LIGMA Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 4 |
| First Seen: | September 13, 2018 |
| Last Seen: | October 11, 2018 |
| OS(es) Affected: | Windows |
The LIGMA Ransomware is an encryption ransomware Trojan that was first observed on September 8, 2018. Typically, the LIGMA Ransomware is delivered using spam email attachments. Once the LIGMA Ransomware is installed, it is used to take the victim's files hostage so that the victim will need to make a payment in exchange for access to the compromised files.
Table of Contents
How the LIGMA Ransomware Carries Out Its Attack
The LIGMA Ransomware uses a strong encryption algorithm to make the victim's files inaccessible. The LIGMA Ransomware targets the user-generated files, which may include media files, various document types, databases and numerous others. The following are examples of the files that are targeted by these attacks:
.jpg, .jpeg, .raw, .tif, .gif, .png, .bmp, .3dm, .max, .accdb, .db, .dbf, .mdb, .pdb, .sql, .dwg, .dxf, .cpp, .cs, .h, .php, .asp, .rb, .java, .jar, .class, .py, .js, .aaf, .aep, .aepx, .plb, .prel, .prproj, .aet, .ppj, .psd, .indd, .indl, .indt, .indb, .inx, .idml, .pmd, .xqx, .xqx, .ai, .eps, .ps, .svg, .swf, .fla, .as3, .as, .txt, .doc, .dot, .docx, .docm, .dotx, .dotm, .docb, .rtf, .wpd, .wps, .msg, .pdf, .xls, .xlt, .xlm, .xlsx, .xlsm, .xltx, .xltm, .xlsb, .xla, .xlam, .xll, .xlw, .ppt, .pot, .pps, .pptx, .pptm, .potx, .potm, .ppam, .ppsx, .ppsm, .sldx, .sldm, .wav, .mp3, .aif, .iff, .m3u, .m4u, .mid, .mpa, .wma, .ra, .avi, .mov, .mp4, .3gp, .mpeg, .3g2, .asf, .asx, .flv, .mpg, .wmv, .vob, .m3u8, .dat, .csv, .efx, .sdf, .vcf, .xml, .ses, .qbw, .qbb, .qbm, .qbi, .qbr , .cnt, .des, .v30, .qbo, .ini, .lgb, .qwc, .qbp, .aif, .qba, .tlg, .qbx, .qby , .1pa, .qpd, .txt, .set, .iif, .nd, .rtp, .tlg, .wav, .qsm, .qss, .qst, .fx0, .fx1, .mx0, .fpx, .fxr, .fim, .ptb, .ai, .pfb, .cgn, .vsd, .cdr, .cmx, .cpt, .csl, .cur, .des, .dsf, .ds4, , .drw, .eps, .ps, .prn, .gif, .pcd, .pct, .pcx, .plt, .rif, .svg, .swf, .tga, .tiff, .psp, .ttf, .wpd, .wpg, .wi, .raw, .wmf, .txt, .cal, .cpx, .shw, .clk, .cdx, .cdt, .fpx, .fmv, .img, .gem, .xcf, .pic, .mac, .met, .pp4, .pp5, .ppf, .nap, .pat, .ps, .prn, .sct, .vsd, .wk3, .wk4, .xpm, .zip, .rar.
The LIGMA Ransomware has one additional nasty component apart from encrypting the victim's files: the LIGMA Ransomware encrypts the Master Boot Record on the victim's computer, making it impossible to start up the infected computer. The files encrypted by the LIGMA Ransomware renames the encrypted files with the file extension '.ForgiveME' added to the affected files' names.
The LIGMA Ransomware’s Demands
Unfortunately, the LIGMA Ransomware functions as a data wiper essentially since it's impossible to restore files encrypted on the victim's computer. Even if the Master Boot Record is fixed, the compromised files will remain inaccessible. The LIGMA Ransomware delivers the following message to the victim in the form of a new desktop wallpaper image, composed of a green text over a black background:
'YOUR PC LIGMA BALLS xD
This PC is dead because you did n't follow the rules.
