H34rtBl33d Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 6 |
| First Seen: | April 7, 2018 |
| Last Seen: | January 10, 2019 |
| OS(es) Affected: | Windows |
The H34rtBl33d Ransomware is a file encoder Trojan that was announced on March 30th, 2018. The H34rtBl33d Ransomware Trojan is said to be the work of a group of programmers that claims the name 'D3g1d5.Cyber.Crew.' The group appears to have had a page on Facebook that was deleted shortly after AV companies started their investigation into the H34rtBl33d Ransomware. The threat at hand is programmed to encipher data and attach the '.d3g1d5' suffix to file names. For example, 'Pope Felice Peretti di Montalto.doc' is renamed by the H34rtBl33d Ransomware to 'Pope Felice Peretti di Montalto.doc.d3g1d5.' Affected users may find balloon notifications generated by the Trojan in the bottom right corner of the desktop. Researchers recorded that the notifications produced by the H34rtBl33d Ransomware feature the following text:
'Error! Your file could not be opened Please Decrypt Your File Using H34rt8133d Decrypter' Want Your Files Back? [Click here|BUTTON]'
'Find out here about H34rt8133d Decrypter and how to return it [Click here|BUTTON]'
'Cheaper than wannacry!
H34rt8133d very good ransomware in the world
Ransomware With Cheapest Ransom!
FACT! Ransomware that has infected your computer turned out RANSOMWARE WITH THE LOWEST CHOICE. Want your file back? [Click here|BUTTON]'
The sequence of notifications lead users to load 'scorpionlocker[.]xyz' into their Web browser and include detailed instructions on how to download the TOR Browser from h[tt]ps://www.torproject[.]org/projects/torbrowser. Infected users may consider loading the 'torbox3uiot6wchz[.]onion' domain and write an email to 'blackpanda007@torbox3uiot6wchz[.]onion' if they have no backups and wish to "purchase" the 'H34rtBl33d Decrypter.' It is a bad idea to comply with the demands from the 'D3g1d5.Cyber.Crew' since the H34rtBl33d Ransomware is written poorly, and the chances are slim that the threat actors have a working decryptor.
It is better to ignore the messages from H34rtBl33d Ransomware and run a complete system cleanup with a reputable anti-malware solution. You can restore the encrypted data using backups from the cloud (services like Google Disk, Microsoft's OneDrive and Dropbox), backup images and system recovery disks safely. It may be possible to use system restore points if the H34rtBl33d Ransomware has not deleted them. The best protection against threats like H34rtBl33d Ransomware is to have a portable memory storage device where you can store copies of your files.
SpyHunter Detects & Remove H34rtBl33d Ransomware
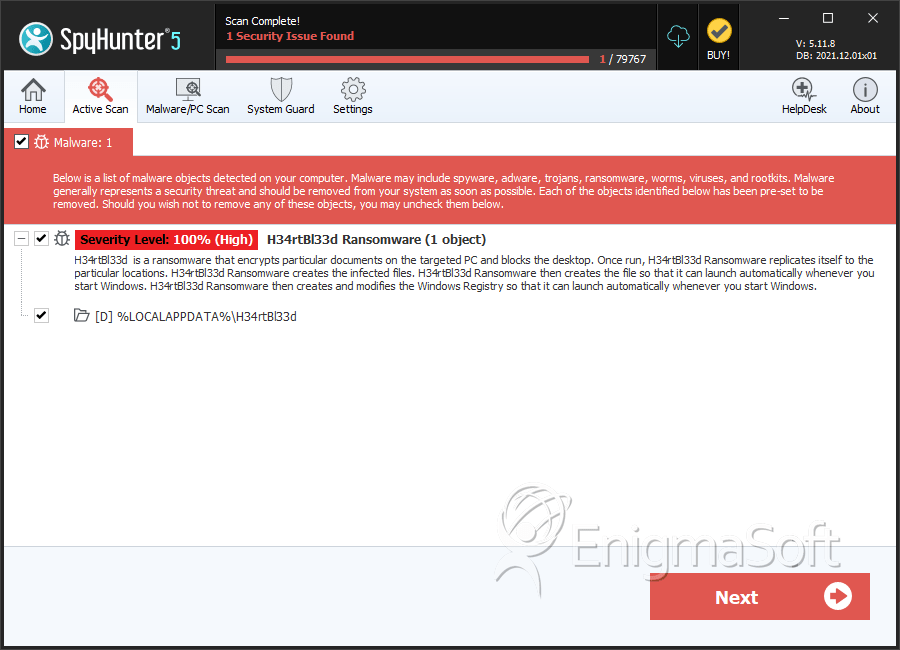
Directories
H34rtBl33d Ransomware may create the following directory or directories:
| %LOCALAPPDATA%\H34rtBl33d |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.