LLTP Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 73 |
| First Seen: | March 22, 2017 |
| Last Seen: | May 2, 2022 |
| OS(es) Affected: | Windows |
The LLTP Ransomware is a ransomware Trojan that seems to be a variant of a known ransomware Trojan named VenusLocker. PC security researchers came across the LLTP Ransomware on March 21, 2017. The LLTP Ransomware seems to be designed to target computer users in Spanish- speaking regions. A closer look at the LLTP Ransomware's code reveals that the LLTP Ransomware was built by rewriting VenusLocker. The LLTP Ransomware is capable of carrying out its attack on the victim without the need for an Internet connection. The LLTP Ransomware adds an extension to encrypted files, a method typical of these attacks. However, the LLTP Ransomware is unique in that it will use different extensions depending on the original type of the affected file.
Table of Contents
The Only Way to Recover Your Files is Having a Backup
Unfortunately, it may not be possible to decrypt the files affected by the LLTP Ransomware currently. Because of this, as with most ransomware Trojans, the best protection against this attack is to have file backups of all data (allowing for easy recovery and rendering the people responsible for the attack completely powerless). If the infected computer is connected to the Internet, the LLTP Ransomware will connect to its Command and Control server to carry out its attack but, as mentioned before, the LLTP Ransomware also can carry out its encryption attack without the need for an Internet connection.
After encrypting its victim's files by using AES encryption, and ensuring that the decryption key is completely inaccessible, the LLTP Ransomware delivers its ransom note. The following is the full text of the LLTP Ransomware ransom note:
'--- the LLTP Ransomware ---
Unfortunately, you are hacked.
1. What happened to my files?
Your personal files, including your photos, documents, videos and other important files on this computer, have been encrypted with RSA-4096, the strongest encryption algorithm. RSA algorithm generates a public key and a private key for your computer. The public key was used to encrypt your files a moment ago. The private key is necessary for you to decrypt and recover your files. Now, your private key is stored on our secret Internet server. And there is no doubt that no one can recover your files without your private key.
For further information about RSA algorithm, please refer to https://en.wikipedia.org/wiki/RSA_(cryptosystem)
2. How to decrypt my files?
To decrypt and recover your files, you have to pay #ramt# US Dollars for the private key and decryption service. Please note that you have ONLY 72 HOURS to complete your payment. If your payment do not be completed within time limit, your private key will be deleted automatically by our server. All your files will be permanently encrypted and nobody can recover them. Therefore, it is advised that you'd better not waste your time, because there is no other way to recover your files except making a payment.
3. How to pay for my private key?
There are three steps to make a payment and recover your files:
1). For the security of transactions, all the payments must be completed via Bitcoin network. Thus, you need to exchange #ramt# US dollars (or equivalent local currencies) to Bitcoins, and then send these Bitcoins (about #btc# BTC) to the following address. 19fhNi9L2aYXTaTFWueRhJYGsGDaN6WGcP
2). Send your personal ID to our official email: LLTP@mail2tor.com
Your personal ID is: #id#
3). You will receive a decryptor and your private key to recover all your files within one working day.
4. What is Bitcoin?
Bitcoin is an innovative payment network and a new kind of money. It is based on an open-source cryptographic protocol that is independent of any central authority. Bitcoins can be transferred through a computer or a smartphone withour an intermediate financial institution.
5. How to make a payment with Bitcoin?
You can make a payment with Bitcoin based on Bitcoin Wallet or Based on Perfect Money. You can choose the way that is more convenient for you.
About Based on Bitcoin Wallet
1) Create a Bitcoin Wallet. We recommend Blockchain.info (https://blockchain.info/)
2) Buy necessary amount of Bitcoins. Our recommendations are as follows.
LocalBitcoins.com -- the fastest and easiest way to buy and sell Bitcoins.
CoinCafe.com -- the simplest and fastest way to buy, sell and use Bitcoins.
BTCDirect.eu -- the best for Europe.
CEX.IO -- Visa / MasterCard
CoinMama.com -- Visa / MasterCard
HowToBuyBitcoins.info -- discover quickly how to buy and sell Bitcoins in your local currency.
3) As mentioned above, send about #btc# BTC (equivalent to #ramt# USD) to our Bitcoin receiving address.
4) As mentioned above, and then, send us your personal ID via email, you will receive your private key soon.
About Based on Perfect Money
1) Create a Perfect Money account. (https://perfectmoney.is)
2) Visit to PMBitcoin.com. (https://pmbitcoin.com/btc)
input our Bitcoin receiving address in the "Bitcoin Wallet" textbox.
input #ramt# in the "Amount" textbox, the amount of Bitcoin will be calculated automatically.
click "PAY" button, then you can complete you payment with your Perfect Money account and local debit card.
6. If you have any problem, please feel free to contact us via official email.
Best Regards
The LLTP Locker Team'
The LLTP Ransomware Attack and Its Similarities to Other Ransomware Trojans
Encrypting the victims' files and then demanding payment of a ransom is one of the most common methods followed by current ransomware Trojans active today. The attack is especially effective because the victim's files remain encrypted even if the threat infection itself is deleted (which was not the case with other forms of ransomware such as those based on lock screens). The best way to deal with threats like the LLTP Ransomware is to take preventive measures. In the case of the LLTP Ransomware, PC security researchers advise the use of file backups combined with a reliable security program that is fully up-to-date and education on how to recognize and avoid the tactics used to deliver threats like the LLTP Ransomware.
SpyHunter Detects & Remove LLTP Ransomware
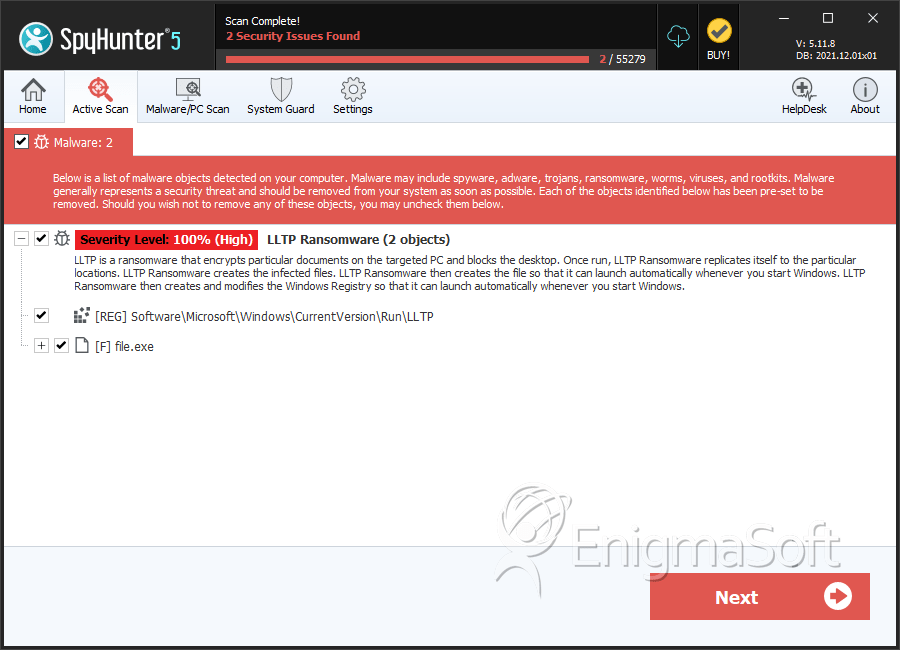
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 4eaac55ddd279d402d0aba8707b9ca5b | 1 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.