L4NC34 Ransomware
Most ransomware threats target regular users and lock the contents of their computers with an encryption algorithm only to then ask them for a ransom fee in exchange for the decryption key they need to recover their data. However, this is not exactly the case with the newly uncovered L4NC34 Ransomware. The L4NC34 Ransomware targets websites only. According to reports, so far, the L4NC34 Ransomware has managed to infiltrate several Web pages.
Table of Contents
Propagation and Encryption
It is not yet known how are the cyber crooks behind the L4NC34 Ransomware infiltrating the targeted websites. Malware researchers speculate that the perpetrators may be relying on software vulnerabilities or poorly protected servers that are easy to exploit. As soon as the L4NC34 Ransomware manages to infiltrate the targeted website, it will lock all its files. The Web page’s files will be renamed because the L4NC34 Ransomware appends a ‘.crypt’ extension to the names of all the locked files. This means that an image called ‘home-page.jpeg’ will be renamed as ‘home-page.jpeg.crypt’ after the encryption process has been completed successfully.
What is L4NC34?
The team at Sucuri recently spotted the L4NC34 virus, which appeared to encrypt files and change their extension to “.crypt.”
The list of infected files included the same kind of ransom note that you’d see with a ransomware attack. There was a difference, though; this ransom note was a PHP file with interactive buttons. The image below shows what happens when you access the PHP file.
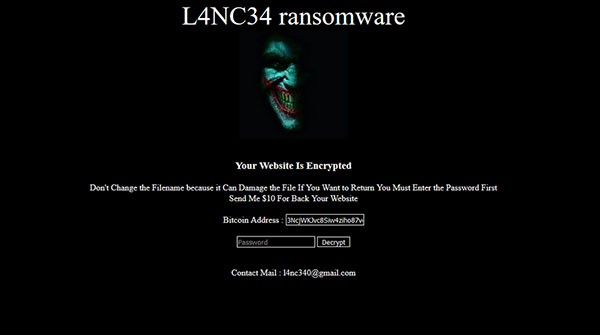
L4NC34 lock screen
It’s worth noting that the ransomware only asks for a small fee to decrypt the files. Instead of asking for hundreds, if not thousands, of dollars, L4NC34 asks for a pittance of just $10. It’s unclear whether the attackers are showing some kind of benevolence or just looking to get as many people as possible to pay. Some people would rather pay $10 than deal with the hassle of restoring their data personally.
Sucuri took a closer look at the coding in the PHP file, which used some basic base64 encoding. It didn’t take long to decode the program and start to see some interesting elements of the code. The team quickly identified the parts of the code that displayed the ransom note and the code that decrypted files.
The PHP file required, as would be expected, some kind of external input to decrypt the data. This external input would take the form of a decryption key. Plug in the key and hit decrypt, and the process begins.
A Closer Look at the Code of L4NC34
The code contained some interesting elements worth paying attention to, including;
$input = $_POST['pass'];
$pass = "9c6679accb84e3ef938b1f4c24158355";
if(isset($input)) {
if(md5($input) == $pass) {
This bit of code verifies that the password on the page is the same as the hardcoded md5 hash. This stands out as the key usually wouldn’t be hardcoded in like this. If the key were hardcoded, though, then it would explain the encrypted files.
Speaking of encryption, this next bit of code covers the decryption process;
function decfile($filename){
if (strpos($filename, '.crypt') === FALSE) {
return;
}
$decrypted = gzinflate(file_get_contents($filename));
file_put_contents(str_replace('.crypt', '', $filename), $decrypted);
unlink('crypt.php');
unlink('.htaccess');
unlink($filename);
echo "$filename Decrypted !!!
";
}
Once again, there’s nothing particularly complicated about the coding. The decryption process appears to take the contents of the file into account and gzinflate them to bring them back to normal. It seems like the encryption process was just the hackers applying a gzdeflate to the data and changing the names on files.
Decrypting Files Affected by L4NC34
Given that the way to solve a gzdeflate is to apply a gzinflate, the researchers applied their own gzinflate to see if it would work. Researchers altered the script of the original PHP file to make it perform the decryption process.
The team ran the script through the terminal to execute it, and their genius move paid off. The file they tested was restored to normal with no need to pay a ransom fee. The next step was to check the bitcoin wallet of the attacker, just to see if anyone had paid them. Investigations showed that there was no activity with the wallet address, meaning that no one had ever paid the ransom.
L4NC34 Ransomware Attack is Not The End-All
A ransomware attack can seem scary, but it isn’t always the end of the world. As L4NC34 proves, sometimes ransomware is barely an issue. With that said, many ransomware attacks do have significant implications. Over $7.5 billion was lost to ransomware attacks in 2019. There’s no guarantee that data will be restored should the ransom be paid either. Take every precaution to protect yourself, your computer, your website, and your business against ransomware.

