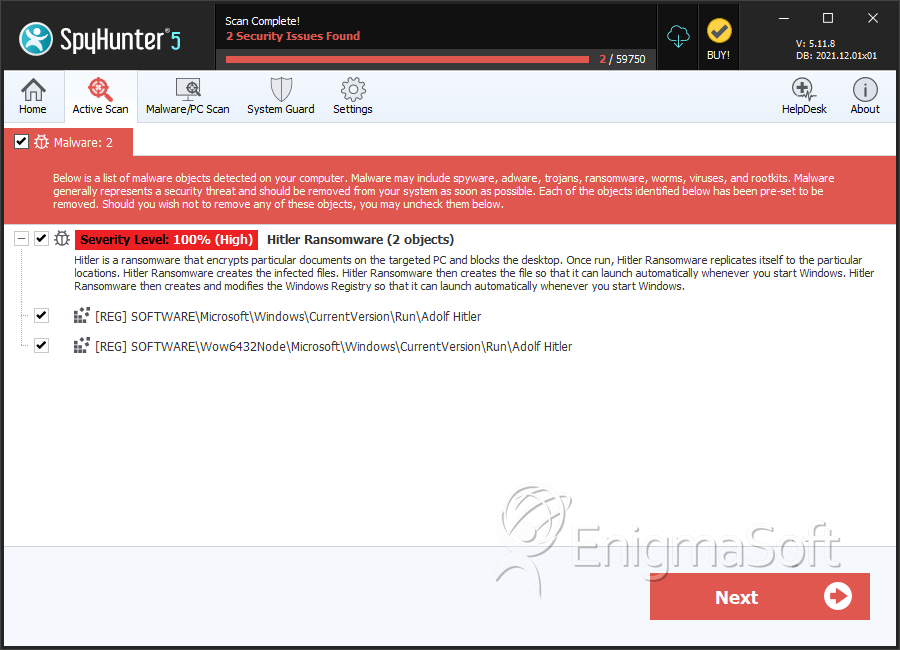
Hitler Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 72 |
| First Seen: | August 8, 2016 |
| Last Seen: | May 2, 2022 |
| OS(es) Affected: | Windows |
The Hitler Ransomware is a ransomware Trojan that is being used in attacks against computer users located in Europe particularly. The Hitler Ransomware deletes its victims' files, a tactic that seems to be increasingly common in ransomware threats that are perhaps created by amateur developers. In the case of the Hitler Ransomware, it is clear that the developers are not especially skillful or that this threat is of a low-quality since even the name of the Hitler Ransomware is misspelled as 'the Hitler Ransonware' in the Hitler Ransomware's lockscreen. The Hitler Ransomware displays a lockscreen with a large picture of Hitler and claims that the victim's files were encrypted. The Hitler Ransomware demands that the victim enters the cash code for a 25 Euro Vodafone Card to decrypt the files. The Hitler Ransomware does not encrypt the victim's files, deleting them instead. This is quite counterproductive, and a tactic that is not used by more advanced threat developers. If victims do not expect their files to be decrypted, then they have no incentive to pay the Hitler Ransomware's or any other ransomware's ransom.
Table of Contents
A Scary Name for a Harmful Attack
The Hitler Ransomware may be a test variant, particularly when looking at comments in its code. The Hitler Ransomware is not designed to encrypt the victims' files. Rather, the Hitler Ransomware removes the extensions on all files in certain directories, displays its lock screen and then begins a one-hour countdown. After the end of this hour, the victim's computer crashes, reboots, and all files in the victim's %UserProfile% will be deleted. The German text in the Hitler Ransomware's code is:
Das ist ein Test
besser gesagt ein HalloWelt
copyright HalloWelt 2016
:d by CoolNass
Ich bin ein Pro
fuer Tools für Windows
Which in English would translates as:
This is a test
rather a Hello World
copyright Hello World 2016
: D by Cool Wet
I am a Pro
for Tools for Windows
When the Hitler Ransomware's executable file runs on the victim's computer, it removes all extensions for files located in the following directories:
%userprofile%\Pictures
%userprofile%\Documents
%userprofile%\Downloads
%userprofile%\Music
%userprofile%\Videos
%userprofile%\Contacts
%userprofile%\Links
%userprofile%\Desktop
C:\Users\Public\Pictures\Sample Pictures
C:\Users\Public\Music\Sample Music
C:\Users\Public\Videos\Sample Videos
The Hitler Ransomware then extracts three files, named chrst.exe, ErOne.vbs, and firefox32.exe and load them into a folder in the %Temp% folder on the victim's computer. The firefox32.exe file will be copied into the Startup folder so that it runs automatically when Windows starts up. The first of these files is used to display the Hitler Ransomware's lockscreen on the victim's computer. After the countdown, the Hitler Ransomware terminates the csrss.exe file process, which causes Windows to stop working and display a Blue Screen of Death. When Windows starts up again, the Firefox32 file will search for certain file processes and terminate them. It will start to delete all files in the victim's %UserProfile% folder automatically. It is possible that computer users can avoid the worst part of the attack if they configure Windows to not start up automatically after it crashes. This would allow access to a security program that could remove the Hitler Ransomware infection before it begins to delete all files. Forcing a shutdown is also a good way to interrupt the Hitler Ransomware's deletion of your files.
How the Hitler Ransomware Attacks a Computer and Its User
The Hitler Ransomware may be either the work of amateurs or a test version of a different threat. For example, con artists may be testing a distribution method or another specific aspect of the threat's attack. The Hitler Ransomware is particularly less sophisticated than most encryption ransomware Trojans, which use advanced encryption algorithms to encrypt the victims' files and may include sophisticated payment methods rather than relying on Vodafone cards (a method that was typical of much older ransomware Trojans). The Hitler Ransomware's attack is not particularly obfuscated and seems to work with simple batch files, which are easy to create and stop.
SpyHunter Detects & Remove Hitler Ransomware


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.