HydraCrypt Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 15 |
| First Seen: | February 4, 2016 |
| Last Seen: | March 13, 2021 |
| OS(es) Affected: | Windows |
The HydraCrypt Ransomware is a Trojan that is used by con artists to lock the data of infected users and demand payment for the release of a decryption key. The HydraCrypt cryptomalware is deployed to users using the Angler Exploit Kit, which is loaded on a remote server. Several compromised sites are known to propagate the HydraCrypt Ransomware among which are Drivers-softprotect.eu, Vyetbr.tk and Harbourfrontcentre.com. Many infections with the HydraCrypt Ransomware are facilitated with the Botime Trojan-Dropper that might plant the executable of the HydraCrypt Ransomware in the System32 folder under the Windows directory. Malware researchers note that the HydraCrypt Ransomware is relatively simple in behavior and is similar to the Buddy Ransomware. Once the user has been infected with the HydraCrypt Trojan, it would register itself to be run on the next system boot up. The encryption process would run in the background while the user is surfing the Internet and playing games.
Files that are encrypted by the HydraCrypt Ransomware would feature an icon that is a blank sheet of paper and has the .HYDRACRPT file extension. Additionally, the .HYDRACRPT suffix is followed by an identifier that is unique to each infected user. For example, the file Family_Reunion.JPG is going to be encrypted according to the model .hydracrypt_ID_. Victims of the HydraCrypt Ransomware are given seventy-two hours to contact the handles of the HydraCrypt Ransomware via email and pay the ransom. The email address can be found in a TXT file named README_DECRYPT_HYDRA_ID_ that is placed in every folder containing the .HYDRACRYPT files inside. Computer users are not advised to pay the ransom to the handlers of the HydraCrypt cryptomalware to discourage the development of that sort of software. Also, users have absolutely no guarantee that they will receive the decryption key for their data. A better choice is to use a backup solution to protect your files from accidental deletion and cryptomalware. You should keep your software up-to-date and employ the services of a trusted anti-malware application to prevent the infiltration of the HydraCrypt Ransomware.
SpyHunter Detects & Remove HydraCrypt Ransomware
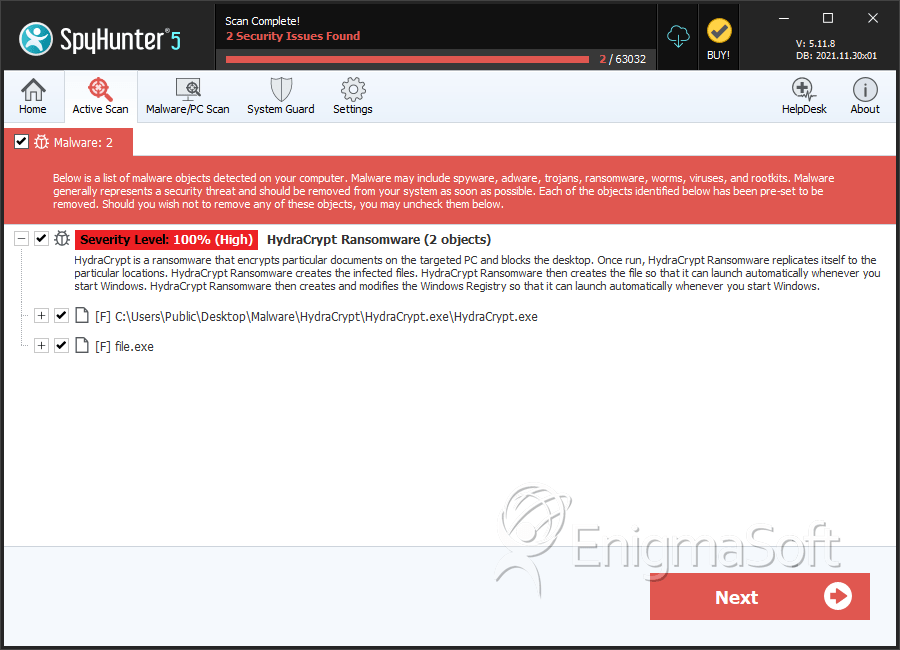
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | HydraCrypt.exe | 08b304d01220f9de63244b4666621bba | 4 |
| 2. | file.exe | 7469c1ee0827a289fa775f4a5656e5f9 | 3 |
| 3. | file.exe | 5f2d13576e4906501c91b8bf400e0890 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.