LockedByte Ransomware
The LockedByte Ransomware is a ransomware Trojan that seems to be distributed through corrupted email spam attachments. Victims of these tactics will receive an email that uses a social engineering tactic to trick the victim into believing that the email was sent from a legitimate source such as a social media website, a bank or a government office. There are numerous ways in which tactics like the LockedByte Ransomware can spread to victims apart from email attachments. These may include social media spam, corrupted advertisements on suspicious websites, and fake files distributed through file sharing networks. Take steps to prevent ransomware attacks like the LockedByte Ransomware, most importantly by having backups of your files.
Table of Contents
This LockedByte may not Set Your Files Free Even Paying Its Ransom
The LockedByte Ransomware does not belong to a known family of ransomware. However, its attack is identical to most encryption ransomware Trojans; the LockedByte Ransomware will search the victim's computer for certain file types and then encrypt them using a strong encryption algorithm. Once files have been encrypted by the LockedByte Ransomware attack, they become unreadable and cannot be recovered without the decryption key. The LockedByte Ransomware targets a wide variety of file types, looking for user generated files such as music, movies, PDFs, and files created with software such as Adobe Photoshop, Microsoft Office, Libre Office, etc.
How the LockedByte Ransomware Carries out Its Attack
The LockedByte Ransomware will encrypt the victim's files using the XOR encryption, making the affected files unreadable. The files that are encrypted by the LockedByte Ransomware will be identified by the LockedByte Ransomware via the addition of the file extension '.[random]' to the end of each file's name. The LockedByte Ransomware demands a large ransom payment of $1000 USD in the form of BitCoins to provide the decryption key and software necessary to restore the files encrypted by the LockedByte Ransomware attack. Essentially, the LockedByte Ransomware takes the victim's files hostage and then demands a ransom to restore them to normal.
The LockedByte Ransomware’s Ransom Note and Demands
After encrypting the victim's files, the LockedByte Ransomware notifies the victim of the attack. To do this, the LockedByte Ransomware will deliver a ransom note to the victim's computer. The LockedByte Ransomware does this by dropping a file on the infected computer, placing it on the computer's desktop and in directories where the LockedByte Ransomware encrypted any content. The LockedByte Ransomware ransom note contains instructions on how to pay and notifies the victim on what has occurred. The following is the full text of the LockedByte Ransomware ransom note:
'Your files have been encrypted by LockedByte
All your files have been encrypted and are now hold for ransom
To receive your files back you will have to pay 1000 dollars worth of bitcoin to the address:
17UomAvt4YEDwNYdpFjotdm7CV1i8jJ16Q
Good luck having your files back
>:-)'
Apart from this text note, the LockedByte Ransomware also will change the victim's desktop image with an image file containing the LockedByte Ransomware's ransom note. Computer users should refrain from following the instructions contained in the LockedByte Ransomware ransom note.
Dealing with a LockedByte Ransomware Attack
It is not unlikely that PC security researchers will release a tool to help computer users recover from the LockedByte Ransomware attack because of the encryption method involved, although this may take quite a lot of time. However, in most ransomware encryption attacks, it may be impossible to recover the affected files without the decryption key. Because of this, prevention is the most important step computer users can take to protect their computers and data. The best preventive measure to take in the face of the LockedByte Ransomware is to have file backups on an external memory device or the cloud. Havingcopies of all files allows computer users to recover from the attack quickly without needing to pay the LockedByte Ransomware ransom, in essence making the LockedByte Ransomware attack ineffective since the con artists can no longer demand a ransom payment.
SpyHunter Detects & Remove LockedByte Ransomware
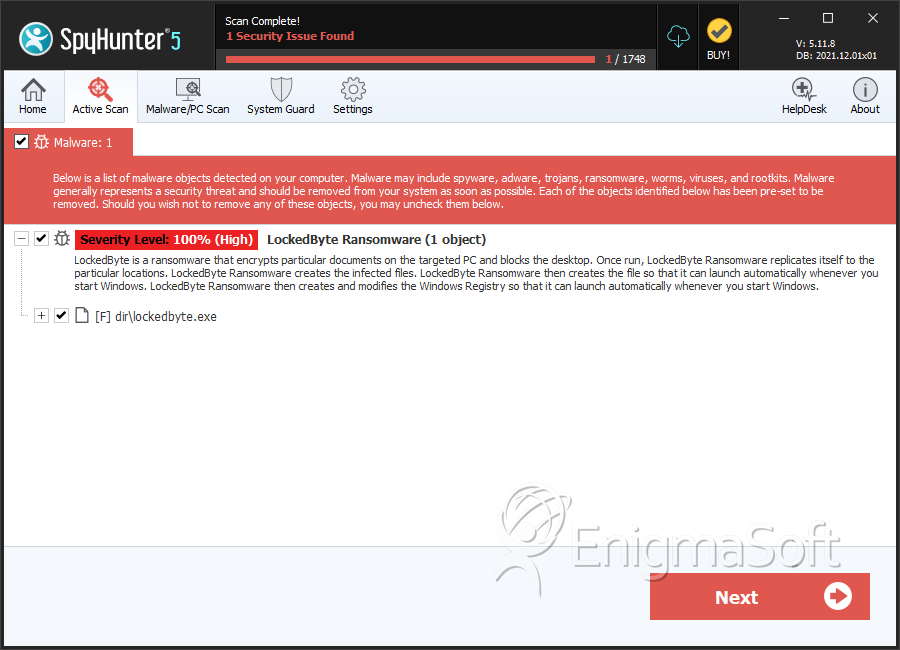
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | lockedbyte.exe | d5c1960a0729722baca09ce52cb7474e | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.