Gomme Ransomware
The Gomme Ransomware is an encryption ransomware Trojan. Threats like the Gomme Ransomware are designed to make the victim's files inaccessible. To do this, ransomware Trojans like the Gomme Ransomware will use a strong encryption algorithm to encrypt the victim's files. The decryption key that must be used to recover the affected files is stored on a remote server, away from the reach of the victim or PC security analysts. Once the Gomme Ransomware encrypts the victim's files, it will demand a ransom payment in exchange for it. The Gomme Ransomware and similar threats are designed to extort victims, demanding outlandish sums of money after taking the victims' files hostage.
Table of Contents
This Updated Version of the Gomme Ransomware can Harm Your Files
The Gomme Ransomware was first observed in an early test version in late May of 2017. The Gomme Ransomware's code was observed on an online anti-virus platform (con artists may upload versions of their threats to these websites to test whether they can bypass commonly used anti-virus techniques). In its early version, the Gomme Ransomware crashed and was not capable of carrying out an effective attack. However, it is likely that an updated version of the Gomme Ransomware has been released since May 2017, which may be capable of carrying out an effective encryption ransomware attack.
How the Gomme Ransomware Carries out Its Attack
By studying the Gomme Ransomware's code, it was noticed that the Gomme Ransomware is designed to encrypt many standard file types, especially the user-generated files such as Microsoft Office documents or audio and video files. As soon as the Gomme Ransomware encrypts a file, it will add the file extension '.gommemode' to the end of its name, after the file's original extension. Once the Gomme Ransomware encrypts the file, it will become inaccessible and can only be recovered by deciphering it using the Gomme Ransomware's decryption key (which is in the con artists' possession).
The Gomme Ransomware’s Ransom Note
The Gomme Ransomware is designed to deliver a ransom note in a program window. The Gomme Ransomware's ransom note alerts the victim of the attack and includes instructions on how to make a ransom payment. The ful-text of the Gomme Ransomware's ransom note is:
'=====Gomme Ransom=====
ALL OF YOUR FILES HAVE BEEN ENCRYPTED!
Everything, Music, Documents, Programs etc, has been encrypted!
WARNING: IF YOU RESTART YOUR COMPUTER WE WON'T BE ABLE TO RESTORE YOUR FILES & YOU WILL LOSE THEM FOREVER!
How can I get my files back?
You will need to pay $25, as soon as you did, you will receive your files back.
You will find the 'TOR Browser' on your desktop.
lf you don't own BTC, purchase some at paxful.com or localbitcoins.
SEND THE MONEY TO THIS ADDRESS:
3FryHKYhynqDYHr24kFaoBWGW9ghzsTwMP'
The Gomme Ransomware runs as an executable file named 'gmm33.exe' on infected computers. The Gomme Ransomware demands a relatively small payment of $25 USDthat should be done using TOR. It is still uncertain whether the Gomme Ransomware has already been released in a full version or if it is still under development currently. However, computer users need to take precautions against threats like the Gomme Ransomware through the use of file backups, anti-malware software, and a reliable anti-spam component.
Dealing with a Gomme Ransomware Infection
If the Gomme Ransomware has encrypted your files, (or one of the many similar encryption ransomware Trojans that are active currently), PC security researchers advise the use of file backups to restore the affected files. Backup copies of files removable memory devices or the cloud, provide the users with the power to restore their files easily after removing the Gomme Ransomware with the help of a reliable security program that is fully up-to- date. If computer users can restore their files easily, then the people responsible for the Gomme Ransomware attack will not have grounds to demand a ransom payment.
SpyHunter Detects & Remove Gomme Ransomware
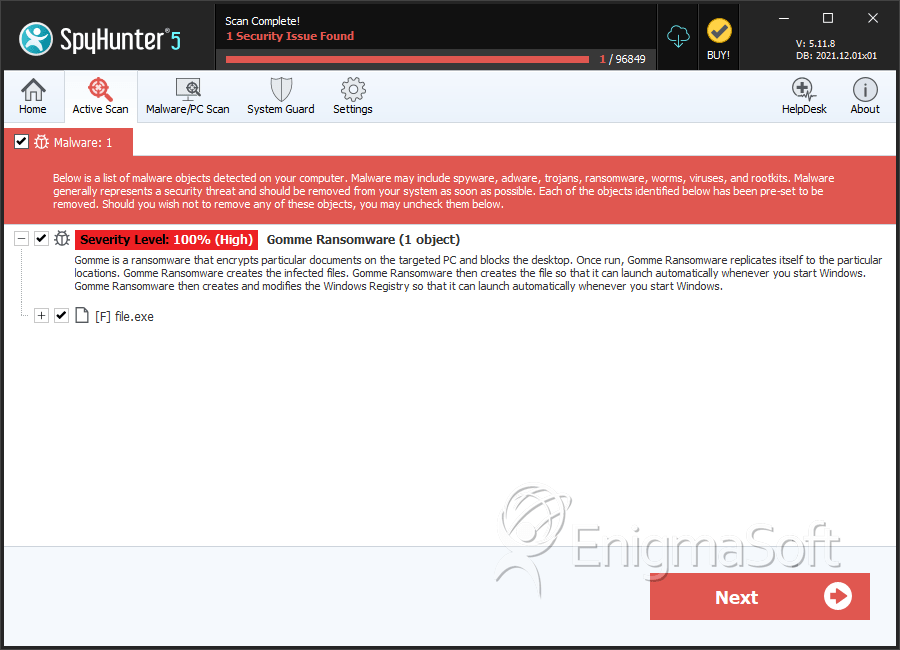
File System Details
| # | File Name | MD5 |
Detections
Detections: The number of confirmed and suspected cases of a particular threat detected on
infected computers as reported by SpyHunter.
|
|---|---|---|---|
| 1. | file.exe | cb24b3c809514b66f56779e2097aa6b9 | 0 |


Submit Comment
Please DO NOT use this comment system for support or billing questions. For SpyHunter technical support requests, please contact our technical support team directly by opening a customer support ticket via your SpyHunter. For billing issues, please refer to our "Billing Questions or Problems?" page. For general inquiries (complaints, legal, press, marketing, copyright), visit our "Inquiries and Feedback" page.