HSDFSDCrypt Ransomware
The HSDFSDCrypt Ransomware is another file encoder Trojan that is aimed at German-speaking users primarily. The threat to Windows systems was reported on November 6th, 2017. The investigation that followed unveiled that the HSDFSDCrypt Ransomware Trojan was installed on machines via corrupted macro scripts embedded into fake messages from Amazon, PayPal, Internet and electricity suppliers. The HSDFSDCrypt Ransomware is categorized as a generic crypto-threat that incorporates modified AES and RSA ciphers, which are used to encipher the targeted data and urge the user to pay 0.12 Bitcoin (866 USD/750 EUR).
As you may know, crypto-threats don't remove and add content to systems, but they are meant to change the structure of data containers. As a consequence, the data owner is rendered unable to load data such as photos, databases, multimedia content, office documents and eBooks. The HSDFSDCrypt Ransomware functions similarly to the DolphinTear Ransomware and the Versiegelt Ransomware, but it does not add a file marker to the encrypted files. Instead, the HSDFSDCrypt Ransomware removes all indications of the file type and renames the files to a nonsensical string of characters. That is why the name of the threat may seem rather odd to some users. For example, 'Vitreous orthoclase minerals.png' might be renamed to something like 'BFFA2AADXKIGJTHFBRSWJWO' and the file is likely to feature a generic blank icon, which Windows uses to represent unknown objects.
The ransom note is saved as 'Wo_sind_meine_Dateien.html' that is German for 'Where_is_my_data.html.' The message appears on the screen after the Trojan has made sure the volume snapshots made by Windows are deleted securely. PC security experts recommend users eliminate the HSDFSDCrypt Ransomware using a trusted anti-malware scanner and proceed to boot backups made with third-party software. Archives and backups from cloud-based services such as Dropbox can help you rebuild your file structure relatively fast. The ransom note utilized by the HSDFSDCrypt Ransomware reads (translated from German):
'Your files have been encrypted!
Dear Sir or Madam,
As you've already noticed, all your files have been encrypted.
How do I get access to my files?
To successfully decrypt your files, you need our special software and its decrypt key.
Where can I get the software?
The decryption software can be purchased from us.
The price for the decryption software is 0.12 Bitcoin.
Please note that we only accept Bitcoin for the purchase of the software.
[edit: instructions on how to purchase Bitcoin from respected markets]
ATTENTION!
If we do not notice any payment within 7 days, we assume that you are not interested in decrypting your files. In that case, we will irrevocably delete the decrypt key and your files will be lost forever.
Your files were encrypted with military quality using a 256-bit AES algorithm. We do not recommend wasting time decrypting yourself, it would only cost you extra time and money, but your files would still be encrypted.
bonus
In addition to the decryption software, after successful payment, you will receive instructions on how the malware could reach your system and how you can protect yourself from further attacks in the future!'
AV engines include virus definitions for the latest strains of the HSDFSDCrypt Ransomware and these rules are grouped under the following detection names:
- Malicious_Behavior.SB
- Ransom_Gen.R002C0RK717
- Troj/Ransom-ERX
- Trojan ( 0051b1951 )
- Trojan-Ransom.Win32.Gen.fwu
- Trojan.Ransom.HSDFSDCrypt
- Trojan/Win32.Ransom.C2247202
- Win32.Trojan.Agent.YEONOQ
- a variant of Win32/Filecoder.NOK
SpyHunter Detects & Remove HSDFSDCrypt Ransomware
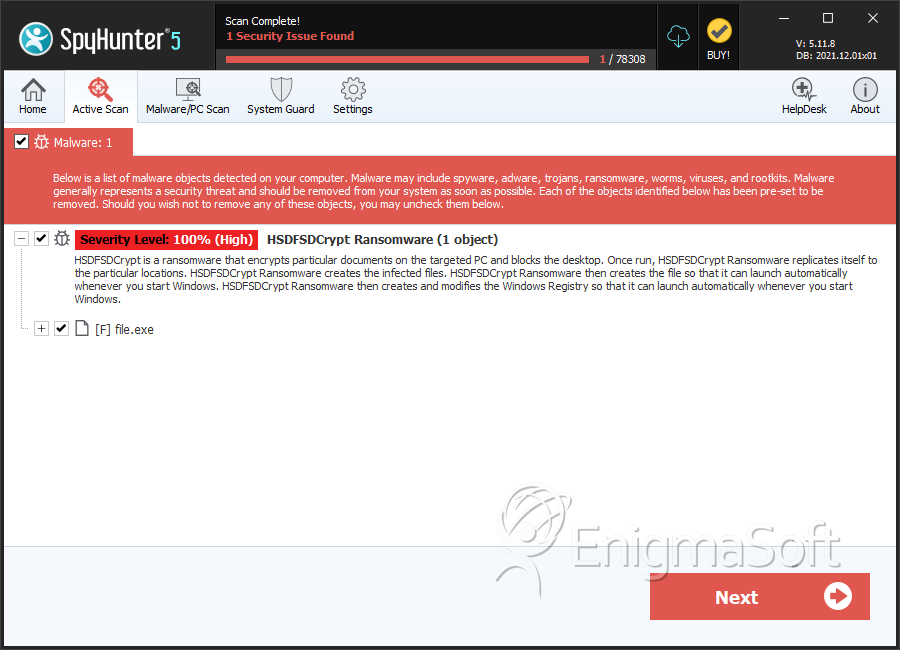
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 870acd0ca66986cc20ab0a655fbc5873 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.