Your PC will never work again.
NOTE: Even if you fix the MBR your Your PC Is Dead.
Entire Registry is Fucked and your files are infected.'
PC security experts strongly advise PC users to abstain from contacting the criminals responsible for the LIGMA Ransomware attack. Unfortunately, if the LIGMA Ransomware was capable of seizing your files, it will not be possible to restore them, and restarting Windows will not work. In general, it will be necessary to wipe the affected drives and reinstall Windows. Once this has been done, you will need to restore the files affected by the LIGMA Ransomware through the use of backup copies. As with most ransomware Trojans, the best protection is to have file backups. Backup copies of your files make it possible to recover your files from the backups. Otherwise, the data compromised by the LIGMA Ransomware attack will damage the files in a way that they will be gone permanently. Because of this, prevention is essential. Computer users should ensure that they have a security program capable of dealing with this threat kind and handle spam email messages with caution.
SpyHunter Detects & Remove LIGMA Ransomware
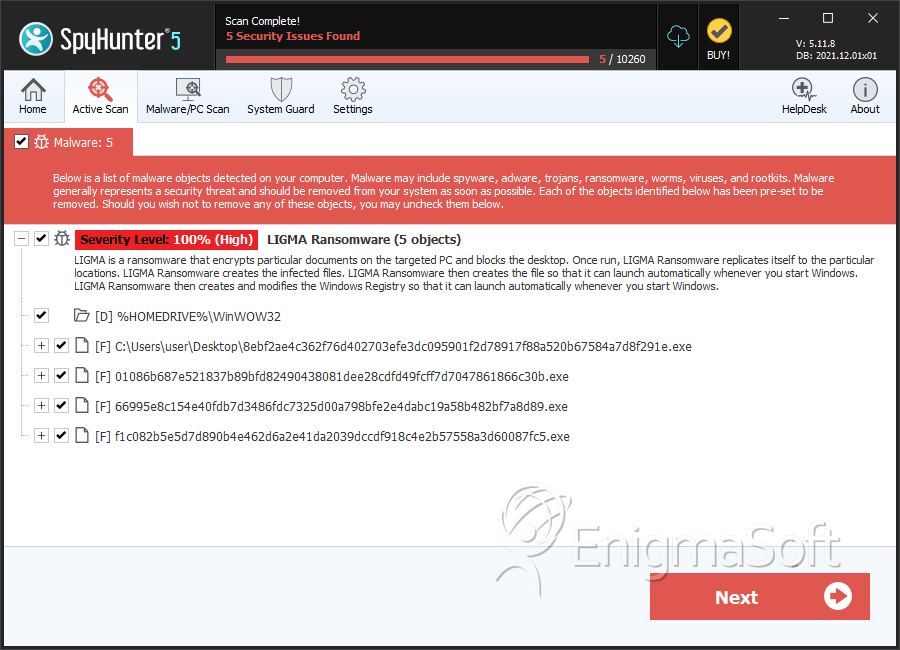
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | 8ebf2ae4c362f76d402703efe3dc095901f2d78917f88a520b67584a7d8f291e.exe | 598e8e939e1ed451c3e32d9192c23450 | 1 |
| 2. | 01086b687e521837b89bfd82490438081dee28cdfd49fcff7d7047861866c30b.exe | 5d5c9392e6c3b6ef5c4d79c0bc2eaac9 | 0 |
| 3. | 66995e8c154e40fdb7d3486fdc7325d00a798bfe2e4dabc19a58b482bf7a8d89.exe | ad2f442ff0d0758bab58d9d6cd99fd46 | 0 |
| 4. | f1c082b5e5d7d890b4e462d6a2e41da2039dccdf918c4e2b57558a3d60087fc5.exe | 3ac5262b15ad7d7bc3e8047f91b3c973 | 0 |
Directories
LIGMA Ransomware may create the following directory or directories:
| %HOMEDRIVE%\WinWOW32 |

