Magniber Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Popularity Rank: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Popularity Rank: | 17,195 |
| Threat Level: | 100 % (High) |
| Infected Computers: | 726 |
| First Seen: | October 25, 2017 |
| Last Seen: | October 7, 2025 |
| OS(es) Affected: | Windows |
The Magniber Ransomware is the new name of the Cerber Ransomware, and the first samples of the threat were discovered on October 14th, 2017. However, the Magniber Ransomware is not just a new name for the old and familiar Cerber Ransomware. The change in the name is just part of many new changes in the Cerber platform. Cyber security experts warn that the Magniber Ransomware is presented to third parties as a RaaS — Ransomware as a Service — platform the same way as its predecessor. The new package includes all core functionalities that made Cerber one of the founding stones for the crypto-threat market of today. The core of the Magniber Ransomware Trojan is rebuilt, and there is a brand-new client-server confirmation along with improved file encryption algorithms. The creators of the Magniber Ransomware continue to use a broad spectrum of instruments to distribute the Trojan to potential victims such as:
- Macro-enabled Microsoft Word documents;
- Fake package confirmation letters from Amazon;
- Compromised RDP (Remote Desktop Protocol) connections;
- Boobytrapped pirated software.
The Magniber Ransomware is reported to make its first victims on the Korean peninsula and South-East Asia. The name of the Magniber Ransomware Trojan is derived from the fact that its first official release was facilitated using the Magnitude Exploit Kit. The attacks using the Magniber Ransomware are highly targeted, and the Trojan might be used in spear phishing attacks on large and medium-sized businesses. The initial Magniber Ransomware campaign is known to extort 0.2 Bitcoin that is worth 1129 USD/960 EUR from compromised users. The Magniber Ransomware is designed to run on the latest versions of Windows and affect images, presentations, text, eBooks, databases, videos, music, spreadsheets and contacts lists. The Magniber Ransomware adds a sequence of seven random characters to the file names of the encrypted objects. For example, 'Canada lynx.jpeg' may be renamed to 'Canada lynx.jpeg.nxpqwup' and users can find ‘READ_ME_FOR_DECRYPT.txt’ on the desktop, which offers the following message:
'ALL Y0UR D0CUMENTS, PHOTOS, DATABASES AND OTHER IMP0RTANT FILES HAVE BEEN ENCRYPTED!
===
Your files are NOT damaged! Your files are modified only. This modification is reversible.
The only 1 way to decrypt your files is to receive the private key and decryption program.
Any attempts to restore your files with the third-party software will be fatal for your files!
===
To receive the private key and decryption program follow the instructions below:
1. Download "Tor Browser" from https://www.torproject.org/ and install it.
2. In the "Tor Browser" open your personal page here:
xxxx://27dh6y1kyr49yjhx8i3.yhicav6vkj427eox.onion/N3ii3Ne9010*****
Note! This page is available via "Tor Browser" only.
===
Also you can use temporary addresses on your personal page without using "Tor Browser":
xxxx://27dh6y1kyr49yjhx8i3.sayhere.party/N3ii3Ne9010*****
xxxx://27dh6y1kyr49yjhx8i3.goflag.webcam/N3ii3Ne9010*****
xxxx://27dh6y1kyr49yjhx8i3.keysmap.trade/N3ii3Ne9010*****
xxxx://27dh6y1kyr49yjhx8i3.segon.racing/N3ii3Ne9010*****
Note! These are temporary addresses! They will be available for a limited amount of time!'
PC users that may have been compromised by the Magniber Ransomware should not expect that the native recovery function Windows will remain usable. Unfortunately, the Magniber Ransomware Trojan is observed to delete the Shadow Volume Copies created by the system for recovery purposes. You should be able to use recovery images made with third-party tools and access cloud-based storage with archived data if you have any. Compliance with the terms laid by the Magniber Ransomware operators does not translate to a favorable outcome necessarily. Cybersecurity experts recommend users install a capable backup manager and purge the Magniber Ransomware using a trusted anti-malware scanner. AV engines are known to recognize the objects utilized by the Magniber Ransomware and flag them as:
