsrc-C installs itself in a way so that Mal/Badsrc-C only affects users using the IE browser. Mal/Badsrc-C has proliferated since its first detections in the late summer of 2011. According to ESG PC security researchers, Mal/Badsrc-C will attack computers using the Internet Explorer Internet browser, but will not affect computers using other popular web browsers, including Mozilla Firefox and Google Chrome. It seems that Mal/Badsrc-C uses a vulnerability specific to Internet Explorer, which involves a PHP script on WordPress Internet websites. This means that computer users using this web browser will become infected with Mal/Badsrc-C when visiting an infected website. ESG malware analysts suspect that these WordPress websites may have become infected in the first place through an FTP (File Transfer Protocol) attack.
Table of Contents
Protecting Your WordPress Website from Mal/Badsrc-C
ESG malware analysts recommend using a strong password to protect WordPress accounts and websites. It is important to make sure that a password is long enough and that it contains a mixture of symbols, letters and numbers. Using a simple dictionary word or one of the most popular passwords (such as "123456" or "12345678") places you at risk for a malware attack, including a Mal/Badsrc-C virus infection. It is also important to use different passwords for your different online accounts. ESG PC security researchers also recommend inspecting your website's code regularly to ascertain that there have been no intrusions. To protect yourself from Mal/Badsrc-C, ESG PC security researchers also recommend keeping your security program fully updated. While WordPress malware attacks are not new, the way Mal/Badsrc-C operates is fairly uncommon. Typically, malware attacking WordPress websites would be spread using WordPress modules or widgets created specifically for this purpose. According to ESG malware analysts, it does not seem that Mal/Badsrc-C is associated with a particular WordPress module, but rather attacks through other means. To make sure that your website does not become a source of Mal/Badsrc-C virus infections and that your readers are protected (particularly those using Internet Explorer), ESG PC security researchers recommend taking the time to make sure that your website is fully secured, that your passwords are strong, that your security software is updated and that no undetected intrusions into your website have occurred in the past.
Analysis Report
General information
| Family Name: | Trojan.Emotet.RNA |
|---|---|
| Signature status: | No Signature |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
9f78dd6ee715389db05cfd196641457d
SHA1:
fc1caf8e8ab5347b10be77e2c032b92a0b47150e
SHA256:
58761D9020FB020CE268E29484D4445005E196555E3692B7C833C59983C00212
File Size:
520.19 KB, 520192 bytes
|
|
MD5:
6b72617a0904bed0198f184d4bc2bd58
SHA1:
70b2824796d337f40a2e553559bc081232a8e747
SHA256:
73709B4192FAEEB375EA72F5743EFCFF4A15737C8519E54B4DABD13EC02103E2
File Size:
671.74 KB, 671744 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have exports table
- File doesn't have relocations information
- File doesn't have security information
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
- File is not packed
Show More
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
File Icons
File Icons
This section displays icon resources found within family samples. Malware often replicates icons commonly associated with legitimate software to mislead users into believing the malware is safe.Windows PE Version Information
Windows PE Version Information
This section displays values and attributes that have been set in the Windows file version information data structure for samples within this family. To mislead users, malware actors often add fake version information mimicking legitimate software.| Name | Value |
|---|---|
| Comments | This is a program to manage the programs that boot on windows startup. |
| Company Name | Elo Touchsystems |
| File Description |
|
| File Version |
|
| Internal Name |
|
| Legal Copyright |
|
| License | GNU General Public License |
| Original Filename |
|
| Product Name |
|
| Product Version |
|
| Website | http://startupmanager.org/ http://st-m.sf.net/ http://sf.net/projects/st-m/ |
File Traits
- HighEntropy
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 1,885 |
|---|---|
| Potentially Malicious Blocks: | 10 |
| Whitelisted Blocks: | 1,220 |
| Unknown Blocks: | 655 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block