KeyBase Keylogger
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 80 % (High) |
| Infected Computers: | 345 |
| First Seen: | June 15, 2015 |
| Last Seen: | March 16, 2023 |
| OS(es) Affected: | Windows |
The KeyBase Keylogger family has been active since February of 2015. The KeyBase Keylogger has numerous features and is sold directly by its authors for $50 USD. The KeyBase Keylogger is being used against various businesses and government agencies and may be delivered by using phishing email messages containing corrupted email attachments and embedded links. There have been at least 300 hundred infected computers since February of 2015. The KeyBase Keylogger has been used to target specific industries, particularly companies in the technology, retail and higher education sectors. PC security analysts consider that the KeyBase Keylogger is threatening and may result in significant losses for targeted businesses and individuals.
Table of Contents
Why Third Parties may Want to Acquire the KeyBase Keylogger
First observed in February of 2015, the KeyBase Keylogger is sold in an online store and the URL keybase(dot)in. The KeyBase Keylogger is distributed on various underground hacking forums and has been active for at least four months. The following features may be included in the KeyBase Keylogger attack:
- The KeyBase Keylogger has an advanced keylogger feature. This allows the KeyBase Keylogger to track keystrokes on the infected computer, keeping track of online passwords, credit card numbers and similar data that may be used to generate revenue.
- The KeyBase Keylogger may be very difficult to remove, in particular when running and scanning the affected computer.
- The KeyBase Keylogger is designed to be easy to use since the KeyBase Keylogger may be sold to inexperienced hackers on these forums. The KeyBase Keylogger has a Web console that allows third parties to monitor the KeyBase Keylogger's functions and attack.
- The KeyBase Keylogger may support various languages and keyboards and allow third parties to isolate sensitive data from the keystrokes typed on affected computers.
The KeyBase Keylogger has Increased in Popularity Since February of 2015 Substantially
Although the KeyBase Keylogger is not particularly sophisticated when compared to other, similar threats, the KeyBase Keylogger has increased in popularity substantially since February of 2015. This is probably because the KeyBase Keylogger has received wide distribution and is not difficult to use for inexperienced attackers. The KeyBase Keylogger may be quite easy to detect on affected computers, and most security programs that are fully updated should be able to notice that the KeyBase Keylogger is logging keystrokes and running in the background. The KeyBase Keylogger may take screenshots and collect data that has been cut or copied into the affected computer. One reason the KeyBase Keylogger is easy to intercept and remove is that the KeyBase Keylogger does not use obfuscation or encryption when connecting to its Command and Control server. This allows PC security researchers to intercept the KeyBase Keylogger quickly and notice when the KeyBase Keylogger is establishing communications.
How the KeyBase Keylogger may be Distributed
Most KeyBase Keylogger attacks may be distributed using mass email programs. These applications that may rely on botnets may be designed to deliver large quantities of corrupted email messages. These may be spam email messages or phishing emails that are more specifically designed to trick specific targets. The attack strategy is not difficult to understand, and may use the following strategies:
- Third parties may identify the target that has the data they want to collect.
- These people may then craft an email designed to con the PC user into opening an affixed file or clicking on an inserted link For example, if the targeted victim is an office, it may try to impersonate an inter-office memo.
- The email may contain an embedded link or email attachment that contains the KeyBase Keylogger and installs the KeyBase Keylogger on the victim's computer when opened. These emails may contain legitimate content as well, to hide the fact that the KeyBase Keylogger is being installed in the background.
SpyHunter Detects & Remove KeyBase Keylogger
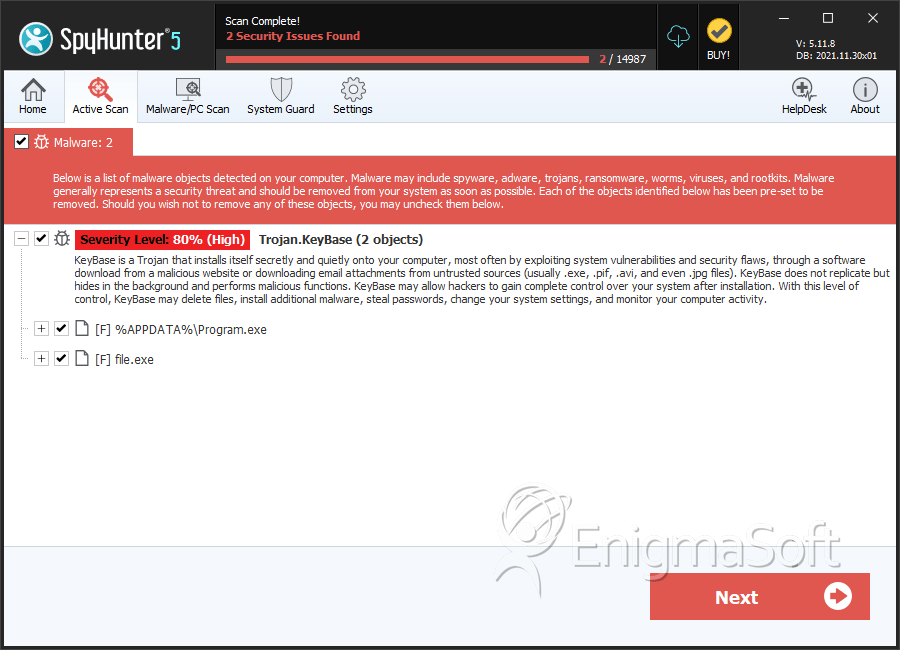
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | program.exe | 63f9f25465353db0187216144ff92f4a | 12 |
| 2. | file.exe | bdadcd9c35687b9913ddd7533f4f47cd | 10 |
| 3. | Program.exe | cd966cb1e35239d1a134b277f6c2159a | 8 |
| 4. | Program.exe | 7563f82019c5d7ad8d58ea2baa1bf625 | 5 |
| 5. | file.exe | 19927de468f347a363e4870c20550b7a | 1 |
| 6. | file.exe | 00cee43716a3251fa97b90705c355095 | 0 |
| 7. | file.exe | 01142b5b5716224da67112100717e191 | 0 |
| 8. | file.exe | e9acb2daf1d7f88a94bf25443abe4d30 | 0 |
| 9. | file.exe | ef6f10079281c2f5caece0c22f435a6e | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.