- Trojan.Ransom.Magniber.C
- Trojan/Win32.Sobnot.R210740
- Win32:Magniber-A [Ransom]
- TR/Crypt.XPACK.Gen
- W32/Filecoder_Cerber.Z!tr
- Ransom_Sobnot.R03BC0DJJ17
- Trojan-Ransom.Win32.Magni.a
Table of Contents
SpyHunter Detects & Remove Magniber Ransomware
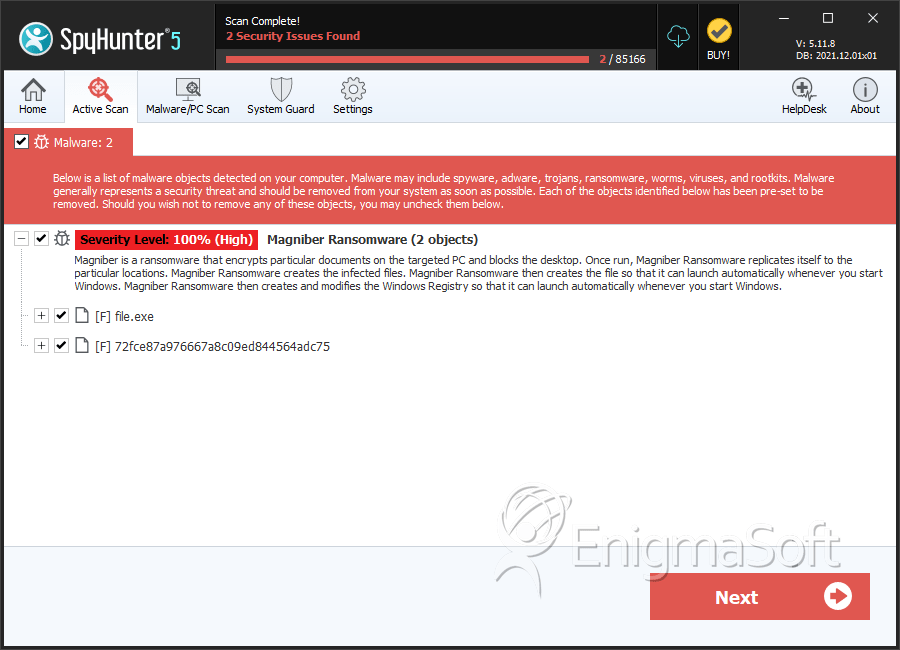
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 617230c31822e65e9c5805665deb81c4 | 0 |
| 2. | 72fce87a976667a8c09ed844564adc75 | 72fce87a976667a8c09ed844564adc75 | 0 |
Analysis Report
General information
| Family Name: | Magniber Ransomware |
|---|---|
| Packers: | UPX! |
| Signature status: | Hash Mismatch |
Known Samples
Known Samples
This section lists other file samples believed to be associated with this family.|
MD5:
be3705692fdd14db297db6c9de903e9a
SHA1:
2df1df53dfdbfa246a20b2b69856a7cac00b1b07
SHA256:
605E5CB57ABB72E0D1A679845118E7AFA93E87FAC82E87D9284F605771EF139B
File Size:
8.60 MB, 8597216 bytes
|
Windows Portable Executable Attributes
- File doesn't have "Rich" header
- File doesn't have debug information
- File doesn't have resources
- File doesn't have security information
- File has been packed
- File has exports table
- File is 32-bit executable
- File is either console or GUI application
- File is GUI application (IMAGE_SUBSYSTEM_WINDOWS_GUI)
- File is Native application (NOT .NET application)
Show More
- IMAGE_FILE_DLL is not set inside PE header (Executable)
- IMAGE_FILE_EXECUTABLE_IMAGE is set inside PE header (Executable Image)
Digital Signatures
Digital Signatures
This section lists digital signatures that are attached to samples within this family. When analyzing and verifying digital signatures, it is important to confirm that the signature’s root authority is a well-known and trustworthy entity and that the status of the signature is good. Malware is often signed with non-trustworthy “Self Signed” digital signatures (which can be easily created by a malware author with no verification). Malware may also be signed by legitimate signatures that have an invalid status, and by signatures from questionable root authorities with fake or misleading “Signer” names.| Signer | Root | Status |
|---|---|---|
| ASUSTeK Computer Inc. | DigiCert SHA2 Assured ID Code Signing CA | Hash Mismatch |
File Traits
- 2+ executable sections
- dll
- upx
- x86
Block Information
Block Information
During analysis, EnigmaSoft breaks file samples into logical blocks for classification and comparison with other samples. Blocks can be used to generate malware detection rules and to group file samples into families based on shared source code, functionality and other distinguishing attributes and characteristics. This section lists a summary of this block data, as well as its classification by EnigmaSoft. A visual representation of the block data is also displayed, where available.| Total Blocks: | 56 |
|---|---|
| Potentially Malicious Blocks: | 0 |
| Whitelisted Blocks: | 18 |
| Unknown Blocks: | 38 |
Visual Map
? - Unknown Block
x - Potentially Malicious Block
Windows API Usage
Windows API Usage
This section lists Windows API calls that are used by the samples in this family. Windows API usage analysis is a valuable tool that can help identify malicious activity, such as keylogging, security privilege escalation, data encryption, data exfiltration, interference with antivirus software, and network request manipulation.| Category | API |
|---|---|
| Syscall Use |
Show More
|
| Process Shell Execute |
|
| Anti Debug |
|
Shell Command Execution
Shell Command Execution
This section lists Windows shell commands that are run by the samples in this family. Windows Shell commands are often leveraged by malware for nefarious purposes and can be used to elevate security privileges, download and launch other malware, exploit vulnerabilities, collect and exfiltrate data, and hide malicious activity.
C:\WINDOWS\SysWOW64\rundll32.exe C:\WINDOWS\system32\rundll32.exe c:\users\user\downloads\2df1df53dfdbfa246a20b2b69856a7cac00b1b07_0008597216.,LiQMAxHB
|