Gryphon Ransomware
Threat Scorecard
EnigmaSoft Threat Scorecard
EnigmaSoft Threat Scorecards are assessment reports for different malware threats which have been collected and analyzed by our research team. EnigmaSoft Threat Scorecards evaluate and rank threats using several metrics including real-world and potential risk factors, trends, frequency, prevalence, and persistence. EnigmaSoft Threat Scorecards are updated regularly based on our research data and metrics and are useful for a wide range of computer users, from end users seeking solutions to remove malware from their systems to security experts analyzing threats.
EnigmaSoft Threat Scorecards display a variety of useful information, including:
Ranking: The ranking of a particular threat in EnigmaSoft’s Threat Database.
Severity Level: The determined severity level of an object, represented numerically, based on our risk modeling process and research, as explained in our Threat Assessment Criteria.
Infected Computers: The number of confirmed and suspected cases of a particular threat detected on infected computers as reported by SpyHunter.
See also Threat Assessment Criteria.
| Threat Level: | 100 % (High) |
| Infected Computers: | 11 |
| First Seen: | August 1, 2017 |
| Last Seen: | July 8, 2019 |
| OS(es) Affected: | Windows |
The Gryphon Ransomware is an encryption ransomware Trojan that was first observed on July 31, 2017. The Gryphon Ransomware may be delivered to victims through the use of corrupted spam email attachments. These spam email attachments may take the form of Microsoft Word documents that use corrupted macro scripts to download and install the Gryphon Ransomware onto the victim's computer. This is one of the reasons why you should disable macros on your word processor unless they are absolutely necessary. The Gryphon Ransomware infects computer users with the Windows operating system and runs as an executable file named 'payload.exe' on the infected computer. The Gryphon Ransomware poses a threat to the computer users' data, and you should take preventive measures to limit the extent of the damage these attacks can cause.
Table of Contents
The Legendary Monster that Makes Your Files Useless
The Gryphon Ransomware is nearly identical to the numerous other encryption ransomware Trojans that are active currently. Like the others, the Gryphon Ransomware will use the AES 256 encryption to make the victim's files inaccessible. The Gryphon Ransomware will encrypt these files using a strong encryption algorithm, prioritizing the files that are user-generated such as media files, images, and files associated with commonly used software such as WinRAR, Microsoft Office, Adobe Photoshop, and numerous others. Once the files have been encrypted by the Gryphon Ransomware, they are no longer recoverable if you don't have the decryption key, which the con artists hold in their possession. The Gryphon Ransomware establishes a connection with its command and control servers and demands a ransom after encrypting the victim's files.
The Gryphon Ransomware’s Ransom Demand
The main purpose of ransomware Trojans like the Gryphon Ransomware is to demand a ransom payment from the victim. To do this, the Gryphon Ransomware will display a ransom note, which makes it clear that the victim will not regain access to the affected files until a ransom is paid. The Gryphon Ransomware delivers its ransom in the form of a text file named 'HELP.txt,' which is dropped on the infected computer's desktop. The full text of the Gryphon Ransomware ransom note is:
'Gryphon Ransomware
Your documents, photos, databases and other important files have been encrypted cryptographically strong, without the original key recovery is impossible!
To decrypt your files you need to buy the special software – 'GRYPFON DECRYPTER' Using another tools could corrupt your files, in case of using third party software we dont give guarantees that full recovery is possible so use it on your own risk.
If you want to restore files, write us to the e-mail: test2
In subject lite write 'encryption' and attach your ID in body of your message
also attach to email 3 crypted files. (files have to be less than 2 MB)
It is in your interest to respond as soon as possible to ensure the restoration of your files, because we won't keep your decryption keys at our server more than one week in interest of our security.
Only in case you do not receive a response from the first email address withit 48 hours, please use this alternative email adress: test3
Your personal identification number:
[Victim's ID]
the Gryphon Ransomware'
Security researchers counsel computer users to refrain from writing to the email addresses associated with the Gryphon Ransomware. Instead, they should take preventive measures to ensure that their files can be recovered after an attack.
Recovering from a Gryphon Ransomware Infection
The best protection against the Gryphon Ransomware and similar attacks is to have file backups. If computer users have a backup copy of their files on an external memory device, then they can simply recover the files from the backup without needing to pay the Gryphon Ransomware ransom. File backups are the best protection against these attacks, taking away all the leverage from the people operating the Gryphon Ransomware. It is also crucial to use a reliable security program that is fully up to date.
SpyHunter Detects & Remove Gryphon Ransomware
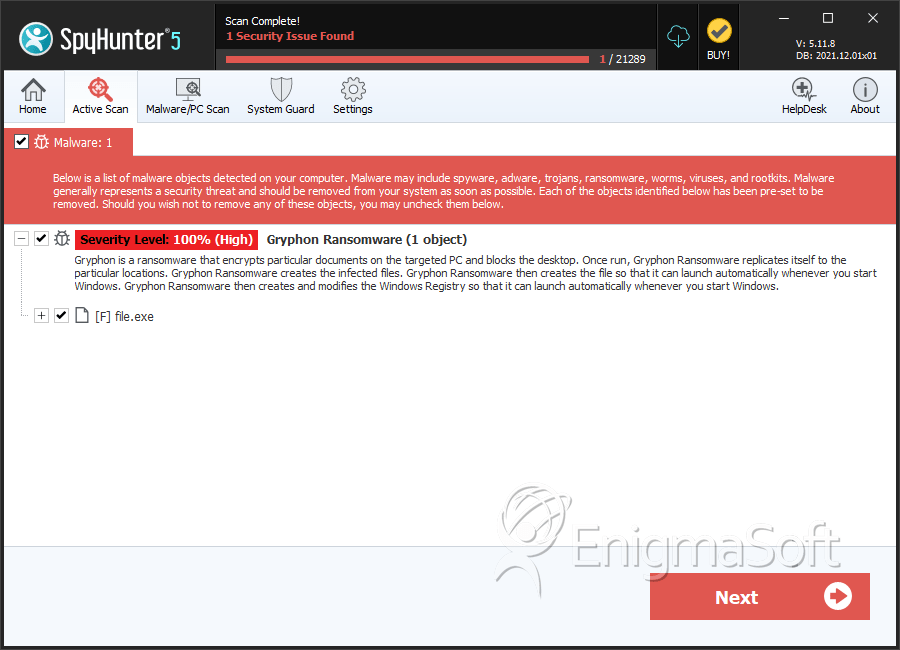
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | dd337ddd0a748423e9c9ef99f291de26 | 0 |
| 2. | file.exe | 6a6727430317ffca1dbffd12acf890bb | 0 |

