KingOuroboros Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 3 |
| First Seen: | June 27, 2018 |
| OS(es) Affected: | Windows |
The KingOuroboros Ransomware is an encryption ransomware Trojan that seems to be based on CryptoWire, an open-source ransomware Trojan that was first observed in October of 2016. There have been multiple variants in this ransomware family, with the KingOuroboros Ransomware being one of the latest. It seems that one of the leading ways in which the KingOuroboros Ransomware is delivered to victims, like many other encryption ransomware Trojans, is through corrupted spam email attachments, which use embedded macro scripts to download and install the KingOuroboros Ransomware onto the victim's computer.
Table of Contents
How the KingOuroboros Ransomware Carries Out Its Attack
Once the KingOuroboros Ransomware is installed onto the victim's PC, it will use the AES encryption to make the victim's files inaccessible. The KingOuroboros Ransomware will target the user-generated files in its attack, which may include numerous documents, media files, databases and various other file types. The following are some of the file extensions that are typically targeted in attacks like the KingOuroboros Ransomware:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
The KingOuroboros Ransomware also will delete the Shadow Volume Copies of the files encrypted by the attack and will mark these files with the string 'king_ouroboros,' added to the end of the affected file's name. The affected file will preserve, however, its original file extension, but will not be recognized when the victim attempts to open it.
The KingOuroboros Ransomware’s Ransom Demands
The KingOuroboros Ransomware will deliver a program window titled 'Delta' after encrypting the victim's files. This window will notify the victims that their files were encrypted and contained the demanded ransom, which must be in Bitcoin, and supposedly will pay for a decryptor. The text on the KingOuroboros Ransomware ransom note reads:
'Your files has been safely encrypted
Encrypted files: [random number]
[follows a list of addresses for the encrypted files]
[Buy Bitcoins|BUTTON] [Decrypt Files|BUTTON] [TEXT BOX FOR THE KEY]
The only way you can recover your files is to buy a decryption key
The payment method is Bitcoin. The price is $50 = Bitcoins
After buying hr amount of bitcoins send an email
to king.ouroboros@protonmail.com Your ID: [random characters
We will provide you payment address and your decryption key
You have 72 Hours to complete the payment otherwise your key will be deleted.'
Unless there's no other solution, the payment of the KingOuroboros Ransomware ransom or following the instructions in the KingOuroboros Ransomware's ransom demand is highly discouraged. Instead, steps should be taken to prevent these kinds of attacks in the first place.
Preventive Steps You Can Take to Avoid the KingOuroboros Ransomware Attacks
A security program that is fully up-to-date is fundamental in preventing attacks like the KingOuroboros Ransomware, which are becoming more common increasingly. Apart from a reliable anti-virus application, it is important to have file backups. File backups allow computer users to restore their files after their attack without having to interact with the criminals responsible for the KingOuroboros Ransomware infection. Unfortunately, it is not possible to restore the files encrypted in attacks like the KingOuroboros Ransomware currently, due to the strength and nature of the encryption method used to take the files hostage.
SpyHunter Detects & Remove KingOuroboros Ransomware
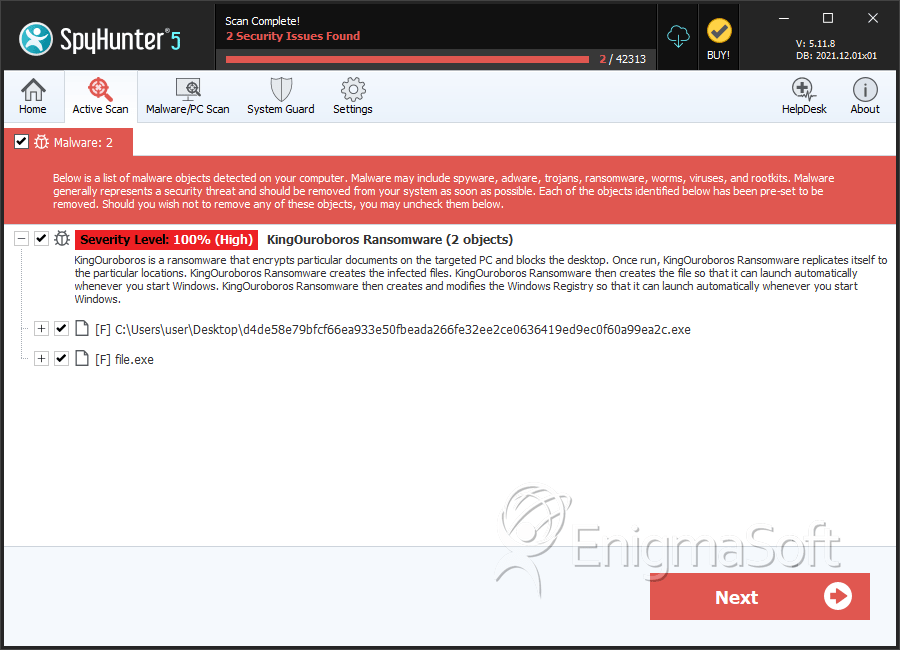
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | d4de58e79bfcf66ea933e50fbeada266fe32ee2ce0636419ed9ec0f60a99ea2c.exe | 8893004b04b4436eb47e9b504b7a437f | 3 |
| 2. | file.exe | a50051fb910aabf6e953f813b4212369 | 0 |

