HawkEye Keylogger
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 105 |
| First Seen: | March 23, 2016 |
| Last Seen: | August 15, 2020 |
| OS(es) Affected: | Windows |
The HawkEye Keylogger is a budget-friendly keylogger for wannabe spies that want to start their career in illegal surveillance with limited funds. That is how the HawkEye Keylogger is promoted on its 'official' YouTube channel and Twitter page. What is more, users that are interested in buying the HawkEye Keylogger can use a discount of 10% from Shoocha.com.
Researchers alert that the HawkEye Keylogger may be delivered to potential victims via spam mail and run on the infected system as WindowsUpdate.exe. Antivirus vendors classify the HawkEye Keylogger as a threat and work with law enforcement authorities to limit the distribution of the HawkEye Keylogger and its sales. Experts report that the HawkEye Keylogger can be installed on PCs via compromised remote desktop connections as well and is designed to run within the AppData directory. The HawkEye Keylogger is not what you would call a sophisticated keylogger typically, but it has the basic functionality of one. The HawkEye Keylogger works as a server cl8ient and can run in the system background as long as the infected PC is running.
The HawkEye Keylogger supports various types of connections and may withdraw information from major Web browsers, email managers, and instant messaging clients. Experts note that the HawkEye Keylogger may support:
- File Transfer Protocol (FTP); POP3; IMAP; SMTP; HTTP.
- Web Panels.
- Email clients like Microsoft Outlook, Windows Live Mail, Mozilla Thunderbird, Google Talk, IncrediMail and Fox Mail.
- Browsers like Google Chrome, Internet Explorer, SeaMoneky, SRWare Iron and Mozilla Firefox.
- Apps like Windows Credential Messenger, FileZilla, Valve's Steam platform and screen capturing programs.
- Instant messaging clients like Skype, MSN Messenger, Pidgin, Miranda and PalTakScene.
The HawkEye Keylogger can collect data from the victim's clipboard when the user uses the copy and paste commands. When a computer is infected with the HawkEye Keylogger, the program will send a transmission to its 'Command and Control' server via FTP, which includes the keyboard layout, local data and time, IP and MAC address, OS type and network type. The HawkEye Keylogger may not be as complex as the KeyBase Keylogger, but it can record the user's input in TXT, DOC and DOCX files directly. The HawkEye Keylogger stores the collected data in the main executable instead of using an encrypted vault. The collected information is encoded when being sent only. The HawkEye Keylogger can be detected easily due to its poor coding and lack of effort to remain stealthy. We advise users to seek the help of a credible anti-spyware tool to make sure that the HawkEye Keylogger is removed from their machines and boost their defenses against similar apps.
SpyHunter Detects & Remove HawkEye Keylogger
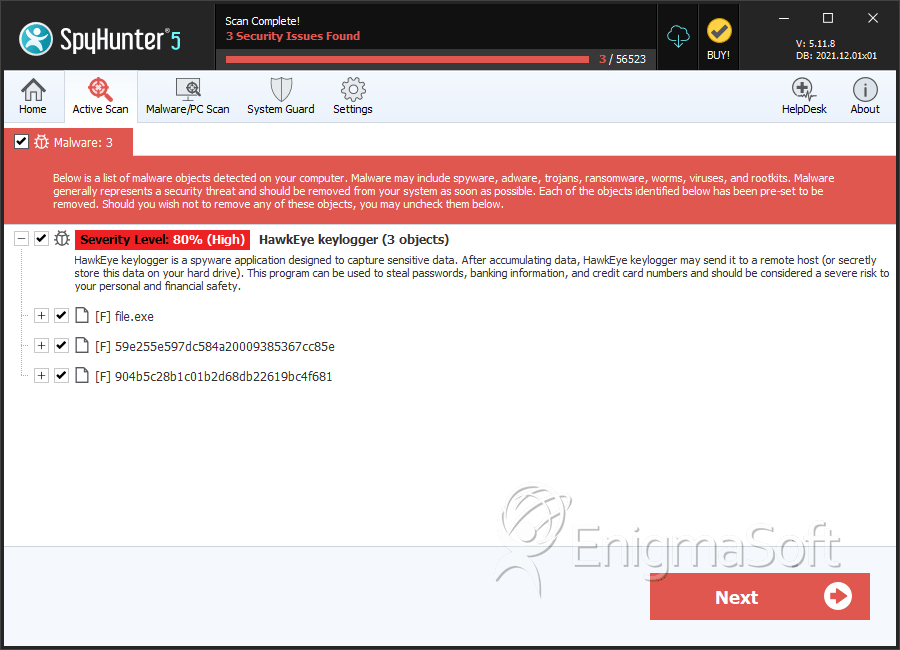
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | 378d167482247b7967f719c7af35f08e | 0 |
| 2. | file.exe | e338403c456b97df7dfabe075486c5c2 | 0 |
| 3. | file.exe | c96e50d83bd43bd8604914bc2e9929c1 | 0 |
| 4. | file.exe | f788bc62f5be5a1f411e0b78d0b563c1 | 0 |
| 5. | file.exe | bc3a8007ebba1fc7c08c1974285abcfa | 0 |
| 6. | file.exe | 09d910627ba09e3626271ec8f620bb33 | 0 |
| 7. | file.exe | 996dc047d99cd08f9d79e018044f8bbd | 0 |
| 8. | file.exe | 1d1b67738f38949d8a7b3a7369d9a953 | 0 |
| 9. | file.exe | 9ddf06e5ed81b26f88acfe0cdea258c6 | 0 |
| 10. | 59e255e597dc584a20009385367cc85e | 59e255e597dc584a20009385367cc85e | 0 |
| 11. | 904b5c28b1c01b2d68db22619bc4f681 | 904b5c28b1c01b2d68db22619bc4f681 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.