JuicyLemon Ransomware
The JuicyLemon Ransomware is a ransomware infection that is used to harass computer users, encrypting their files and demanding the payment of an enormous ransom to recover their files. The JuicyLemon Ransomware's ransom, which should be paid in BitCoins can exceed one thousand Euro sometimes! The files that have been encrypted using the JuicyLemon Ransomware cannot be decrypted without access to the decryption key. The JuicyLemon Ransomware takes the victim's files hostage effectively, demanding that the computer users pay money to give them the decryption key. It is currently not possible to decrypt files encrypted by the JuicyLemon Ransomware without the decryption key. Because of this, the best protection against the JuicyLemon Ransomware are adequate preventive measures, using a reliable anti-malware program, a good anti-spam filter, and keeping backups of all files on an external device. Malware analysts strongly advise computer users to avoid unsolicited email attachments or clicking on embedded links.
Table of Contents
How the JuicyLemon Ransomware may be Delivered to a PC
In most cases, the JuicyLemon Ransomware enters a computer through a corrupted email message, in an attached file or embedded links. These email messages may be designed to trick computer users into opening this attached content. For example, the email may impersonate a shipping company, claiming that the attachment contains an invoice or is tracking a certain delivery. The JuicyLemon Ransomware is designed to infect computer running the Windows operating system, and may affect all versions of Windows ranging from Windows XP all the way to Windows 10. After the JuicyLemon Ransomware enters a computer, it searches for data files with extensions matching its configuration files, including the following:
.sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odt.
When the JuicyLemon Ransomware finds files with these extensions, the JuicyLemon Ransomware changes their file extensions and drops a ransom note containing information on how to pay the ransom amount. These ransom notes take the form of text and HTML files and are dropped in every directory where the JuicyLemon Ransomware encrypted files. The JuicyLemon Ransomware will also change the affected computer's Desktop wallpaper image into a version of its ransom note. The ransom note instructs computer users on how to buy BitCoins and pay the JuicyLemon Ransomware ransom to recover from an attack.
Protecting Your Computer from the JuicyLemon Ransomware
Prevention is the best way to deal with threats like the JuicyLemon Ransomware. Malware analysts strongly advise computer users to use a reliable anti-malware program that is fully up-to-date. You should use a reliable anti-spam filter and avoid opening any file attachments or embedded links in unsolicited email messages. Malware analysts also recommend that computer users backup all files regularly, to avoid having to pay the ransom to recover the files encrypted by threats similar to the JuicyLemon Ransomware, which, unfortunately, are becoming increasingly common.
SpyHunter Detects & Remove JuicyLemon Ransomware
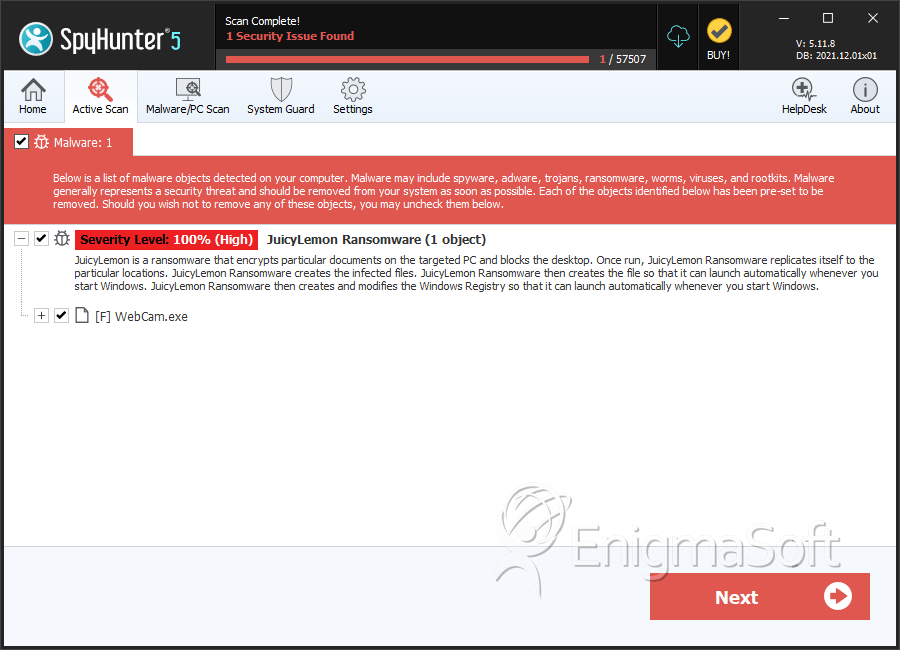
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | WebCam.exe | 5ee28035c56c048580c64b67ec4f2124 | 0 |

